Cybersecurity researchers have disclosed a new kind of Office malware distributed as part of a malicious email campaign that targeted more than 80 customers worldwide in an attempt to control victim machines and steal information remotely.
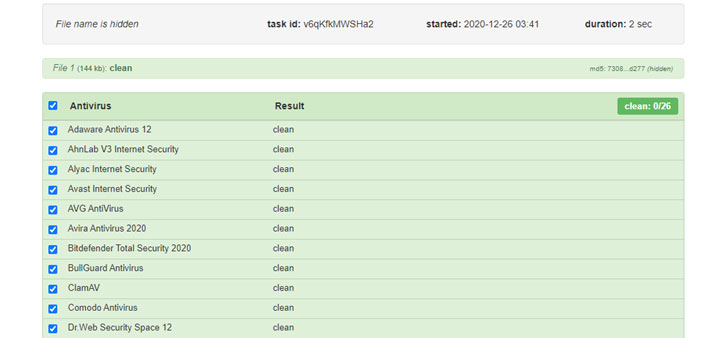
The tool — dubbed “APOMacroSploit” — is a macro exploit generator that allows the user to create an Excel document capable of bypassing antivirus software, Windows Antimalware Scan Interface (AMSI), and even Gmail and other email-based phishing detection.
APOMacroSploit is believed to be the work of two French-based threat actors “Apocaliptique” and “Nitrix,” who are estimated to have made at least $5000 in less than two months selling the product on HackForums.net.
About 40 hackers in total are said to be behind the operation, utilizing 100 different email senders in a slew of attacks targeting users in more than 30 different countries. The attacks were spotted for the first time at the end of November 2020, according to cybersecurity firm Check Point.
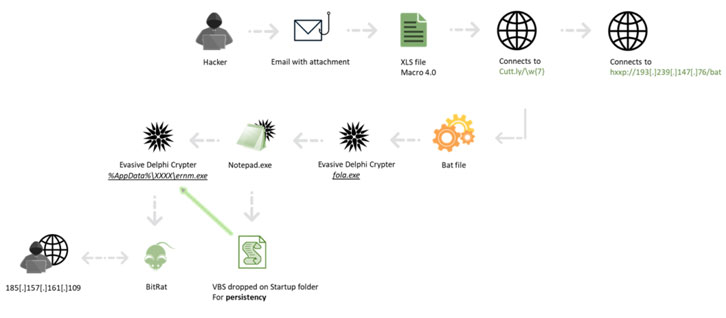
“The malware infection begins when the dynamic content of the attached XLS document is enabled, and an XLM macro automatically starts downloading a Windows system command script,” the firm said in a Tuesday report.
This system command script is retrieved from cutt.ly, which directs to servers hosting multiple BAT scripts that have the nickname of the customers inserted attached to the filenames. The scripts are also responsible for executing the malware (“fola.exe”) on Windows systems, but not before adding the malware location in the exclusion path of Windows Defender and disabling Windows cleanup.
In one of the attacks, the malware — a Delphi Crypter followed by a second-stage remote access Trojan called BitRAT — was found hosted on a Bulgarian website catering to medical equipment and supplies, implying that the attackers breached the website to store the malicious executable.
The idea of using “crypters” or “packers” has become increasingly popular among threat actors to not only compress but also to make malware samples more evasive and reverse engineer.
BitRAT, which was formally documented last August, comes with features to mine cryptocurrencies, hack webcams, log keystrokes, download and upload arbitrary files, and remotely control the system via a command-and-control server, which in this case resolved to a sub-domain of a legitimate Bulgarian website for video surveillance systems.
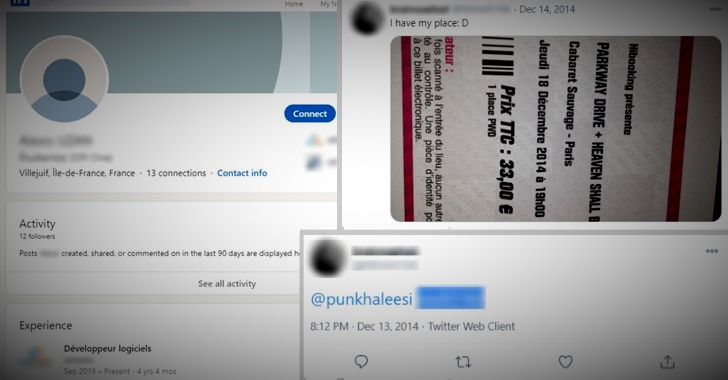
Further investigation by Check Point involved chasing the digital trail left by the two operators — including two League of Legends player profiles — ultimately leading the researchers to unmask the real identity of Nitrix, who revealed his actual name on Twitter when he posted a picture of a ticket he bought for a concert in December 2014.
While Nitrix is a software developer from Noisy-Le-Grand with four years of experience as a software developer, Apocaliptique’s use of alternative names such as “apo93” or “apocaliptique93” has stirred up possibilities that the individual may also be a French resident, as “93” is the colloquial name for the French department of Seine-Saint-Denis.
Check Point Research said it had alerted law enforcement authorities about the identities of the attackers.