Two new Android surveillanceware families have been found to target military, nuclear, and election entities in Pakistan and Kashmir as part of a pro-India, state-sponsored hacking campaign.
Dubbed Hornbill and Sunbird, the malware impersonates legitimate or seemingly innocuous services to cover its tracks, only to stealthily collect SMS, encrypted messaging app content, and geolocation, among other types of sensitive information.
The findings published by Lookout is the result of an analysis of 18GB of exfiltrated data that was publicly exposed from at least six insecurely configured command-and-control (C2) servers located in India.
“Some notable targets included an individual who applied for a position at the Pakistan Atomic Energy Commission, individuals with numerous contacts in the Pakistan Air Force (PAF), as well as officers responsible for electoral rolls (Booth Level Officers) located in the Pulwama district of Kashmir,” the researchers said in a Wednesday analysis.
In all, the attacks targeted 156 victims with phone numbers from India, Pakistan, and Kazakhstan over the last several years.
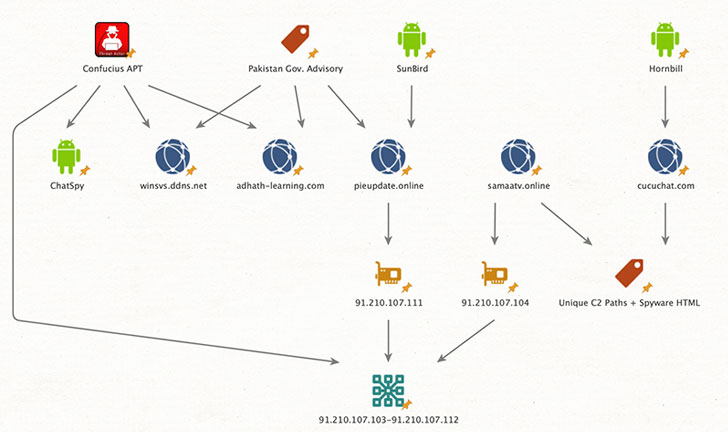
Lookout attributed the two tools to an advanced persistent threat (APT) tracked as Confucius, a group known for its attacks on South Asian countries at least since 2013. The cybersecurity firm called Hornbill a “passive reconnaissance tool.”
While Hornbill appears to be derived from the same code base as a previously active commercial surveillance product known as MobileSpy, SunBird has been traced to a group of Indian developers behind another mobile tracking software called BuzzOut. Clues uncovered by the Lookout also point to the fact the operators of Hornbill worked together at various Android and iOS app development companies registered and operating in or near the Indian city of Chandigarh.
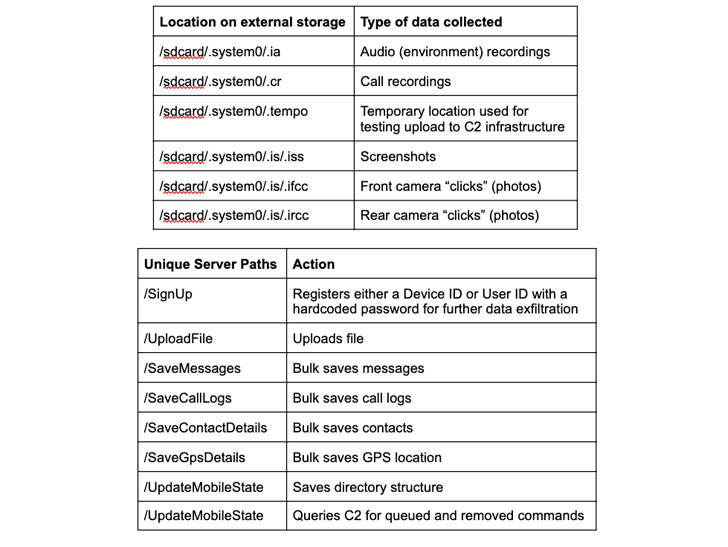
Both the pieces of spyware are equipped to amass a wide range of data, such as call logs, contacts, system information, location, photos stored on external drives, record audio and video, capture screenshots, with a particular focus on plundering WhatsApp messages and voice notes by abusing Android’s accessibility APIs.
SunBird also differs from Hornbill in that the former features remote access Trojan (RAT) functionality, allowing the attackers to execute arbitrary commands on the target device. In addition, it’s capable of exfiltrating browser histories, calendar information, and even siphoning content from BlackBerry Messenger and IMO instant messaging apps.
“Samples of SunBird have been found hosted on third-party app stores, indicating one possible distribution mechanism,” the researchers detailed. “Considering many of these malware samples are trojanized – as in they contain complete user functionality — social engineering may also play a part in convincing targets to install the malware.”
Lookout identified Hornbill samples as recently as December 2020, indicating an active use of the malware since their discovery in 2018. On the other hand, Sunbird seems to have been actively deployed in 2018 and 2019, before the threat actor shifted to another Android-based spyware product called ChatSpy last year.
Interestingly, the C2 infrastructure shared by Hornbill and SunBird reveals further connections with other stalkerware operations conducted by the Confucius group — including a publicly-accessible 2018 Pakistani government advisory warning of a desktop malware campaign targeting officers and government personnel — implying that the two tools are used by the same actor for different surveillance purposes.
Although India has been a relatively new entrant in the spyware and surveillance sector, Citizen Lab researchers last June outed a mercenary hack-for-hire group based in Delhi called BellTroX InfoTech that aimed to steal credentials from journalists, advocacy groups, investment firms, and an array of other high-profile targets.