Attention, Android users! A banking malware capable of stealing sensitive information is “spreading rapidly” across Europe, with the U.S. likely to be the next target.
According to a new analysis by Proofpoint, the threat actors behind FluBot (aka Cabassous) have branched out beyond Spain to target the U.K., Germany, Hungary, Italy, and Poland. The English-language campaign alone has been observed to make use of more than 700 unique domains, infecting about 7,000 devices in the U.K.
In addition, German and English-language SMS messages were found being sent to U.S. users from Europe, which Proofpoint suspects could be the result of malware propagating via contact lists stored on compromised phones. A concerted campaign aimed at the U.S. is yet to be detected.
FluBot, a nascent entry in the banking trojan landscape, began its operations late last year, with campaigns leveraging the malware infecting more than 60,000 users in Spain, according to an analysis published by Proactive Defence Against Future Threats (PRODAFT) in March 2021. It’s said to have amassed more than 11 million phone numbers from the devices, representing 25% of the total population in Spain.
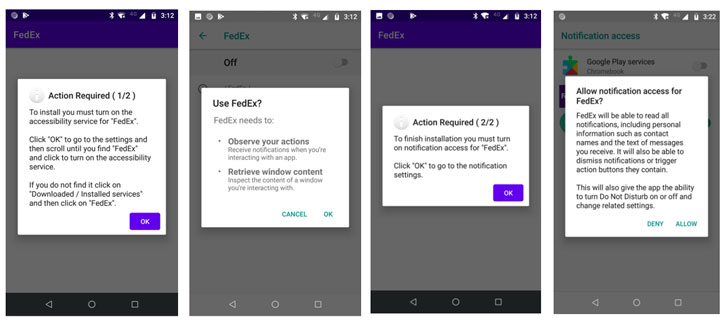
Primarily distributed via SMS phishing (aka smishing), the messages masquerade as a delivery service such as FedEx, DHL, and Correos, seemingly notifying users of their package or shipment delivery status along with a link to track the order, which, when clicked, downloads malicious apps that have the encrypted FluBot module embedded within them.
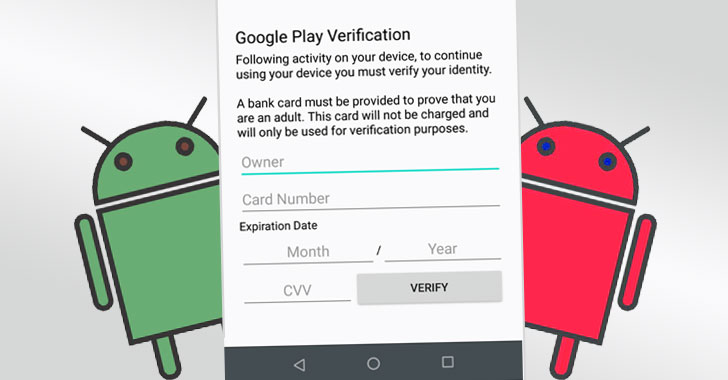
“FluBot is a new Android banking malware that uses overlay attacks to perform webview-based application phishing,” the researchers noted. “The malware mainly targets mobile banking and cryptocurrency applications but also gathers a wide range of user data from all installed applications on a given device.”
Upon installation, FluBot not only tracks the applications launched on the device but also overlays login pages of financial apps with specially-crafted malicious variants from an attacker-controlled server, designed with the goal of hijack credentials, in addition to retrieving contact lists, messages, calls, and notifications by abusing the Android Accessibility Service.
Although Spanish authorities arrested four criminals suspected to be behind the FluBot campaign, infections have picked up, while simultaneously expanding the countries targeted to include Japan, Norway, Sweden, Finland, Denmark, and the Netherlands in a short period of time, per the latest insights from ThreatFabric.
The spurt in FluBot activity has prompted Germany’s Federal Office for Information Security (BSI) and the U.K.’s National Cyber Security Centre (NCSC) to issue alerts warning of ongoing attacks via fraudulent SMS messages that trick users into installing “spyware that steals passwords and other sensitive data.”
“FluBot is likely to continue to spread at a fairly rapid rate, moving methodically from country to country via a conscious effort by the threat actors,” Proofpoint researchers said. “As long as there are users willing to trust an unexpected SMS message and follow the threat actors’ provided instructions and prompts, campaigns such as these will be successful.”