More details have emerged about a security feature bypass vulnerability in Windows NT LAN Manager (NTLM) that was addressed by Microsoft as part of its monthly Patch Tuesday updates earlier this month.
The flaw, tracked as CVE-2021-1678 (CVSS score 4.3), was described as a “remotely exploitable” flaw found in a vulnerable component bound to the network stack, although exact details of the flaw remained unknown.
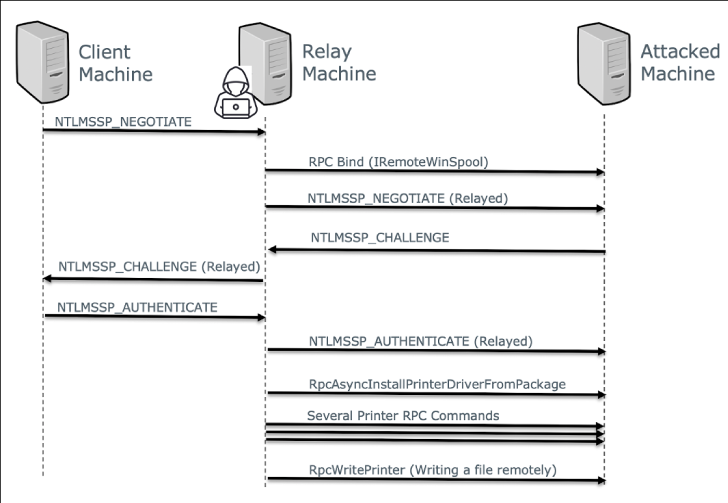
Now according to researchers from Crowdstrike, the security bug, if left unpatched, could allow a bad actor to achieve remote code execution via an NTLM relay.
“This vulnerability allows an attacker to relay NTLM authentication sessions to an attacked machine, and use a printer spooler MSRPC interface to remotely execute code on the attacked machine,” the researchers said in a Friday advisory.
NTLM relay attacks are a kind of man-in-the-middle (MitM) attacks that typically permit attackers with access to a network to intercept legitimate authentication traffic between a client and a server and relay these validated authentication requests in order to access network services.
Successful exploits could also allow an adversary to remotely run code on a Windows machine or move laterally on the network to critical systems such as servers hosting domain controllers by reusing the NTLM credentials directed at the compromised server.
While such attacks can be thwarted by SMB and LDAP signing and turning on Enhanced Protection for Authentication (EPA), CVE-2021-1678 exploits a weakness in MSRPC (Microsoft Remote Procedure Call) that makes it vulnerable to a relay attack.
Specifically, the researchers found that IRemoteWinspool — an RPC interface for remote printer spooler management — could be leveraged to execute a series of RPC operations and write arbitrary files on a target machine using an intercepted NTLM session.
Microsoft, in a support document, said it addressed the vulnerability by “increasing the RPC authentication level and introducing a new policy and registry key to allow customers to disable or enable Enforcement mode on the server-side to increase the authentication level.”
In addition to installing the January 12 Windows update, the company has urged organizations to turn on Enforcement mode on the print server, a setting which it says will be enabled on all Windows devices by default starting June 8, 2021.