Microsoft has awarded an independent security researcher $50,000 as part of its bug bounty program for reporting a flaw that could have allowed a malicious actor to hijack users’ accounts without their knowledge.
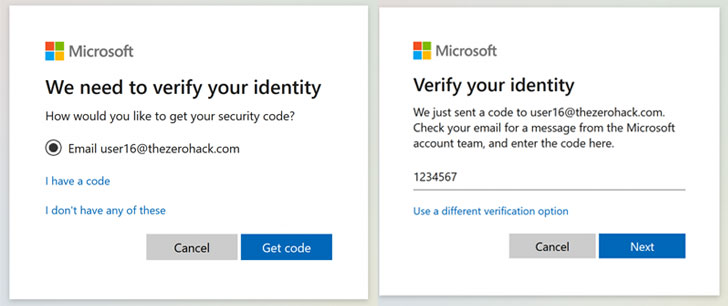
Reported by Laxman Muthiyah, the vulnerability aims to brute-force the seven-digit security code that’s sent to a user’s email address or mobile number to corroborate his (or her) identity before resetting the password in order to recover access to the account.
Put differently, the account takeover scenario is a consequence of privilege escalation stemming from an authentication bypass at an endpoint which is used to verify the codes sent as part of the account recovery process.
The company addressed the issue in November 2020, before details of the flaw came to light on Tuesday.
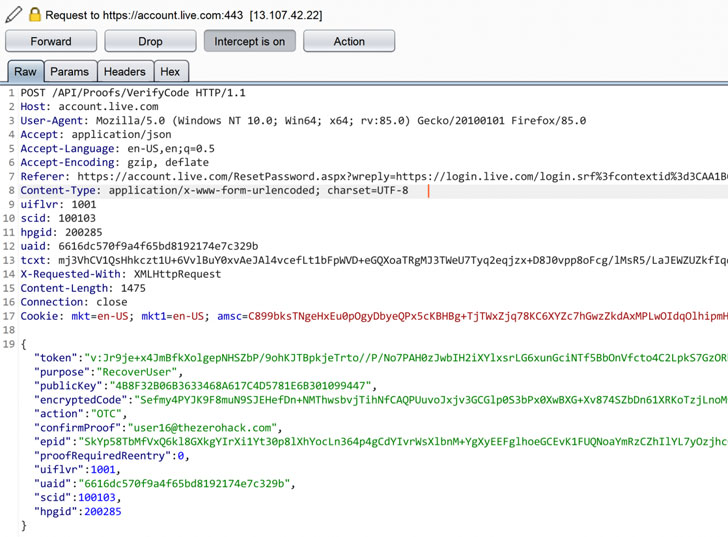
Although there are encryption barriers and rate-limiting checks designed to prevent an attacker from repeatedly submitting all the 10 million combinations of the codes in an automated fashion, Muthiyah said he eventually cracked the encryption function used to cloak the security code and send multiple concurrent requests.
Indeed, Muthiyah’s tests showed that out of 1000 codes that were sent, only 122 of them got through, with the others blocked with the error code 1211.
“I realized that they are blacklisting the IP address [even] if all the requests we send don’t hit the server at the same time,” the researcher said in a write-up, adding that “a few milliseconds delay between the requests allowed the server to detect the attack and block it.”
Following this discovery, Muthiyah said he was able to get around the rate-limiting constraint and reach the next step of changing the password, thereby allowing him to hijack the account.
While this attack only works in cases where the account is not secured by two-factor authentication, it can still be extended to defeat the two layers of protection and modify a target account’s password — something that could be prohibitive given the amount of computing resources required to mount an attack of this kind.
“Putting all together, an attacker has to send all the possibilities of 6 and 7 digit security codes that would be around 11 million request attempts and it has to be sent concurrently to change the password of any Microsoft account (including those with 2FA enabled),” Muthiyah said.
Separately, Muthiyah also employed a similar technique to Instagram’s account recovery flow by sending 200,000 concurrent requests from 1,000 different machines, finding that it was possible to achieve account takeover. He was rewarded $30,000 as part of the company’s bug bounty program.
“In a real attack scenario, the attacker needs 5000 IP addresses to hack an account,” Muthiyah noted. “It sounds big but that’s actually easy if you use a cloud service provider like Amazon or Google. It would cost around 150 dollars to perform the complete attack of one million codes.”