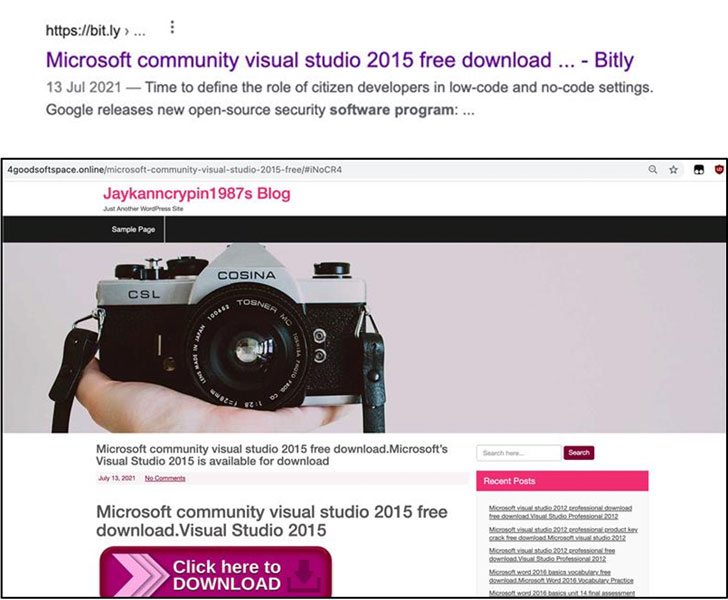
An ongoing search engine optimization (SEO) poisoning attack campaign has been observed abusing trust in legitimate software utilities to trick users into downloading BATLOADER malware on compromised machines.
“The threat actor used ‘free productivity apps installation’ or ‘free software development tools installation’ themes as SEO keywords to lure victims to a compromised website and to download a malicious installer,” researchers from Mandiant said in a report published this week.
In SEO poisoning attacks, adversaries artificially increase the search engine ranking of websites (genuine or otherwise) hosting their malware to make them show up on top of search results so that users searching for specific apps like TeamViewer, Visual Studio, and Zoom are infected with malware.
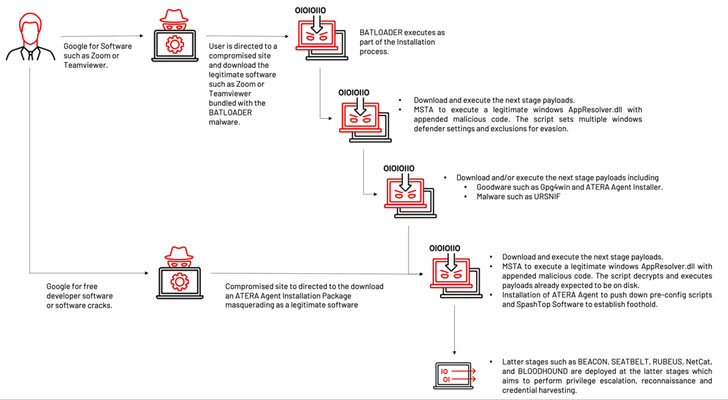
The installer, while packing the legitimate software, is also bundled with the BATLOADER payload that’s executed during the installation process. The malware then acts as a stepping stone for gaining further insight into the targeted organization by downloading next-stage executables that propagate the multi-stage infection chain.
One of those executables is a tampered version of an internal component of Microsoft Windows that’s appended with a malicious VBScript. The attack subsequently leverages a technique called signed binary proxy execution to run the DLL file using the legitimate “Mshta.exe” utility.
This results in the execution of the VBScript code, effectively triggering the next phase of the attack wherein additional payloads such as Atera Agent, Cobalt Strike Beacon, and Ursnif are delivered in the later stages to help perform remote reconnaissance, privilege escalation, and credential harvesting.
What’s more, in a sign that the operators experimented with different ploys, an alternative variant of the same campaign delivered the Atera remote monitoring management software directly as a consequence of the initial compromise for further follow-on post-exploitation activities.
Mandiant also called out the attacks’ overlaps with that of techniques adopted by the Conti ransomware gang, which were publicized in August 2021. “At this time, due to the public release of this information, other unaffiliated actors may be replicating the techniques for their own motives and objectives,” the researchers said.