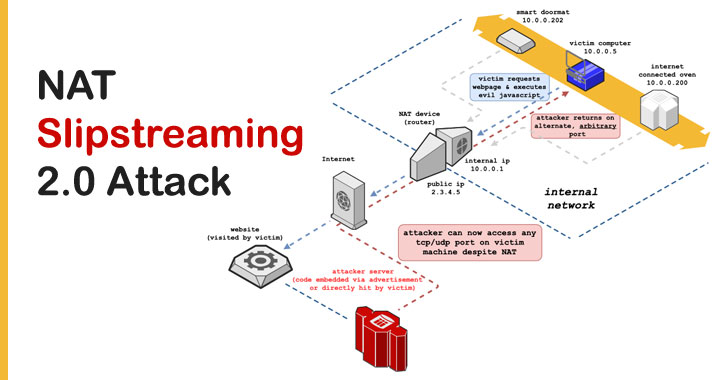
A newly devised variant of the NAT Slipstreaming attack can be leveraged to compromise and expose any device in an internal network, according to the latest research.
Detailed by enterprise IoT security firm Armis, the new attack (CVE-2020-16043 and CVE-2021-23961) builds on the previously disclosed technique to bypass routers and firewalls and reach any unmanaged device within the internal network from the Internet.
First disclosed by security researcher Samy Kamkar in late October 2020, the JavaScript-based attack relied on luring a user into visiting a malicious website to circumvent browser-based port restrictions and allow the attacker to remotely access TCP/UDP services on the victim’s device, even those that were protected by a firewall or NAT.
Although partial mitigations were released on November 11 to thwart the attack in Chrome 87, Firefox 84, and Safari by preventing connections on port 5060 or 5061, Armis researchers Ben Seri and Gregory Vishnipolsky revealed that “NAT Slipstreaming 2.0” puts “embedded, unmanaged, devices at greater risk, by allowing attackers to expose devices located on internal networks, directly to the Internet.”
Vulnerable devices that could be potentially exposed as a consequence of this attack include office printers, industrial controllers, IP cameras, and other unauthenticated interfaces that could be exploited once the NAT/firewall is tricked into opening network traffic to the victim device.
“Using the new variant of the NAT Slipstreaming attack to access these types of interfaces from the Internet, can result in attacks that range from a nuisance to a sophisticated ransomware threat,” the researchers said.
Google, Apple, Mozilla, and Microsoft have all released patches to Chrome (v87.0.4280.141), Safari (v14.0.3), Firefox (v85.0), and Edge (v87.0.664.75) browsers to address the new attack.
Using H.323 Packets to facilitate NAT Slipstreaming
Put simply, NAT Slipstreaming allows a bad actor to bypass NAT/firewall and remotely access any TCP/UDP service bound to a victim machine as a result of the target visiting a malware-infected website specially crafted for this purpose.
Particularly, the malicious JavaScript code running on the victim’s browser extracts the internal IP address and takes advantage of TCP/IP packet segmentation to create large TCP/UDP beacons and subsequently smuggle a Session Initiation Protocol (SIP) packet containing the internal IP address inside an outbound HTTP POST request via TCP port 5060.
“This is achieved by carefully setting the [Maximum Segment Size] value of an attacker controlled TCP connection from the victim browser to an attacker’s server, so that a TCP segment in the ‘middle’ of the HTTP request will be entirely controlled by the attacker,” the researchers explained.
As a consequence, this causes the NAT application-level gateway (ALG) to open arbitrary ports for inbound connections to the client’s device via the internal IP address.
NAT Slipstreaming 2.0 is similar to the aforementioned attack in that it uses the same approach but relies on H.323 VoIP protocol instead of SIP to send multiple fetch requests to the attacker’s server on H.323 port (1720), thereby allowing the attacker to iterate through a range of IP addresses and ports, and opening each one of them to the Internet.
“A long lasting solution, unfortunately, would require some [overhaul] of the Internet infrastructure we’re accustomed to,” the researchers concluded.
“It is important to understand that security was not the principal agenda for the creation of NATs, rather it was mainly a by-product of the potential exhaustion of IPv4 addresses. Legacy requirements such as ALGs are still a dominant theme in the design of NATs today, and are the primary reason bypassing attacks are found again and again.”