The cyberattack aimed at Viasat that temporarily knocked KA-SAT modems offline on February 24, 2022, the same day Russian military forces invaded Ukraine, is believed to have been the consequence of wiper malware, according to the latest research from SentinelOne.
The findings come as the U.S. telecom company disclosed that it was the target of a multifaceted and deliberate” cyberattack against its KA-SAT network, linking it to a “ground-based network intrusion by an attacker exploiting a misconfiguration in a VPN appliance to gain remote access to the trusted management segment of the KA-SAT network.”
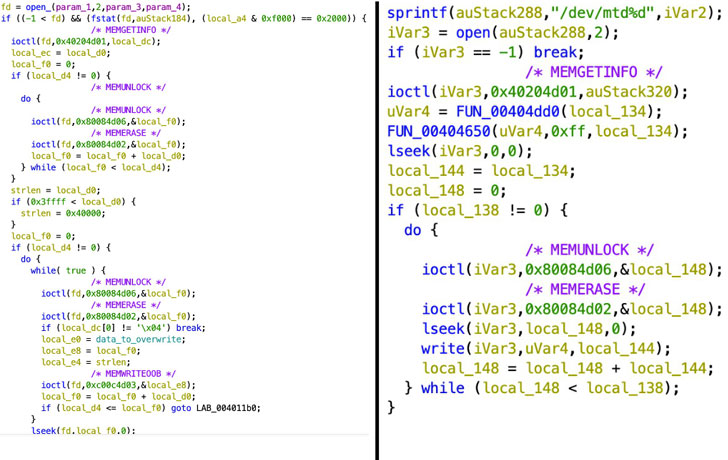
Upon gaining access, the adversary issued “destructive commands” on tens of thousands of modems belonging to the satellite broadband service that “overwrote key data in flash memory on the modems, rendering the modems unable to access the network, but not permanently unusable.”
But SentinelOne said it uncovered a new piece of malware on March 15 that casts the entire incident in a fresh light – a supply chain compromise of the KA-SAT management mechanism to deliver the wiper, dubbed AcidRain, to the modems and routers and achieve scalable disruption.
AcidRain is fashioned as a 32-bit MIPS ELF executable that “performs an in-depth wipe of the filesystem and various known storage device files,” researchers Juan Andres Guerrero-Saade and Max van Amerongen said. “If the code is running as root, AcidRain performs an initial recursive overwrite and delete of non-standard files in the filesystem.”
Once the wiping process is complete, the device is rebooted to render it inoperable. This makes AcidRain the seventh wiper strain to be uncovered since the start of the year in connection with the Russo-Ukrainian war after WhisperGate, WhisperKill, HermeticWiper, IsaacWiper, CaddyWiper, and DoubleZero.
Further analysis of the wiper sample has also uncovered an “interesting” code overlap with a third stage plugin (“dstr”) used in attacks involving a malware family called VPNFilter, which has been attributed to the Russian Sandworm (aka Voodoo Bear) group.
In late February 2022, intelligence agencies from the U.K. and the U.S. revealed a successor to VPNFilter, calling the replacement framework Cyclops Blink.
That having said, it’s still unclear how the threat actors gained access to the VPN. In a statement shared with Ars Technica, Viasat confirmed that data destroying malware was indeed deployed on modems using “legitimate management” commands but has refrained from sharing further details citing an ongoing investigation.