Cybersecurity researchers have discovered a new malware dropper contained in as many as 9 Android apps distributed via Google Play Store that deploys a second stage malware capable of gaining intrusive access to the financial accounts of victims as well as full control of their devices.
“This dropper, dubbed Clast82, utilizes a series of techniques to avoid detection by Google Play Protect detection, completes the evaluation period successfully, and changes the payload dropped from a non-malicious payload to the AlienBot Banker and MRAT,” Check Point researchers Aviran Hazum, Bohdan Melnykov, and Israel Wernik said in a write-up published today.
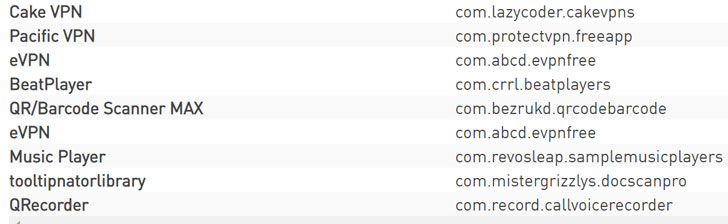
The apps that were used for the campaign include Cake VPN, Pacific VPN, eVPN, BeatPlayer, QR/Barcode Scanner MAX, Music Player, tooltipnatorlibrary, and QRecorder. After the findings were reported to Google on January 28, the rogue apps were removed from the Play Store on February 9.
Malware authors have resorted to a variety of methods to bypass app store vetting mechanisms. Whether be it using encryption to hide strings from analysis engines, creating rogue versions of legitimate apps, or crafting fake reviews to lure users into downloading the apps, fraudsters have hit back at Google’s attempts to secure the platform by constantly developing new techniques to slip through the net.
Equally popular are other methods like versioning, which refers to uploading a clean version of the app to the Play Store to build trust among users and then sneakily adding unwanted code at a later stage via app updates, and incorporating time-based delays to trigger the malicious functionality in an attempt to evade detection by Google.
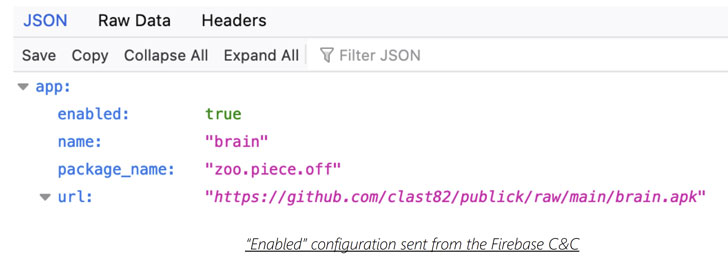
Clast82 is no different in that it utilizes Firebase as a platform for command-and-control (C2) communication and makes use of GitHub to download the malicious payloads, in addition to leveraging legitimate and known open-source Android applications to insert the Dropper functionality.
“For each application, the actor created a new developer user for the Google Play store, along with a repository on the actor’s GitHub account, thus allowing the actor to distribute different payloads to devices that were infected by each malicious application,” the researchers noted.
For instance, the malicious Cake VPN app was found to be based on an open-sourced version of its namesake created by a Dhaka-based developer by the name of Syed Ashraf Ullah. But once the app is launched, it takes advantage of the Firebase real-time database to retrieve the payload path from GitHub, which is then installed on the target device.
In the event the option to install apps from unknown sources has been turned off, Clast82 repeatedly urges the user every five seconds with a fake “Google Play Services” prompt to enable the permission, ultimately using it to install AlienBot, an Android banking MaaS (malware-as-a-service) capable of stealing credentials and two-factor authentication codes from financial apps.
Last month, a popular barcode scanner app with over 10 million installations turned rogue with a single update after its ownership changed hands. In a similar development, a Chrome extension by the name of The Great Suspender was deactivated following reports that the add-on stealthily added features that could be exploited to execute arbitrary code from a remote server.
“The hacker behind Clast82 was able to bypass Google Play’s protections using a creative, but concerning, methodology,” Hazum said. “With a simple manipulation of readily available 3rd party resources — like a GitHub account, or a FireBase account — the hacker was able to leverage readily available resources to bypass Google Play Store’s protections. The victims thought they were downloading an innocuous utility app from the official Android market, but what they were really getting was a dangerous trojan coming straight for their financial accounts.”