A sophisticated stealer-as-a-ransomware threat dubbed RedEnergy has been spotted in the wild targeting energy utilities, oil, gas, telecom, and machinery sectors in Brazil and the Philippines through their LinkedIn pages.
The malware “possesses the ability to steal information from various browsers, enabling the exfiltration of sensitive data, while also incorporating different modules for carrying out ransomware activities,” Zscaler researchers Shatak Jain and Gurkirat Singh said in a recent analysis.
The goal, the researchers noted, is to couple data theft with encryption with the goal of inflicting maximum damage to the victims.
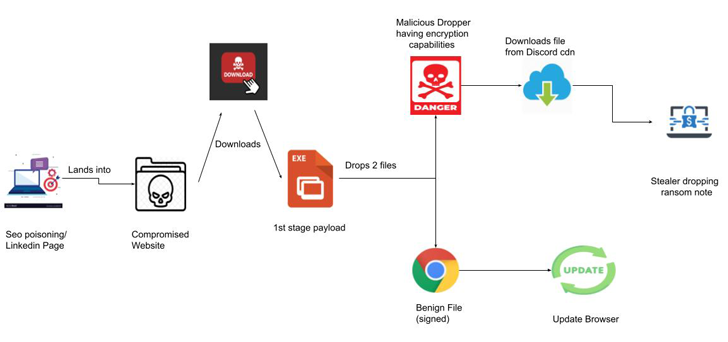
The starting point for the multi-stage attack is a FakeUpdates (aka SocGholish) campaign that tricks users into downloading JavaScript-based malware under the guise of web browser updates.
What makes it novel is the use of reputable LinkedIn pages to target victims, redirecting users clicking on the website URLs to a bogus landing page that prompts them to update their web browsers by clicking on the appropriate icon (Google Chrome, Microsoft Edge, Mozilla Firefox, or Opera), doing so which results in the download a malicious executable.
Following a successful breach, the malicious binary is used as a conduit to set up persistence, perform the actual browser update, and also drop a stealer capable of covertly harvesting sensitive information and encrypting the stolen files, leaving the victims at risk of potential data loss, exposure, or even the sale of their valuable data.
Zscaler said it discovered suspicious interactions taking place over a File Transfer Protocol (FTP) connection, raising the possibility that valuable data is being exfiltrated to actor-controlled infrastructure.
In the final stage, RedEnergy’s ransomware component proceeds to encrypt the user’s data, suffixing the “.FACKOFF!” extension to each encrypted file, deleting existing backups, and dropping a ransom note in each folder.
Victims are expected to make a payment of 0.005 BTC (about $151) to a cryptocurrency wallet mentioned in the note to regain access to the files. RedEnergy’s dual functions as a stealer and ransomware represent an evolution of the cybercrime landscape.
The development also follows the emergence of a new RAT-as-a-ransomware threat category in which remote access trojans such as Venom RAT and Anarchy Panel RAT have been equipped with ransomware modules to lock various file extensions behind encryption barriers.
“It is crucial for individuals and organizations to exercise utmost caution when accessing websites, especially those linked from LinkedIn profiles,” the researchers said. “Vigilance in verifying the authenticity of browser updates and being wary of unexpected file downloads is paramount to protect against such malicious campaigns.”