Cybersecurity researchers on Wednesday shed light on a new sophisticated backdoor targeting Linux endpoints and servers that’s believed to be the work of Chinese nation-state actors.
Dubbed “RedXOR” by Intezer, the backdoor masquerades as a polkit daemon, with similarities found between the malware and those previously associated with the Winnti Umbrella (or Axiom) threat group such as PWNLNX, XOR.DDOS and Groundhog.
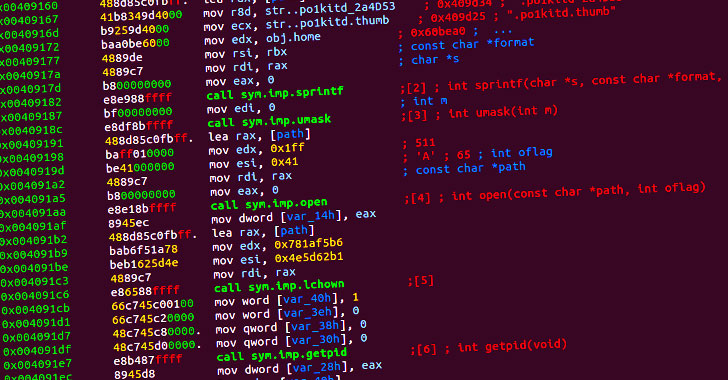
RedXOR’s name comes from the fact that it encodes its network data with a scheme based on XOR, and that it’s compiled with a legacy GCC compiler on an old release of Red Hat Enterprise Linux, suggesting that the malware is deployed in targeted attacks against legacy Linux systems.
Intezer said two samples of the malware were uploaded from Indonesia and Taiwan around Feb. 23-24, both countries that are known to be singled out by China-based threat groups.
Aside from the overlaps in terms of the overall flow and functionalities and the use of XOR encoding between RedXOR and PWNLNX, the backdoor takes the form of an unstripped 64-bit ELF file (“po1kitd-update-k”), complete with a typosquatted name (“po1kitd” vs. “polkitd”), which, upon execution, proceeds to create a hidden directory to store files related to the malware, before installing itself on the machine.
Polkit (née PolicyKit) is a toolkit for defining and handling authorizations, and is used for allowing unprivileged processes to communicate with privileged processes.
Additionally, the malware comes with an encrypted configuration that houses the command-and-control (C2) IP address and port, and the password it needs to authenticate to the C2 server, before establishing connection over a TCP socket.
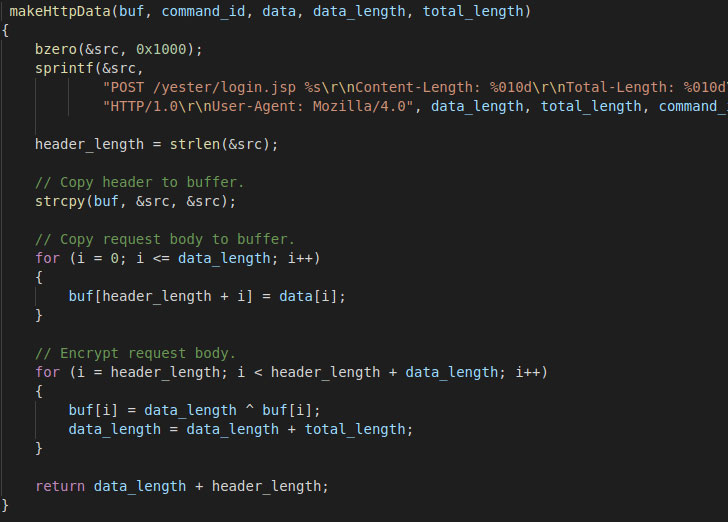
What’s more, the communications are not only disguised as harmless HTTP traffic, but are also encoded both ways using an XOR encryption scheme, the results of which are decrypted to reveal the exact command to be run.
RedXOR supports a multitude of capabilities, including gathering system information (MAC address, username, distribution, clock speed, kernel version, etc.), performing file operations, executing commands with system privileges, running arbitrary shell commands, and even options to remotely update the malware.
Users victimized by RedXOR can take protective measures by killing the process and removing all files related to the malware.
If anything, the latest development points to an increase in the number of active campaigns targeting Linux systems, in part due to widespread adoption of the operating system for IoT devices, web servers, and cloud servers, leading attackers to port their existing Windows tools to Linux or develop new tools that support both platforms.
“Some of the most prominent nation-state actors are incorporating offensive Linux capabilities into their arsenal and it’s expected that both the number and sophistication of such attacks will increase over time,” Intezer researchers outlined in a 2020 report charting the last decade of Linux APT attacks.