Cybercriminals are impersonating popular crypto platforms such as Binance, Celo, and Trust Wallet with spoofed emails and fake login pages in an attempt to steal login details and deceptively transfer virtual funds.
“As cryptocurrency and non-fungible tokens (NFTs) become more mainstream, and capture headlines for their volatility, there is a greater likelihood of more individuals falling victim to fraud attempting to exploit people for digital currencies,” Proofpoint said in a new report.
“The rise and proliferation of cryptocurrency has also provided attackers with a new method of financial extraction.”
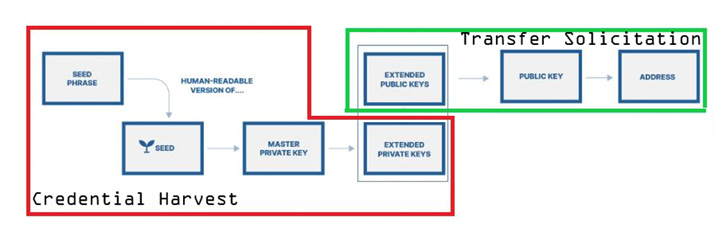
The targeting of sensitive cryptocurrency data by threat actors was recently echoed by the Microsoft 365 Defender Research Team, which warned about the emerging threat of cryware wherein private keys, seed phrases, and wallet addresses are plundered with the goal of siphoning virtual currencies by means of fraudulent transfers.
The swift popularity of Web3 in recent years has caused a shift in the phishing landscape, paving the way for a variety of social engineering and exploitation mechanisms that are aimed at stealing cryptocurrencies in different ways ranging from credential harvesting to the use of commodity stealer malware.
This includes spam emails that contain links to rogue URLs that download malware and redirect users to a credential harvesting landing page or even fake lookalike versions of NFT trading platforms like OpenSea. Other campaigns prompt potential victims to enter their seed phrases.
In a phishing attack detected by the enterprise security firm in February 2022, a Trust Wallet-themed lure was observed nudging email recipients, specifically university students, to verify their wallets by entering the recovery phrases.
A crucial enabler of these tailored campaigns is the relative ease with which counterfeit landing pages can be built using phishing kits, allowing less skilled threat actors to distribute and manage campaigns at a massive scale.
Further incentivizing the cybercriminal scheme are phishing-as-a-service (PHaaS) operators like BulletProofLink that offer phishing templates, spamming services, bulletproof hosting services, and credential collection services, among others.
The kits, which are continually updated and expanded, are designed to mimic different brands such as blockchain[.]com as well as other NFT and other cryptocurrency wallet service providers.
Also prominent are business email compromise (BEC) attempts to facilitate the fraudulent transfer of digital coins through messages that solicit cryptocurrency under the guise of vendor payments and donation requests to support the Ukraine war effort.
The findings come as losses from crypto-related crime jumped 79% year-over-year in 2021, with the U.S. Federal Trade Commission (FTC) noting that more than 46,000 people have reported losing over $1 billion in digital currencies to scams.
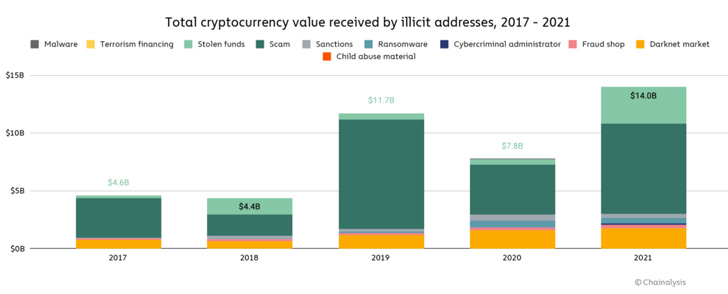
What’s more, Blockchain analytics firm Chainalysis found that cryptocurrency-based crime hit a new all-time high in 2021, even as illicit addresses received $14 billion over the course of the year, up from $7.8 billion in 2020.
“Cybercriminal threats to cryptocurrency are not new, however as the general public experiences growing adoption of cryptocurrency, people may be more likely to engage with social engineering lures using such themes,” Sherrod DeGrippo, vice president of threat research and detection at Proofpoint, said.
“Crypto went mainstream with Superbowl ads this year and threat actors have taken note of the opportunity for a quick payday. There is no easier method of financial extraction than the illicit transfer of cryptocurrency.”