The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) on Wednesday issued a joint advisory warning of active exploitation of vulnerabilities in Microsoft Exchange on-premises products by nation-state actors and cybercriminals.
“CISA and FBI assess that adversaries could exploit these vulnerabilities to compromise networks, steal information, encrypt data for ransom, or even execute a destructive attack,” the agencies said. “Adversaries may also sell access to compromised networks on the dark web.”
The attacks have primarily targeted local governments, academic institutions, non-governmental organizations, and business entities in various industry sectors, including agriculture, biotechnology, aerospace, defense, legal services, power utilities, and pharmaceutical, which the agencies say are in line with previous activity conducted by Chinese cyber actors.
Tens of thousands of entities, including the European Banking Authority and the Norwegian Parliament, are believed to have been breached to install a web-based backdoor called the China Chopper web shell that grants the attackers the ability to plunder email inboxes and remotely access the target systems.
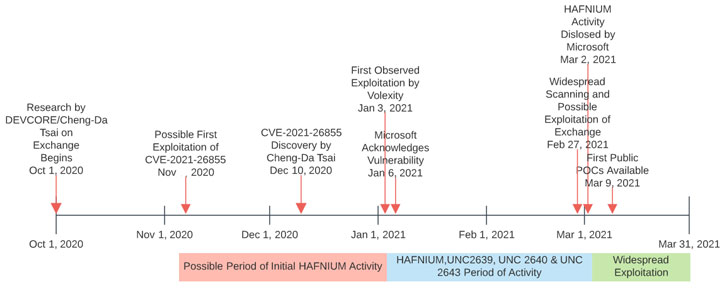
The development comes in light of the rapid expansion of attacks aimed at vulnerable Exchange Servers, with multiple threat actors exploiting the vulnerabilities as early as February 27 before they were eventually patched by Microsoft last week, swiftly turning what was labeled as “limited and targeted” into an indiscriminate mass exploitation campaign.
While there is no concrete explanation for the widespread exploitation by so many different groups, speculations are that the adversaries shared or sold exploit code, resulting in other groups being able to abuse these vulnerabilities, or that the groups obtained the exploit from a common seller.
From RCE to Web Shells to Implants
On March 2, 2021, Volexity publicly disclosed the detection of multiple zero-day exploits used to target flaws in on-premises versions of Microsoft Exchange Servers, while pegging the earliest in-the-wild exploitation activity on January 3, 2021.
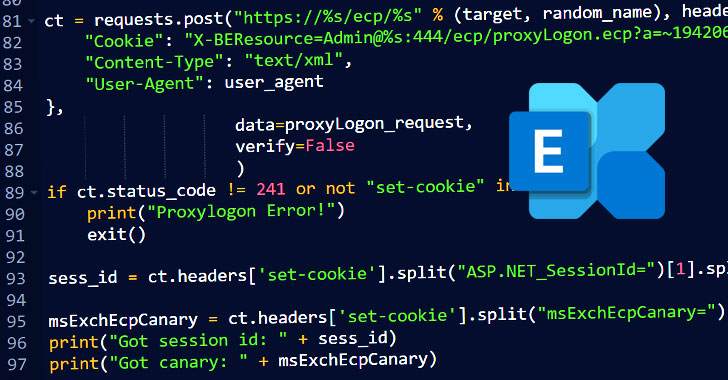
Successful weaponization of these flaws, called ProxyLogon, allows an attacker to access victims’ Exchange Servers, enabling them to gain persistent system access and control of an enterprise network.
Although Microsoft initially pinned the intrusions on Hafnium, a threat group that’s assessed to be state-sponsored and operating out of China, Slovakian cybersecurity firm ESET on Wednesday said it identified no fewer than 10 different threat actors that likely took advantage of the remote code execution flaws to install malicious implants on victims’ email servers.
Apart from Hafnium, the five groups detected as exploiting the vulnerabilities prior to the patch release are Tick, LuckyMouse, Calypso, Websiic, and Winnti (aka APT41 or Barium), with five others (Tonto Team, ShadowPad, “Opera” Cobalt Strike, Mikroceen, and DLTMiner) scanning and compromising Exchange servers in the days immediately following the release of the fixes.
