End-user passwords are one of the weakest components of your overall security protocols. Most users tend to reuse passwords across work and personal accounts.
They may also choose relatively weak passwords that satisfy company password policies but can be easily guessed or brute-forced. Your users may also inadvertently use breached passwords for their corporate account password.
The National Institute of Standards and Technology (NIST) has a cybersecurity framework that helps organizations address common cybersecurity pitfalls in their environment, including weak, reused, and breached passwords. This post will take a closer look at the NIST password guidelines and see how you can effectively audit your password policies to ensure these meet the standards recommended by NIST.
NIST Password Guidelines and Best Practices
Specific guidance around passwords is addressed within the chapter titled Memorized Secret Verifiers. NIST has several recommendations in regards to passwords:
- Passwords should be no less than eight characters in length
- ASCII characters are acceptable along with Spaces
- If a service provider randomly chooses passwords, these must be at least six characters in length
- Passwords should be compared against a list of known commonly-used, expected, or compromised passwords.
What types of passwords are commonly-used, expected, or compromised?
- Previously breached passwords
- Dictionary words
- Characters that are sequential or repetitive
- Context-specific words (including username, business name, etc.)
NIST also recommends the following other password security mechanisms, including:
- Rate-limiting failed login attempts,
- Not forcing users to change their password after an arbitrary number of days,
- Forcing a password change if there is evidence of a compromise of the account password (i.e., password exposed in a breach),
- Guidance should be offered to users as to specific password policy requirements.
Auditing Active Directory Password Policies
Most enterprise organizations today are using Microsoft Active Directory as their centralized identity source and access management solution. Many make use of the built-in Active Directory Password Policies provided by Group Policy. The built-in Password Policies as part of Group Policy Account Policies provide basic functionality to create password policies for your Active Directory environment.
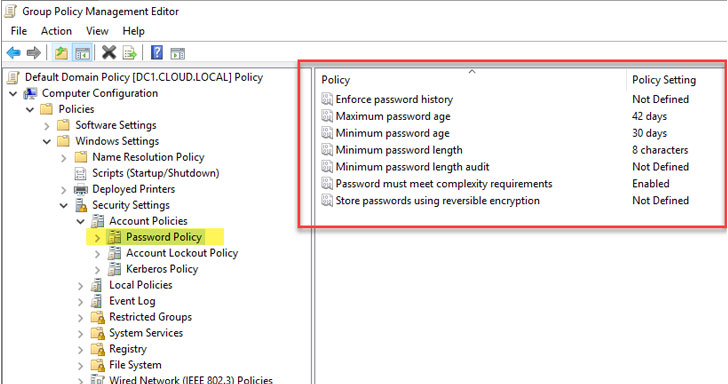
Below is an example of a Default Domain Policy configured with the default Password Policy settings, including:
- Maximum password age
- Minimum password age
- Minimum password length
- Password must meet complexity requirements
 |
| A Default Domain Policy Password Policy |
As you can see in the Password Policy properties, there are no built-in means to detect breached passwords or upload a password list file for custom dictionary purposes. According to NIST recommended password guidelines, this policy would not align with the NIST standard.
What if you have many different password policies with potentially many different password settings and configurations? How do you effectively audit your Active Directory Password Policies to see how they measure up to recommendations of NIST standards and others?
Specops Password Auditor – Visibility to NIST and other cybersecurity standards
What if you had a tool that provided visibility to all of your Active Directory Password Policies and how these measure up to leading industry standards? Specops Password Auditor is a robust tool that not only allows you to have quick visibility into dangerous passwords in your Active Directory environment. It also allows you to quickly audit existing password policies against top cybersecurity standards for compliance with these.
