Critical infrastructure is important for societal existence, growth, and development. Societies are reliant on the services provided by critical infrastructure sectors like telecommunication, energy, healthcare, transportation, and information technology. Safety and security are necessary for the optimal operation of these critical infrastructures. Critical infrastructure is made up of digital and non-digital assets. Organizations must stay ahead of cybersecurity threats to prevent failures caused by cyber attacks on critical infrastructure. Finding ways to protect digital assets in an ever-changing landscape filled with threats is a continuous activity. Organizations must also employ efficient security solutions and best practices to stay protected and reduce the chances of compromise.
Security solutions help secure and improve the visibility of an organization’s threat landscape. Different solutions use different concepts and approaches. An important concept that has risen recently is Extended Detection and Response (XDR).
XDR solutions provide detection and response capabilities across multiple layers. XDR tools correlate data using threat detection and response methods by gathering logs and events from various sources, such as network devices, servers, and applications. These capabilities make it possible for security teams to quickly detect, investigate and respond to incidents.
Attacks on critical infrastructure
In February 2022, a supply chain attack occurred in one of Germany’s energy giants. This attack led to the closure of more than 200 gas stations across Germany, affecting lives and businesses. This event occurred nearly a year after the Colonial Pipeline attack in the United States of America, where data exfiltration occurred and a ransomware infection shut down digital services within their infrastructure for days. An article from the NYTimes reported that an estimated 5 million dollars were paid to the hackers involved in the Colonial Pipeline ransomware attack. The hackers in the Colonial Pipeline case were able to gain entry using a compromised VPN password, and they proceeded to perform intrusion activities for an entire day before they were detected.
There are several entry points for attacks on critical infrastructure, and some vectors are more prevalent than others. These vectors include compromised credentials, unpatched operating systems, vulnerable applications, and malware delivered through various techniques.
Emphasis should be placed on securing critical infrastructure before an attack happens, regardless of how it originates. Security solutions help organizations protect themselves from different attack vectors. These solutions include XDR, SIEM, code scanners, infrastructure analyzers, vulnerability scanners, and malware detection solutions. In addition to these solutions are compliance standards. A few recommended standards are NIST, PCI DSS, HIPAA, and GDPR. The correct application of these solutions and compliance standards can help improve an organization’s security posture.
How XDR can mitigate attacks
An XDR plays a significant role in situations where threat actors target different digital assets of an organization. With an XDR integrated into an organization’s infrastructure, security events from various sources and assets are analyzed and correlated to determine what activities are happening in the infrastructure. An XDR has the ability to detect and provide automated responses to malicious activities in an environment. Such a response can kill a malicious process, delete a malicious file, or isolate a compromised endpoint. As the responses are executed in near real-time, speed plays a critical role in the execution of these tasks.
Wazuh SIEM/XDR
Wazuh is a free and open source SIEM and XDR platform. It includes several components that protect both cloud and on-premises workloads. The Wazuh platform operates with an agent-server model. The Wazuh central components (server, indexer, and dashboard) analyze security data from endpoints in your infrastructure. At the same time, the Wazuh agent is deployed on endpoints to collect security data and provide threat detection and response. The Wazuh agent is lightweight and supports multiple platforms. Wazuh also supports agentless monitoring on routers, firewalls, and switches.
Wazuh XDR capabilities
Wazuh has several capabilities that help an organization stay ahead of security threats. Some of these capabilities are malware detection, vulnerability detection, file integrity monitoring, and automated response to threats, amongst others. The following sections contain more details on Wazuh capabilities that help in protecting critical infrastructure.
Log data analysis
The Wazuh log data analysis module collects and analyzes security data from various sources. Such data include system event logs, application logs, and abnormal system behavior logs. Consequently, the analyzed data is used for threat detection and automated response. This capability gives you visibility into events happening at different endpoints in your infrastructure.