Despite no conclusive evidence connecting the campaign to China, Domain Tools’ Senior Security Researcher Joe Slowik noted that several of the aforementioned groups have been formerly linked to China-sponsored activity, including Tick, LuckyMouse, Calypso, Tonto Team, Mikroceen APT Group, and the Winnti Group.
“It seems clear that there are numerous clusters of groups leveraging these vulnerabilities, the groups are using mass scanning or services that allow them to independently target the same systems, and finally there are multiple variations of the code being dropped, which may be indicative of iterations to the attack,” Palo Alto Networks’ Unit 42 threat intelligence team said.
In one cluster tracked as “Sapphire Pigeon” by researchers from U.S.-based Red Canary, attackers dropped multiple web shells on some victims at different times, some of which were deployed days before they conducted follow-on activity.
According to ESET’s telemetry analysis, more than 5,000 email servers belonging to businesses and governments from over 115 countries are said to have been affected by malicious activity related to the incident. For its part, the Dutch Institute for Vulnerability Disclosure (DIVD) reported Tuesday that it found 46,000 servers out of 260,000 globally that were unpatched against the heavily exploited ProxyLogon vulnerabilities.
Troublingly, evidence points to the fact that the deployment of the web shells ramped up following the availability of the patch on March 2, raising the possibility that additional entities have opportunistically jumped in to create exploits by reverse engineering Microsoft updates as part of multiple, independent campaigns.
“The day after the release of the patches, we started to observe many more threat actors scanning and compromising Exchange servers en masse,” said ESET researcher Matthieu Faou. “Interestingly, all of them are APT groups focused on espionage, except one outlier that seems related to a known coin-mining campaign (DLTminer). It is still unclear how the distribution of the exploit happened, but it is inevitable that more and more threat actors, including ransomware operators, will have access to it sooner or later.”
Aside from installing the web shell, other behaviors related to or inspired by Hafnium activity include conducting reconnaissance in victim environments by deploying batch scripts that automate several functions such as account enumeration, credential-harvesting, and network discovery.
Public Proof-of-Concept Available
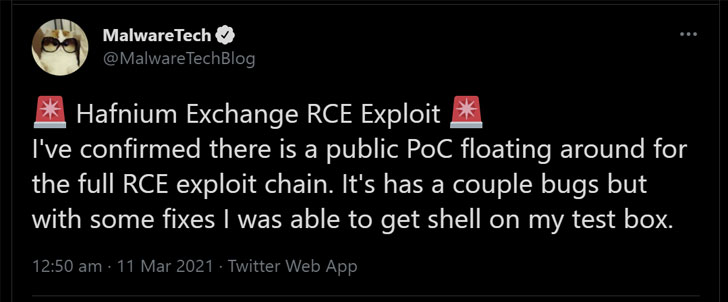
Complicating the situation further is the availability of what appears to be the first functional public proof-of-concept (PoC) exploit for the ProxyLogon flaws despite Microsoft’s attempts to take down exploits published on GitHub over the past few days.
“I’ve confirmed there is a public PoC floating around for the full RCE exploit chain,” security researcher Marcus Hutchins said. “It has a couple bugs but with some fixes I was able to get shell on my test box.”
Also accompanying the PoC’s release is a detailed technical write-up by Praetorian researchers, who reverse-engineered CVE-2021-26855 to build a fully functioning end-to-end exploit by identifying differences between the vulnerable and patched versions.
While the researchers deliberately decided to omit critical PoC components, the development has also raised concerns that the technical information could further accelerate the development of a working exploit, in turn triggering even more threat actors to launch their own attacks.
As the sprawling hack’s timeline slowly crystallizes, what’s clear is that the surge of breaches against Exchange Server appears to have happened in two phases, with Hafnium using the chain of vulnerabilities to stealthily attack targets in a limited fashion, before other hackers began driving the frenzied scanning activity starting February 27.
Cybersecurity journalist Brian Krebs attributed this to the prospect that “different cybercriminal groups somehow learned of Microsoft’s plans to ship fixes for the Exchange flaws a week earlier than they’d hoped.”
“The best advice to mitigate the vulnerabilities disclosed by Microsoft is to apply the relevant patches,” Slowik said. “However, given the speed in which adversaries weaponized these vulnerabilities and the extensive period of time pre-disclosure when these were actively exploited, many organizations will likely need to shift into response and remediation activities to counter existing intrusions.”