A previously known Windows remote access Trojan (RAT) with credential-stealing capabilities has now expanded its scope to set its sights on users of Android devices to further the attacker’s espionage motives.
“The developers of LodaRAT have added Android as a targeted platform,” Cisco Talos researchers said in a Tuesday analysis. “A new iteration of LodaRAT for Windows has been identified with improved sound recording capabilities.”
Kasablanca, the group behind the malware, is said to have deployed the new RAT in an ongoing hybrid campaign targeting Bangladeshi users, the researchers noted.
The reason why Bangladesh-based organizations have been specifically singled out for this campaign remains unclear, as is the identity of the threat actor.
First documented in May 2017 by Proofpoint, Loda is an AutoIt malware typically delivered via phishing lures that’s equipped to run a wide range of commands designed to record audio, video, and capture other sensitive information, with recent variants aimed at stealing passwords and cookies from browsers.
The latest versions — dubbed Loda4Android and Loda4Windows — are a lot alike in that they come with a full set of data-gathering features that constitute a stalker application. However, the Android malware is also different, as it particularly avoids techniques often used by banking Trojans, like abusing Accessibility APIs to record on-screen activities.
Besides sharing the same command-and-control (C2) infrastructure for both Android and Windows, the attacks, which originated in October 2020, have targeted banks and carrier-grade voice-over-IP software vendors, with clues pointing to the malware author being based in Morocco.
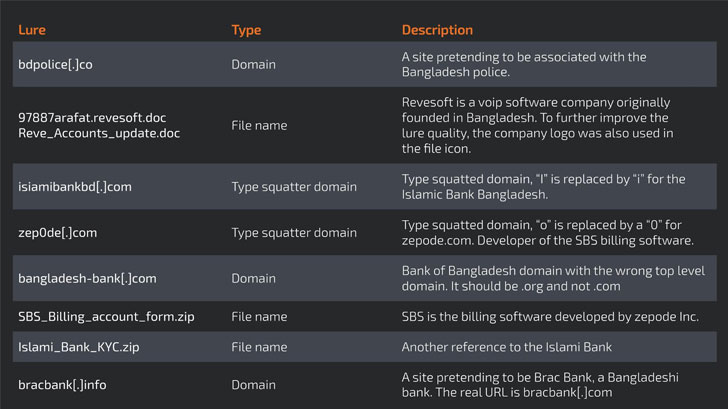
The attackers also made of a myriad number of social engineering tricks, ranging from typo squatted domains to malicious RTF documents embedded in emails, that, when opened, triggered an infection chain that leverages a memory corruption vulnerability in Microsoft Office (CVE-2017-11882) to download the final payload.
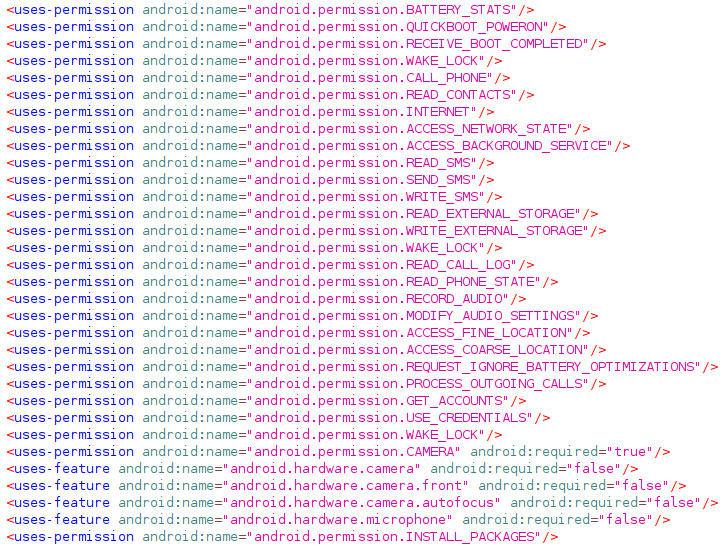
While the Android version of the malware can take photos and screenshots, read SMS and call logs, send SMS and perform calls to specific numbers, and intercept SMS messages or phone calls, its latest Windows counterpart comes with new commands that enable remote access to the target machine via Remote Desktop Protocol (RDP) and “Sound” command that makes use of BASS audio library to capture audio from a connected microphone.
“The fact that the threat group has evolved into hybrid campaigns targeting Windows and Android shows a group that is thriving and evolving,” said researchers with Cisco Talos.
“Along with these improvements, the threat actor has now focused on specific targets, indicating more mature operational capabilities. As is the case with earlier versions of Loda, both versions of this new iteration pose a serious threat, as they can lead to a significant data breach or heavy financial loss.”