Managing vulnerabilities in the constantly evolving technological landscape is a difficult task. Although vulnerabilities emerge regularly, not all vulnerabilities present the same level of risk. Traditional metrics such as CVSS score or the number of vulnerabilities are insufficient for effective vulnerability management as they lack business context, prioritization, and understanding of attackers’ opportunities. Vulnerabilities only represent a small part of the attack surface that attackers can leverage.
Initially, organizations used manual methods to address known security weaknesses, but as technology and cyber threats evolved, a more automated and comprehensive approach became necessary. However, legacy vulnerability management tools were designed primarily for compliance and modern tools still face challenges in prioritization and limited resources, especially in dynamic and agile cloud environments.
Modern vulnerability management integrates security tools such as scanners, threat intelligence, and remediation workflows to provide a more efficient and effective solution. Nevertheless, organizations continue to face challenges such as:
- A growing list of vulnerabilities
- Inaccurate prioritization
- Missing business context
- Misalignment of priorities and resources between IT and security teams
- Lack of coverage and a unified view of risk
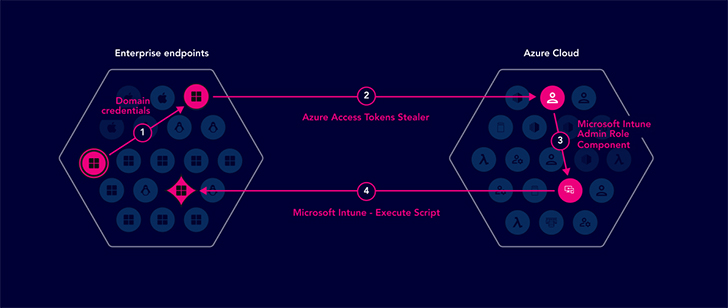
Exposures are broader than a typical CVE and can encompass more than just vulnerabilities. Exposures can result from various factors, such as human error, improperly defined security controls, and poorly designed and unsecured architecture. Many security tools tend to focus on specific types of exposures, such as vulnerabilities, misconfigurations, or identities, and address each one in isolation. However, this approach fails to consider how attackers view networks and systems. Attackers don’t look at the individual exposure – rather, they leverage the toxic combination of vulnerabilities, misconfigurations, overly permissive identities, and other security gaps to move across systems and reach sensitive assets. This route is called an attack path and this type of lateral movement can go undetected for weeks or months, allowing attackers to cause significant and ongoing damage while hiding inside networks.
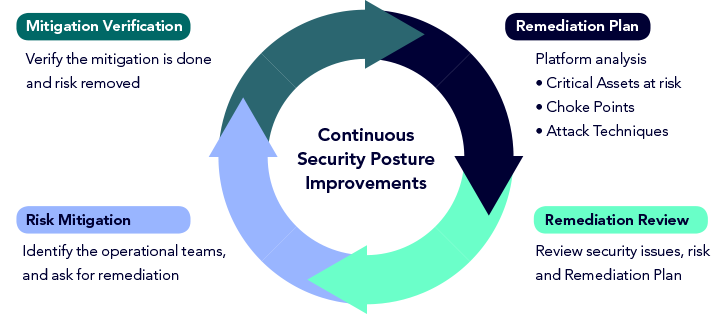
A modern exposure management program involves combining multiple exposures onto an attack graph to understand the relationship and context of risk towards critical assets. This allows for targeted remediation that reduces risk in the most cost-efficient manner. To build a modern exposure management program, organizations should recognize the evolution of threat actors and their tactics, establish an operational process for ensuring continuous security posture improvement, and implement a plan consisting of remediation planning, remediation review, risk mitigation and mitigation verification.
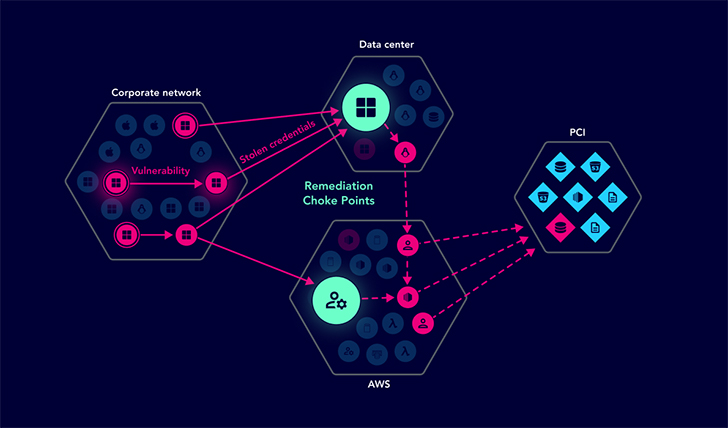
At XM Cyber, we believe that only by combining multiple exposures together onto an attack graph that visualizes all possible attack paths, can we understand the relationship and context of risk towards critical assets. And by understanding context, we can accurately prioritize issues to focus on the exposures that need remediating where they converge on choke points. This allows for productive remediation that reduces risk in the most cost-efficient manner.
The three key pillars to building a modern exposure management program are:
- Understanding exposure insights – continuously identify and monitor potential risks to critical assets, as well as identifying any gaps in security controls or deviations from compliance standards.
- Analyzing attack paths – create an attack graph view that visualizes all possible attack paths to critical assets.
- Prioritizing remediation efforts – focus on the most critical issues and choke points that require immediate attention to reduce risk exposure in a cost-efficient manner.
By combining these three pillars, organizations can build a comprehensive and effective exposure management program that helps to protect critical assets and reduce overall risk exposure. This allows for productive remediation that reduces risk in the most cost-efficient manner. By continuously analyzing and monitoring exposures, organizations can build a sustainable and scalable process for managing risk over time.
Note: This article is written and contributed by Michael A. Greenberg, Director of Product Marketing at XM Cyber.