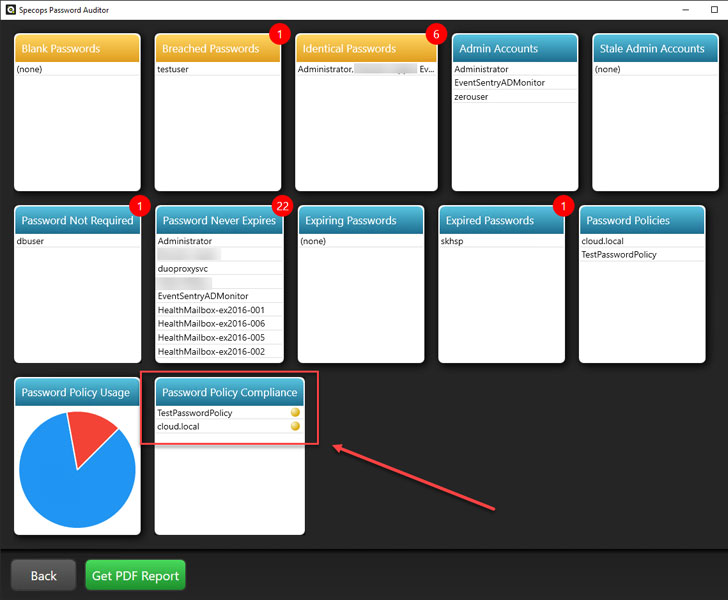
As you can see, the Specops Password Auditor tool enables you to have quick visibility to risky passwords in your organization’s Active Directory environment. These include:
- Blank Passwords
- Breached Passwords
- Identical Passwords
- Admin Accounts
- Stale Admin Accounts
- Password Not Required
- Password Never Expires
- Expiring Passwords
- Expired Passwords
- Password Policies
- Password Policy Usage
- Password Policy Compliance
 |
| Specops Password Auditor |
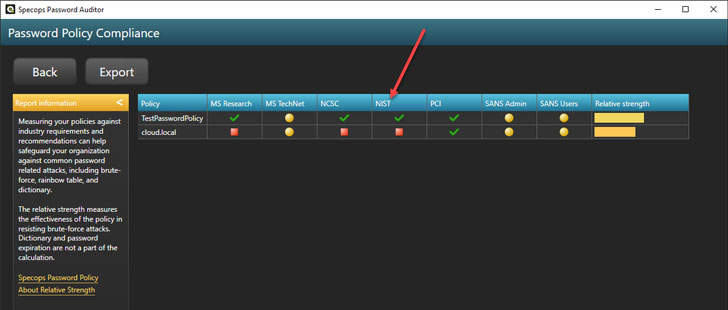
Specops Password Auditor’s Password Policy Compliance report compares the settings in your existing Active Directory Password Policies with the following standards:
- MS Research
- MS TechNet
- NCSC
- NIST
- PCI
- SANS Admin
- SANS Users
You can quickly see if your existing password policies meet the requirements recommended by the various cybersecurity standards. It offsets a tremendous burden from the IT or security administrator when performing audits to align security policies with different cybersecurity frameworks, like NIST. As you can see, the cloud.local policy does not comply with NIST.
 |
| Specops Password Auditor Password Policy Compliance report |
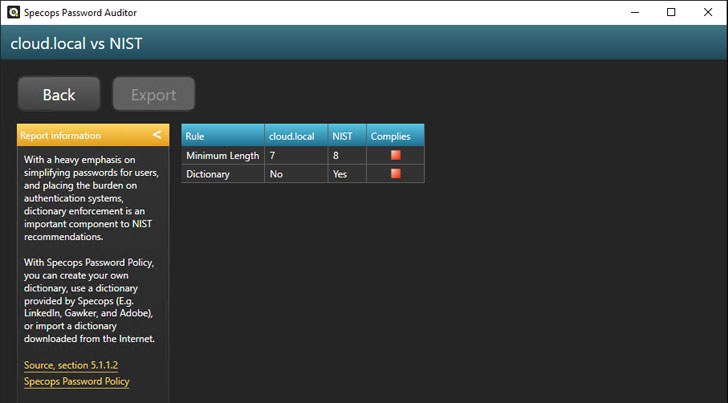
If you click the “red box” under NIST for the specific domain password policy, you will get a detailed look at why the policy fails to comply with the particular standard. We see that both the minimum length and Dictionary settings fail.
 |
| Comparing your password policy with the NIST standard |
Using Specops Password Auditor and Specops Password Policy
The Specops Password Auditor provides excellent visibility to how your Active Directory Password Policies stack up against industry-standard cybersecurity standards. Suppose you want to take this functionality to the next level. In that case, Specops Password Policy provides the ability to easily create password policies that are fully compliant with NIST and other cybersecurity frameworks.
Using Specops Password Policy, you can easily implement the more advanced components of your Active Directory Password Policies, including custom dictionary files and breached password protection.
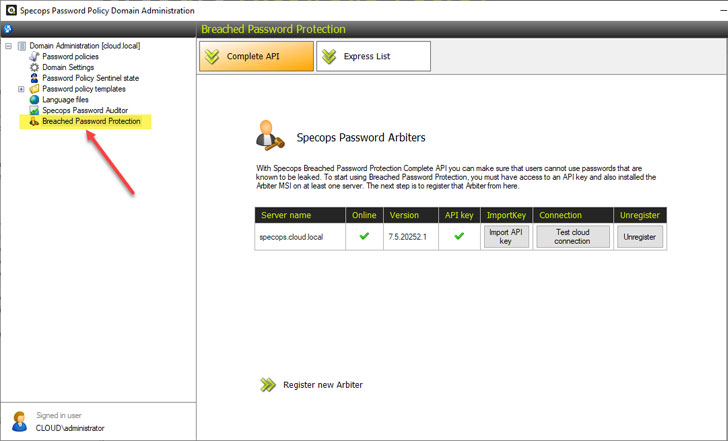 |
| Specops Password Policy Breached Password Protection |
Wrapping Up
Maintaining visibility and compliance in your Active Directory environment with recommended cybersecurity best practices such as NIST is a great way to bolster your environment’s security. NIST is a well-known industry standard cybersecurity framework that provides excellent guidance for password security.
Most businesses today are making use of Active Directory Password Policies in the environment. Performing audits of your password policies against the NIST standard helps to see any areas of your existing policies that may need to be revisited.
Specops Password Auditor makes this process extremely easy. It automatically pulls all the settings of existing password policies in the environment and compares these with industry-standard cybersecurity frameworks, like NIST. Specops Password Policy enables easily implementing NIST recommendations and others such as custom dictionaries and breached password protection.
