Cybersecurity researchers have warned of a publicly available fully-functional exploit that could be used to target SAP enterprise software.
The exploit leverages a vulnerability, tracked as CVE-2020-6207, that stems from a missing authentication check in SAP Solution Manager (SolMan) version 7.2
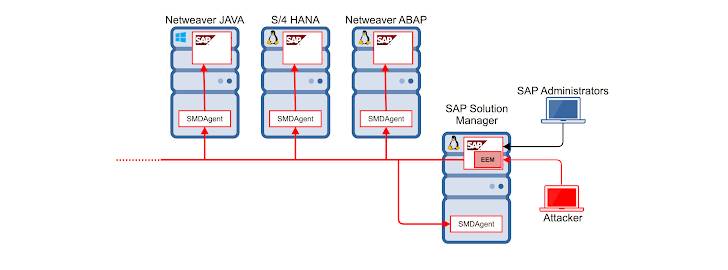
SAP SolMan is an application management and administration solution that offers end-to-end application lifecycle management in distributed environments, acting as a centralized hub for implementing and maintaining SAP systems such as ERP, CRM, HCM, SCM, BI, and others.
“A successful exploitation could allow a remote unauthenticated attacker to execute highly privileged administrative tasks in the connected SAP SMD Agents,” researchers from Onapsis said, referring to the Solution Manager Diagnostics toolset used to analyze and monitor SAP systems.
The vulnerability, which has the highest possible CVSS base score of 10.0, was addressed by SAP as part of its March 2020 updates.
Exploitation methods leveraging the flaw were later demonstrated at the Black Hat conference last August by Onasis researchers Pablo Artuso and Yvan Genuer to highlight possible attack techniques that could be devised by rogue parties to strike SAP servers and obtain root access.
The critical flaw resided in SolMan’s User Experience Monitoring (formerly End-user Experience Monitoring or EEM) component, thus putting every business system connected to the Solution Manager at risk of a potential compromise.
The public availability of a Proof-of-Concept (PoC) exploit code, therefore, leaves unpatched servers exposed to a number of potential malicious attacks, including:
- Shutting down any SAP system in the landscape
- Causing IT to control deficiencies impacting financial integrity and privacy, leading to regulatory compliance violations
- Deleting any data in the SAP systems, causing business disruptions
- Assigning superuser privileges to any existing or new user, allowing those users to run critical operations, and
- Reading sensitive data from the database
“While exploits are released regularly online, this hasn’t been the case for SAP vulnerabilities, for which publicly available exploits have been limited,” Onasis researchers said.
“The release of a public exploit significantly increases the chance of an attack attempt since it also expands potential attackers not only to SAP-experts or professionals, but also to script-kiddies or less-experienced attackers that can now leverage public tools instead of creating their own.”