Cybersecurity researchers have disclosed that the LightSpy spyware recently identified as targeting Apple iOS users is in fact a previously undocumented macOS variant of the implant.
The findings come from both Huntress Labs and ThreatFabric, which separately analyzed the artifacts associated with the cross-platform malware framework that likely possesses capabilities to infect Android, iOS, Windows, macOS, Linux, and routers from NETGEAR, Linksys, and ASUS.
“The Threat actor group used two publicly available exploits (CVE-2018-4233, CVE-2018-4404) to deliver implants for macOS,” ThreatFabric said in a report published last week. “Part of the CVE-2018-4404 exploit is likely borrowed from the Metasploit framework. macOS version 10 was targeted using those exploits.”
LightSpy was first publicly reported in 2020, although subsequent reports from Lookout and the Dutch mobile security firm have revealed possible connections between the spyware and an Android surveillance tool called DragonEgg.
Earlier this April, BlackBerry disclosed what it said was a “renewed” cyber espionage campaign targeting users in South Asia to deliver an iOS version of LightSpy. But this has now been found to be a much more refined macOS version that employs a plugin-based system to harvest various kinds of information.
“It’s also worth noting that while this sample was uploaded to VirusTotal recently from India, this isn’t a particularly strong indicator of an active campaign, nor targeting within the region,” Huntress researchers Stuart Ashenbrenner and Alden Schmidt said.
“It’s a contributing factor, but without more concrete evidence or visibility into delivery mechanisms, it should be taken with a heavy grain of salt.”
ThreatFabric’s analysis has revealed that the macOS flavor has been active in the wild since at least January 2024, but confined to just about 20 devices, a majority of which are said to be test devices.
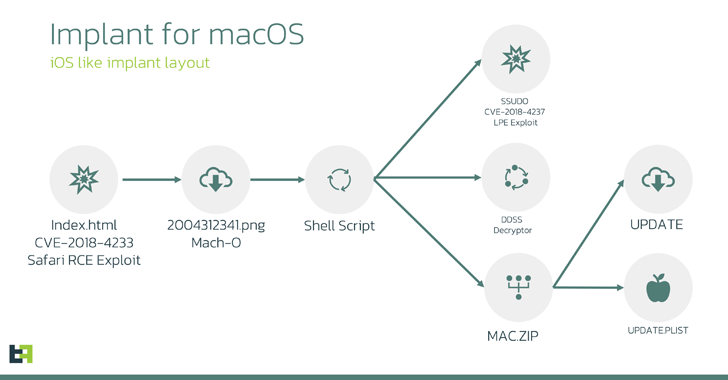
The attack chain begins with the exploitation of CVE-2018-4233, a Safari WebKit flaw, via rogue HTML pages to trigger code execution, leading to the delivery of a 64-bit Mach-O binary that masquerades as a PNG image file.
The binary is primarily designed to extract and launch a shell script that, in turn, fetches three additional payloads: A privilege escalation exploit, an encryption/decryption utility, and a ZIP archive.
The script subsequently extracts the contents of the ZIP archive — update and update.plist — and assigns root privileges to both of them. The information property list (plist) file is used to set up persistence for the other file such that it’s launched every time after a system restart.
The “update” file (aka macircloader) acts as a loader for the LightSpy Core component, allowing the latter to establish contact with a command-and-control (C2) server and retrieve commands as well as download plugins.
The macOS version comes with support for 10 different plugins to capture audio from the microphone, take photos, record screen activity, harvest and delete files, execute shell commands, grab the list of installed applications and running processes, and extract data from web browsers (Safari and Google Chrome) and iCloud Keychain.
Two other plugins further make it possible to capture information about all the other devices that are connected to the same network as the victim, the list of Wi-Fi networks the device has connected to, and details about the nearby Wi-Fi networks.
“The Core serves as a command dispatcher and additional plugins extend the functionality,” ThreatFabric noted. “Both the Core and plugins could be updated dynamically by a command from C2.”
The cybersecurity firm said it was able to find a misconfiguration that made it possible to gain access to the C2 panel, including a remote control platform, which contains information about the victims and the associated data.
“Regardless of the targeted platform, the threat actor group focused on intercepting victim communications, such as messenger conversations and voice recordings,” the company said. “For macOS, a specialized plugin was designed for network discovery, aiming to identify devices in proximity to the victim.”
The development comes as Android devices have been targeted with known banking trojans such as BankBot and SpyNote in attacks aimed at mobile banking app users in Uzbekistan and Brazil, as well as by impersonating a Mexico telecom service provider to infect users in Latin America and the Caribbean.
It also comes as a report from Access Now and the Citizen Lab uncovered evidence of Pegasus spyware attacks targeting seven Russian and Belarusian-speaking opposition activists and independent media in Latvia, Lithuania, and Poland.
“The use of Pegasus spyware to target Russian- and Belarusian-speaking journalists and activists dates back until at least 2020, with more attacks following Russia’s full-scale invasion of Ukraine in February 2022,” Access Now said, adding “a single Pegasus spyware operator may be behind the targeting of at least three of the victims and possibly all five.”
Pegasus-maker NSO Group, in a statement shared with Meduza, said it cannot disclose information about specific customers but noted that it only sells its tools to countries that are allied with Israel and the U.S. It further said it will initiate an investigation subject to which it may suspend or terminate the service.