Hackers with suspected ties to Iran are actively targeting academia, government agencies, and tourism entities in the Middle East and neighboring regions as part of an espionage campaign aimed at data theft.
Dubbed “Earth Vetala” by Trend Micro, the latest finding expands on previous research published by Anomali last month, which found evidence of malicious activity aimed at UAE and Kuwait government agencies by exploiting ScreenConnect remote management tool.
The cybersecurity firm linked the ongoing attacks with moderate confidence to a threat actor widely tracked as MuddyWater, an Iranian hacker group known for its offensives primarily against Middle Eastern nations.
Earth Vetala is said to have leveraged spear-phishing emails containing embedded links to a popular file-sharing service called Onehub to distribute malware that ranged from password dumping utilities to custom backdoors, before initiating communications with a command-and-control (C2) server to execute obfuscated PowerShell scripts.
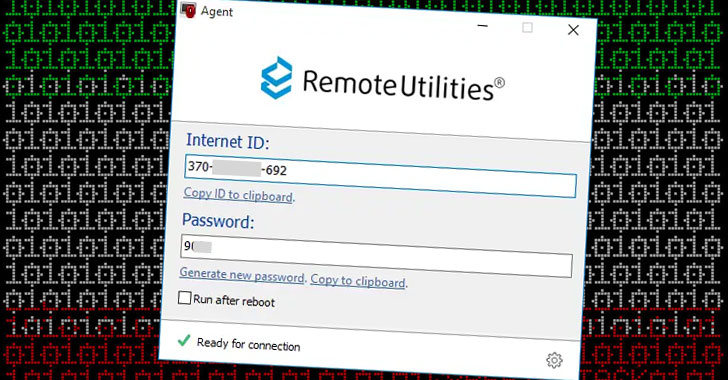
The links themselves direct victims to a .ZIP file that contains a legitimate remote administration software developed by RemoteUtilities, which is capable of downloading and uploading files, capturing screenshots, browsing files and directories, and executing and terminating processes.
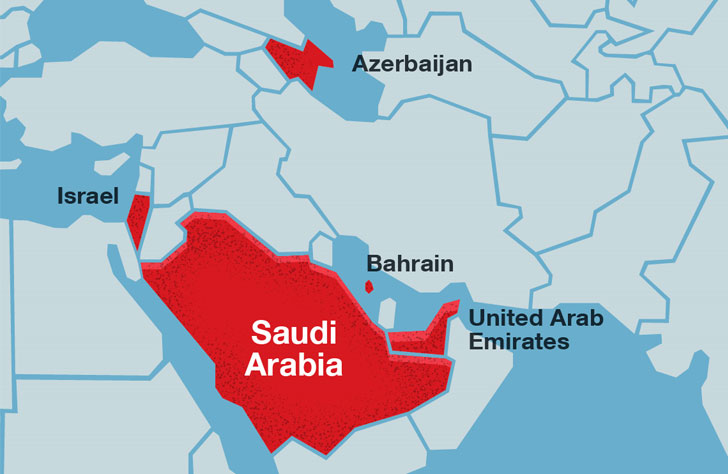 |
| Affected Countries |
Noting that the tactics and techniques between the two campaigns that distribute RemoteUtilities and ScreenConnect are broadly similar, Trend Micro said the targets of the new wave of attacks are mainly organizations located in Azerbaijan, Bahrain, Israel, Saudi Arabia, and the UAE.
In one particular instance involving a compromised host in Saudi Arabia, the researchers found that the adversary tried to unsuccessfully configure SharpChisel — a C# wrapper for a TCP/UDP tunneling tool called chisel — for C2 communications, before downloading a remote access tool, a credential stealer, and a PowerShell backdoor capable of executing arbitrary remote commands.
“Earth Vetala represents an interesting threat,” Trend Micro said. “While it possesses remote access capabilities, the attackers seem to lack the expertise to use all of these tools correctly. This is unexpected since we believe this attack is connected to the MuddyWater threat actors — and in other connected campaigns, the attackers have shown higher levels of technical skill.”