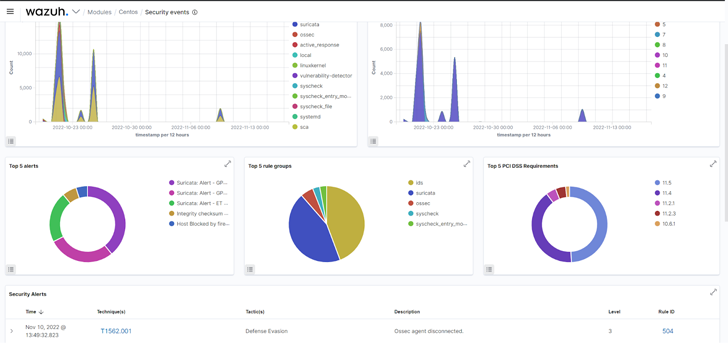 |
| Fig 1: Security events of a monitored endpoint on the Wazuh dashboard. |
Malware detection
Wazuh has several features that help in malware detection. In addition, Wazuh can be integrated with other security tools like YARA and VirusTotal to detect malware. By properly configuring Wazuh Constant Database (CDB) lists, values from decoded alerts such as users, file hashes, IP addresses, or domain names can be compared with malicious records. Here is a blog post that shows how Wazuh can be integrated with CDB lists for detecting and responding to malicious files. This Wazuh capability helps you detect malware on various monitored endpoints.
File integrity monitoring
The Wazuh File Integrity Monitoring (FIM) module monitors an endpoint filesystem to detect changes in predefined files and directories. Alerts are triggered when a file is created, modified, or deleted in monitored directories. You can see how this module is utilized to detect changes to an SSH key file in the blog post Detecting illegitimate crypto miners on Linux endpoints. Using the Wazuh FIM module, you can detect changes to configuration files on critical systems and determine if the activity is authorized or malicious.
Vulnerability detection
Wazuh uses the Vulnerability detector module to find vulnerabilities on a monitored endpoint. Vulnerability detection works by performing software audits. These audits are made possible by leveraging vulnerability feeds indexed from sources like Canonical, Debian, Red Hat, Arch Linux, ALAS (Amazon Linux Advisories Security), Microsoft, and the National Vulnerability Database. These feeds are cross-correlated by Wazuh with information from the endpoint’s application inventory. Administrators should commence remediation immediately after vulnerabilities are detected before malicious actors can exploit them.
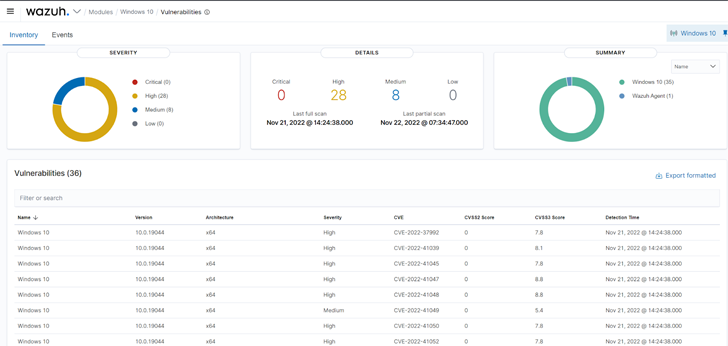 |
| Fig 2: The Wazuh vulnerability detection dashboard. |
Automated response to threats
The Wazuh active response module can be configured to automatically execute countermeasures when events match specific criteria. It can execute user-defined actions, such as a firewall block or drop, traffic shaping or throttling, account lockout, system shutdown, etc. The active response module was configured to deny network connection from an identified malicious source in the blog post Responding to network attacks with Suricata and Wazuh XDR.
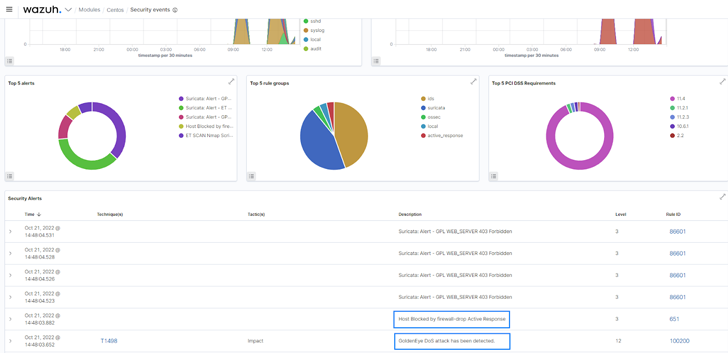 |
| Fig 3: The Wazuh active response mitigating a DoS attack. |
Conclusion
Implementing security across multiple layers of critical infrastructure reduces an organization’s attack surface. We have emphasized a few factors to keep in mind to maintain a proper security posture. In protecting your digital assets, we suggest a solution that works well with various endpoints, systems, and technologies.
Wazuh is a free and open source XDR solution. It includes the capabilities necessary to discover vulnerabilities, determine the system configuration state, and respond to threats on your digital assets. Wazuh also provides support for compliance standards like PCI DSS, HIPAA, NIST, and GDPR. Wazuh has an ever-growing community where support is provided to users. Check out the Wazuh documentation for more information.
