Endpoint devices like desktops, laptops, and mobile phones enable users to connect to enterprise networks and use their resources for their day-to-day work. However, they also expand the attack surface and make the organisation vulnerable to malicious cyberattacks and data breaches.
Why Modern Organisations Need EDR
According to the 2020 global risk report by Ponemon Institute, smartphones, laptops, mobile devices, and desktops are some of the most vulnerable entry points that allow threat actors to compromise enterprise networks. Security teams must assess and address the security risks created by these devices before they can damage the organisation. And for this, they require Endpoint Detection & Response (EDR).
EDR solutions provide real-time visibility into endpoints and detect threats like malware and ransomware. By continuously monitoring endpoints, they enable security teams to uncover malicious activities, investigate threats, and initiate appropriate responses to protect the organisation.
The Limitations of EDR
Modern enterprise networks are complex webs of users, endpoints, applications, and data flows distributed across on-premises and multi-cloud environments. As EDR solutions only provide visibility into endpoints, many security gaps and challenges remain, significantly increasing the risk of cyberattacks going unnoticed.
- Malware disabling/abusing EDR agents: The emergence of sophisticated hacker groups like Lapsus$ is another risk that EDR tools can’t deal with. In late 2021, Lapsus$ hacked into several large companies by compromising remote endpoints and turning off their EDR tools. They were thus able to hide their malicious behaviour on the infected endpoints and achieve their goal of stealing sensitive company data. Another problem is that threat actors can abuse the “hooking” technique that EDRs use to monitor running processes. This technique enables EDR tools to monitor programs, detect suspicious activities, and gather data for behaviour-based analytics. However, this same process allows attackers to access a remote endpoint and import malware.
- BYOD: In recent years, many organisations have shifted to remote work models that allow employees and third-party users to access enterprise resources via remote networks and unsecured mobile devices. These devices are outside the control of security teams and their EDR tools. Consequently, their security solutions cannot keep up with all these endpoints, much less protect them or the enterprise network from malicious attacks.
- Unsupported devices: Also, not every connected endpoint can support EDR agents. This is true for legacy endpoints like routers and switches, as well as newer IoT devices. Further, with connected Supervisory Control and Data Acquisition (SCADA) and Industrial Control System (ICS) environments, some endpoints may be outside the organisation’s control and thus outside the EDR’s security perimeter. Consequently, these endpoints and systems remain vulnerable to threats like malware, DDoS attacks, and crypto mining.
- Maintaining/deploying EDR: Finally, with agent based EDR products, it can be a huge burden for security teams to install and maintain agents on every endpoint across the enterprise network environment.
Closing EDR’s Security Gaps with Network Visibility and NDR
One of the most effective ways to close the security gaps highlighted above is by adding Network Detection and Response (NDR) to the enterprise cybersecurity stack for the following reasons:
- Cannot disable NDR: As a log data based NDR such as ExeonTrace collects data from multiple different data sources in the network (and does not rely on specific devices), the detection algorithms cannot be circumvented. Therefore, even if an EDR is disabled by malware, the NDR will detect it.
- Identification of shadow IT: An NDR solution not only allows to monitor the network traffic between known network devices but also identifies and monitors yet unknown devices and networks. And of course, also endpoints without EDR agents are included in the network analytics (such as BYOD).
- Misconfigured firewalls and gateways: Unproper configured firewalls and gateways can be entry doors for attackers – an NDR allows for detection before exploitation.
- Tamper-proof data collection: Network-based data collection is more tamper-proof than agent-based data; ideal for digital forensics required by regulators.
- Complete visibility of the whole network: As no agents are required, an NDR solution such as ExeonTrace allows for complete visibility of all network connections and data flows. It thus provides greater visibility across the entire enterprise network and any potential threats across it.
Conclusion
As organisations become increasingly complex and add more end-user devices to their networks, they require a reliable monitoring solution to protect their endpoints from potential threats. However, Endpoint Detection and Response (EDR) provides such endpoint protection only to a certain extent. There are numerous drawbacks of EDR that allow sophisticated cybercriminals to surpass their security perimeter and exploit network vulnerabilities.
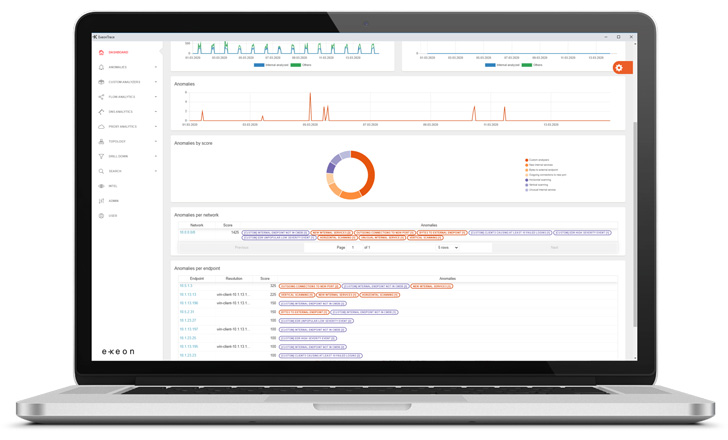 |
| ExeonTrace Platform: Screenshot of Dashboard |
To fill the security gaps left by EDR solutions, organisations must reinforce their security defences. Network Detection and Response (NDR) solutions like ExeonTrace are a reliable and proven way to monitor network traffic and thus complete enterprise cybersecurity stacks. As EDR and NDR solutions are complementary, their combined detection capabilities can effectively protect organisations from sophisticated cyberattacks.
Book a free demo to discover how ExeonTrace can help address your security challenges and make your organisation more cyber resilient.