When dealing with user data, it’s essential that we design our password policies around compliance. These policies are defined both internally and externally.
While companies uphold their own password standards, outside forces like HIPAA and NIST have a heavy influence. Impacts are defined by industry and one’s unique infrastructure. How do IT departments maintain compliance with NIST and HIPAA?
We’ll discuss each compliance measure and its importance in this article.
What is NIST compliance?
Defined by the National Institute of Standards and Technology, NIST compliance aims to harden federal systems against cyber-attacks. While the agency is non-regulatory, it is part of the U.S. Department of Commerce, which has plenty of influence over government agencies and their contractors.
For example, NIST guidelines help agencies satisfy the requirements of the Federal Information Security Management Act (FISMA). NIST is instrumental in creating Federal Information Processing Standards (FIPS) that comply with FISMA. None of this would be possible without the NIST Cybersecurity Framework.
The Framework outlines steps and best practices that data processors should follow.
Controls relate to the following:
- Authentication-based access for local workstations, databases, websites, and web services
- Audit events for password changes, failed logins, and failed access related to Personal Identity Verification (PIV) credentials, third-party credentials, or admin actions
- Group (shared privilege) accounts and individual accounts
- Passwords, access tokens, biometrics, and multi-factor authentication (MFA)
- Encryption and password hashing
- Minimum password length, complexity, and validation time
Notably, an admin complying with NIST standards might define necessary password policies to enforce minimum length and leaked password filtering requirements. Password policy could also include the blocking of common character substitution and other predictable password construction patterns such as changing a password by only adding numbers or symbols at the end.
NIST encourages removing password expiry and complexity — but this needs to be weighed with the organization’s regulatory obligations; for example, PCI-DSS and HITRUS-CFS require these.
Regular assessment or identification of compromised passwords is crucial. Organizations can use automated tools to identify and enforce change when detected continually.
NIST Cybersecurity Framework compliance is an excellent stepping stone to strong security. However, the agency warns that NIST guidelines do NOT create impenetrable systems. No framework is perfect.
What is HIPAA compliance?
Personal health information falls under the high-sensitivity umbrella. These records are confidential and contain private information, hence why databases and data warehouses must employ strong protections. There’s also an argument that password policies exist to protect patient dignity.
Patient-doctor confidentiality, and provider-patient relationships, are critical to maintaining privacy across the healthcare landscape. However, many patients don’t even have a stellar perception of healthcare providers. In 2016, Black Book revealed that 87% of patients withheld some degree of health information from “trusted” providers.
You might see where this is going. Personal medical data is so personal that trust is hard-earned outside of one’s inner circle. That phenomenon is amplified in our digital age, where remote access and electronic record sharing are commonplace.
Some other areas of concern:
- Patient financial information
- Patient portal access
- Personal information submitted as part of an online profile
Protection via password compliance
So much information is collected these days that patients themselves find it difficult to sift through. Technology-savvy providers are entrusted with safeguarding this data and making it accessible to the right individual(s). This is where the Health Insurance Portability and Accountability Act (HIPAA) steps in.
First, HIPAA outlines three types of standards that organizations must meet:
- Technical standards – which describe the safeguards necessary to protect and maintain an infrastructure that stores personal electronic health information
- Physical standards – which describe how brick-and-mortar premises must be protected both inside and out
- Administrative standards – which describe the necessary controls and maintenance efforts on the part of staff members in upholding the security of personal health information
Our natural focus is on technical and administrative standards—the first covers online systems or databases that store highly sensitive data. Administrative standards entail staff roles in dictating password management and access authorization. What does that look like in a password policy?
Note that HIPAA and NIST guidelines aren’t mutually exclusive. Following these rules will keep you both HIPAA and NIST compliant:
- Mandate that passwords be 8+ characters in length (even up to 64 for some data)
- Don’t give password hints to users
- Encourage the creation of memorable passwords, not obscure ones requiring record keeping
- Vet passwords according to banned password lists, or dictionaries of compromised passwords
These guidelines are critical. Additionally, HIPAA does provide some wiggle room in accordance with the entity monitoring key data. Because providers can be microscopic and massive (health systems, insurance providers), unique password policies are needed.
Better NIST and HIPAA Compliance with Specops
External tools can provide plenty of help when crafting compliant password policies. We recommend two tools: Specops Password Auditor and Specops Password Policy. These automate multiple processes critical to ongoing password security.
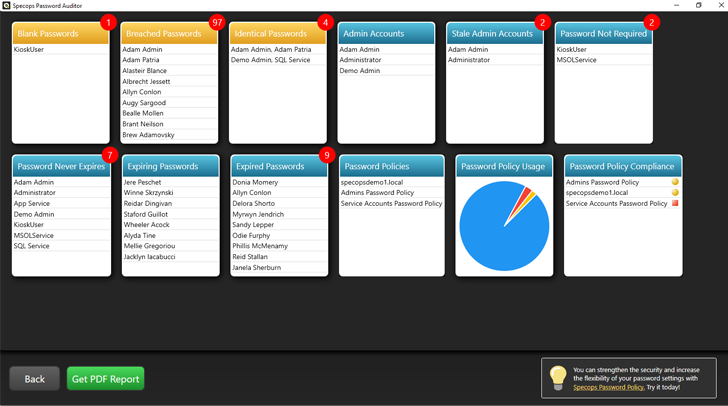
Password Auditor is a free tool that offers three main benefits: password reporting, Active Directory account auditing, and standards compliance. Auditor scans your environment to ensure that general and fine-grained password policies promote secure passwords. Informative reports highlight weak points and problematic accounts—simplifying remediation. These reports even compare your policies against those pushed by the NIST.
Password Auditor will also show you how resilient your systems are against attacks. You can also view domains and their respective accounts. Vulnerable passwords are identified if they match those found within our breached-passwords lists.
Meanwhile, Password Policy provides similar benefits with greater granularity. Mainly, you can accomplish the following: block weak passwords, create compliant password policies, and target password entropy. The tool lets you bring your own password dictionary and incorporate the Specops list of 2 billion breached passwords.
Specops does the heavy lifting—automatically accepting passwords (and even phrases) while rejecting non-compliant passwords. Enforce your own password length, complexity, and character requirements. Finally, compliance tools will show you how your existing policies compare to industry-compliant policies. Password Policy provides templating and analysis to protect company-held data against popular cyber-attack methods.
NIST and HIPAA compliance rests with strong password policies. Thankfully, the compliance process doesn’t have to be complicated.