SideWinder, a prolific nation-state actor mainly known for targeting Pakistan military entities, compromised the official website of the National Electric Power Regulatory Authority (NEPRA) to deliver a tailored malware called WarHawk.
“The newly discovered WarHawk backdoor contains various malicious modules that deliver Cobalt Strike, incorporating new TTPs such as KernelCallBackTable injection and Pakistan Standard Time zone check in order to ensure a victorious campaign,” Zscaler ThreatLabz said.
The threat group, also called APT-C-17, Rattlesnake, and Razor Tiger, is suspected to be an Indian state-sponsored group, although a report from Kaspersky earlier this May acknowledged previous indicators that led to the attribution have since disappeared, making it challenging it to link the threat cluster to a specific nation.
More than 1,000 attacks are said to have been launched by the group since April 2020, an indication of SideWinder’s newfound aggression since it commenced operations a decade ago in 2012.
The intrusions have been significant not only with regard to their frequency but also in their persistence, even as the group takes advantage of a massive arsenal of obfuscated and newly-developed components.
In June 2022, the threat actor was found leveraging an AntiBot script that’s designed to filter their victims to check the client browser environment, specifically the IP address, to ensure the targets are located in Pakistan.
The September campaign spotted by Zscaler entails the use of a weaponized ISO file hosted on NEPRA’s website to activate a killchain that leads to the deployment of the WarHawk malware, with the artifact also acting as a decoy to hide the malicious activity by displaying a legitimate advisory issued by the Cabinet Division of Pakistan on July 27, 2022.
WarHawk, for its part, masquerades as legitimate apps such as ASUS Update Setup and Realtek HD Audio Manager to lure unsuspecting victims into execution, resulting the exfiltration of system metadata to a hard-coded remote server, while also receiving additional payloads from the URL.
This includes a command execution module that’s responsible for the execution of system commands on the infected machine received from the command-and-control server, a file manager module that recursively enumerates files present in different drives, and an upload module that transmits files of interest to the server.
Also deployed as a second-stage payload using the aforementioned command execution module is a Cobalt Strike Loader, which validates the host’s time zone to confirm it matches the Pakistan Standard Time (PKT), failing which the process is terminated.
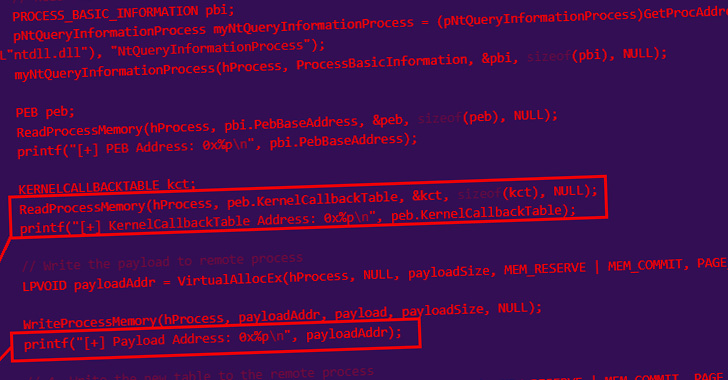
Should all the anti-analysis checks successfully pass, the loader injects shellcode into a notepad.exe process using a technique called KernelCallbackTable process injection, with the malware authors lifting source code from a technical write-up published in April 2022 by a researcher who goes by the online alias Capt. Meelo.
The shellcode then decrypts and loads Beacon, the default malware payload used by Cobalt Strike to establish a connection to its command-and-control server.
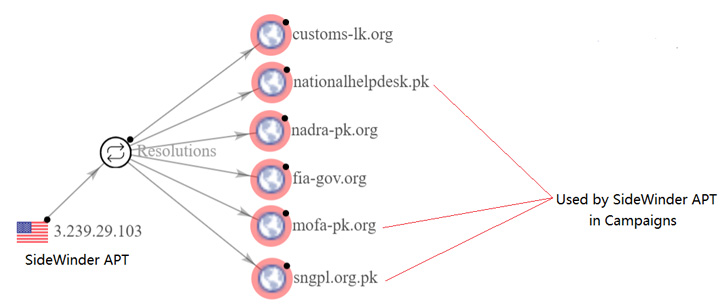
Per the cybersecurity company, the attack campaign’s connections to the SideWinder APT stem from the reuse of network infrastructure that has been identified as used by the group in prior espionage-focused activities against Pakistan.
“The SideWinder APT Group is continuously evolving their tactics and adding new malware to their arsenal in order to carry out successful espionage attack campaigns against their targets,” the researchers concluded.