Researchers have discovered a new side-channel that they say can be reliably exploited to leak information from web browsers that could then be leveraged to track users even when JavaScript is completely disabled.
“This is a side-channel attack which doesn’t require any JavaScript to run,” the researchers said. “This means script blockers cannot stop it. The attacks work even if you strip out all of the fun parts of the web browsing experience. This makes it very difficult to prevent without modifying deep parts of the operating system.”
In avoiding JavaScript, the side-channel attacks are also architecturally agnostic, resulting in microarchitectural website fingerprinting attacks that work across hardware platforms, including Intel Core, AMD Ryzen, Samsung Exynos 2100, and Apple M1 CPUs — making it the first known side-channel attack on the iPhone maker’s new ARM-based chipsets.
The findings, which come from a group of academics from the Ben-Gurion Univ. of the Negev, the University of Michigan, and the University of Adelaide, will be presented at the USENIX Security Symposium in August.
Side-channel attacks typically rely on indirect data such as timing, sound, power consumption, electromagnetic emissions, vibrations, and cache behavior in an effort to infer secret data on a system. Specifically, microarchitectural side-channels exploit the shared use of a processor’s components across code executing in different protection domains to leak secret information like cryptographic keys.
Additionally, studies have also previously demonstrated fully automated attacks such as “Rowhammer.js” that rely on nothing but a website with malicious JavaScript to trigger faults on remote hardware, thereby gaining unrestricted access to systems of website visitors.
While these leaky side-channels can be effectively plugged by domain isolation techniques, browser vendors have incorporated defenses to offer protection against timing attacks and fingerprinting by reducing the precision of time-measuring functions, aside from adding support for completely disabling JavaScript using add-ons like NoScript.
However, the latest research released this week aims to bypass such browser-based mitigations by implementing a side-channel attack called “CSS Prime+Probe” constructed solely using HTML and CSS, allowing the attack to work even in hardened browsers like Tor, Chrome Zero, and DeterFox that have JavaScript fully disabled or limit the resolution of the timer API.
“A common trend in these approaches is that they are symptomatic and fail to address the root cause of the leakage, namely, the sharing of microarchitectural resources,” the researchers outlined. “Instead, most approaches attempt to prevent leakage by modifying browser behavior, striking different balances between security and usability.”
First, a small primer about cache-based side-channels: Unlike Flush+Reload attacks, wherein a spy can use a cache flush instruction (e.g., clflush in x86) to flush specific cache lines, and determine if the victim accessed this data by re-accessing the same memory line and timing the access for a hit (data is back in the cache) or miss (not accessed by the victim), Prime+Probe requires the attacker to populate the entire shared cache in order to evict victim’s data from the cache, and then timing its own accesses after it fills the cache — the presence of a cache miss indicating that the victim accessed the corresponding cache line causing the spy’s data to be removed.
Although these methods exploit a covert timing channel in the CPU cache, the new attack devised by Ben-Gurion researchers targets a cache-based side-channel in modern web browsers.
Specifically, the CSS Prime+Probe technique hinges on rendering a web page that includes a long HTML string variable covering the entire cache (e.g., a <div> element with a class name containing two million characters), then performing a search for a short, non-existent substring in the text, in turn forcing the search to scan the whole string. In the final step, the time to carry out this probe operation is sent to an attacker-controlled server.
“The attacker first includes in the CSS an element from an attacker-controlled domain, forcing DNS resolution,” the researchers explained. “The malicious DNS server logs the time of the incoming DNS request. The attacker then designs an HTML page that evokes a string search from CSS, effectively probing the cache. This string search is followed by a request for a CSS element that requires DNS resolution from the malicious server. Finally, the time difference between consecutive DNS requests corresponds to the time it takes to perform the string search, which […] is a proxy for cache contention.”
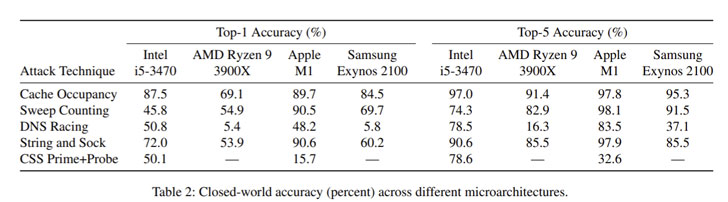
To evaluate the effectiveness of the methods via website fingerprinting attacks, the researchers used the aforementioned side-channel, among others, to collect traces of cache use while loading different websites — including Alexa Top 100 websites — using the “memorygrams” to train a deep neural network model to identify a specific set of websites visited by a target.
While JavaScript-based cache occupancy attacks offer higher accuracy of over 90% across all platforms when compared to CSS Prime+Probe, the study noted that the accuracy achieved by the latter is high enough to leak data that could allow malicious parties to identify and track users.
“So, how can security-conscious users access the web?,” the researchers concluded. “One complicating factor to this concept is the fact that the web browser makes use of additional shared resources beyond the cache, such as the operating system’s DNS resolver, the GPU, and the network interface. Cache partitioning seems a promising approach, either using spatial isolation based on cache coloring, or by OS-based temporal isolation.”