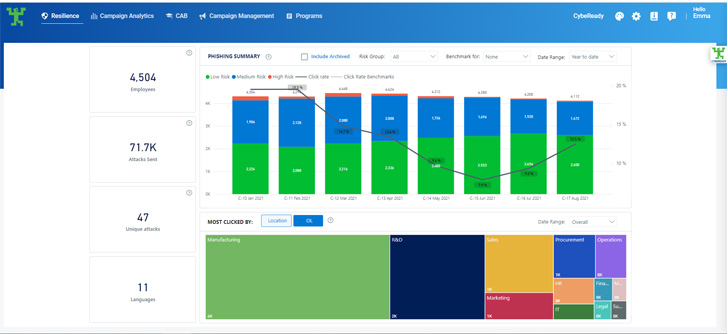
Phishing incidents are on the rise. A report from IBM shows that phishing was the most popular attack vector in 2021, resulting in one in five employees falling victim to phishing hacking techniques.
The Need for Security Awareness Training
Although technical solutions protect against phishing threats, no solution is 100% effective. Consequently, companies have no choice but to involve their employees in the fight against hackers. This is where security awareness training comes into play.
Security awareness training gives companies the confidence that their employees will execute the right response when they discover a phishing message in their inbox.
As the saying goes, “knowledge is power,” but the effectiveness of knowledge depends heavily on how it is delivered. When it comes to phishing attacks, simulations are among the most effective forms of training because the events in training simulations directly mimic how an employee would react in the event of an actual attack. Since employees do not know whether a suspicious email in their inbox is a simulation or a real threat, the training becomes even more valuable.
Phishing Simulations: What does the training include?
It is critical to plan, implement and evaluate a cyber awareness training program to ensure it truly changes employee behavior. However, for this effort to be successful, it should involve much more than just emailing employees. Key practices to consider include:
- Real-life phishing simulations.
- Adaptive learning – live response and protection from actual cyberattacks.
- Personalized training based on factors such as department, tenure, and cyber experience level.
- Empowering and equipping employees with an always-on cybersecurity mindset.
- Data-driven campaigns
Because employees do not recognize the difference between phishing simulations and real cyberattacks, it’s important to remember that phishing simulations evoke different emotions and reactions, so awareness training should be conducted thoughtfully. As organizations need to engage their employees to combat the ever-increasing attacks and protect their assets, it is important to keep morale high and create a positive culture of cyber hygiene.
Three common phishing simulation mistakes.
Based on years of experience, cybersecurity firm CybeReady has seen companies fall into these common mistakes.
1 — Testing instead of educating
The approach of running a phishing simulation as a test to catch and punish “repeat offenders” can do more harm than good.
An educational experience that involves stress is counterproductive and even traumatic. As a result, employees will not go through the training but look for ways to circumvent the system. Overall, the fear-based “audit approach” is not beneficial to the organization in the long run because it cannot provide the necessary training over an extended period.
Solution #1: Be sensitive
Because maintaining positive employee morale is critical to the organization’s well-being, provide positive just-in-time training.
Just-in-time training means that once employees have clicked on a link within the simulated attack, they are directed to a short and concise training session. The idea is to quickly educate the employee on their mistake and give them essential tips on spotting malicious emails in the future.
This is also an opportunity for positive reinforcement, so be sure to keep the training short, concise, and positive.
Solution #2: Inform relevant departments.
Communicate with relevant stakeholders to ensure they are aware of ongoing phishing simulation training. Many organizations forget to inform relevant stakeholders, such as HR or other employees, that the simulations are being conducted. Learning has the best effect when participants have the opportunity to feel supported, make mistakes, and correct them.
2 — Use the same simulation for all employees
It is important to vary the simulations. Sending the same simulation to all employees, especially at the same time, is not only not instructive but also has no valid metrics when it comes to organizational risk.
The “warning effect” – the first employee to discover or fall for the simulation warns the others. This prepares your employees to respond to the “threat” by anticipating the simulation, thus bypassing the simulation and the training opportunity.
Another negative impact is social desirability bias, which causes employees to over-report incidents to IT without noticing them in order to be viewed more favorably. This leads to an overloaded system and the department IT.
This form of simulation also leads to inaccurate results, such as unrealistically low click-through rates and over-reporting rates. Thus, the metrics do not show the real risks of the company or the problems that need to be addressed.
Solution: Drip mode
Drip mode allows sending multiple simulations to different employees at different times. Certain software solutions can even do this automatically by sending a variety of simulations to different groups of employees. It’s also important to implement a continuous cycle to ensure that all new employees are properly onboarded and to reinforce that security is important 24/7 – not just checking a box for minimum compliance.
3 — Relying on data from a single campaign
With over 3.4 billion phishing attacks per day, it’s safe to assume that at least a million of them differ in complexity, language, approach, or even tactics.
Unfortunately, no single phishing simulation can accurately reflect an organization’s risk. Relying on a single phishing simulation result is unlikely to provide reliable results or comprehensive training.
Another important consideration is that different groups of employees respond differently to threats, not only because of their vigilance, training, position, tenure, or even education level but because the response to phishing attacks is also contextual.
Solution: Implement a variety of training programs
Behavior change is an evolutionary process and should therefore be measured over time. Each training session contributes to the progress of the training. Training effectiveness, or in other words, an accurate reflection of actual organizational behavior change, can be determined after multiple training sessions and over time.
The most effective solution is to continuously conduct various training programs (at least once a month) with multiple simulations.
It is highly recommended to train employees according to their risk level. A diverse and comprehensive simulation program also provides reliable measurement data based on systematic behavior over time. To validate their efforts at effective training, organizations should be able to obtain a valid indication of their risk at any given point in time while monitoring progress in risk reduction.
Implement an effective phishing simulation program.
Creating such a program may seem overwhelming and time-consuming. That’s why we have created a playbook of the 10 key practices you can use to create a simple and effective phishing simulation. Simply download the CybeReady Playbook or meet with one of our experts for a product demo and learn how CybeReady’s fully automated security awareness training platform can help your organization achieve the fastest results with virtually zero effort IT.