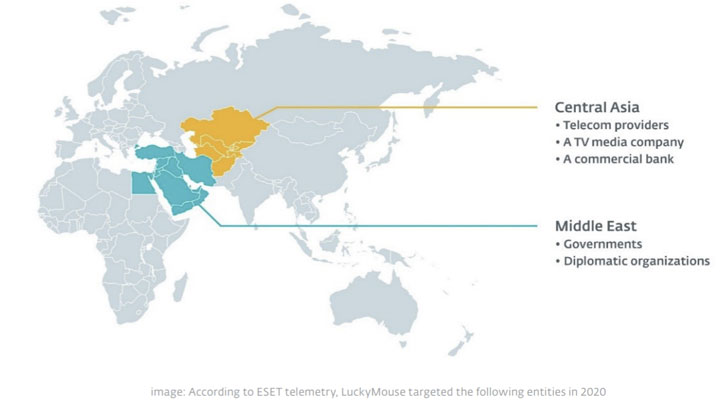
An adversary known for its watering hole attacks against government entities has been linked to a slew of newly detected intrusions targeting various organizations in Central Asia and the Middle East.
The malicious activity, collectively named “EmissarySoldier,” has been attributed to a threat actor called LuckyMouse, and is said to have happened in 2020 with the goal of obtaining geopolitical insights in the region. The attacks involved deploying a toolkit dubbed SysUpdate (aka Soldier) in a number of breached organizations, including government and diplomatic agencies, telecom providers, a TV media company, and a commercial bank.
LuckyMouse, also referred to as APT27 and Emissary Panda, is a sophisticated cyberespionage group that has a history of breaching multiple government networks in Central Asia and the Middle East. The actor has also been linked to cyberattacks aimed at transnational organizations such as the International Civil Aviation Organization (ICAO) in 2019 and recently attracted attention for exploiting ProxyLogon flaws to compromise the email server of a governmental entity in the Middle East.
EmissarySoldier is only the latest in a series of surveillance efforts aimed at the targets.
“In order to compromise victims, LuckyMouse typically uses watering holes, compromising websites likely to be visited by its intended targets, ESET malware researcher Matthieu Faou said in a report published today. “LuckyMouse operators also perform network scans to find vulnerable internet-facing servers run by their intended victims.”
What’s more, ESET also found a few infected internet-facing systems running Microsoft SharePoint, which the researchers suspect occurred by taking advantage of remote code execution vulnerabilities in the application.
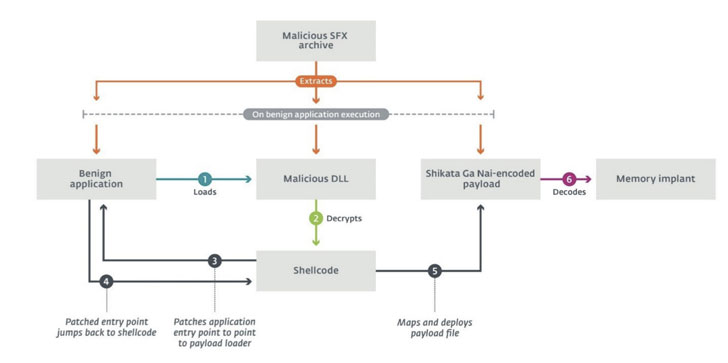
Regardless of the method used to gain an initial foothold, the attack chain culminates in the deployment of custom post-compromise implants, SysUpdate, or HyperBro, both of which leverage DLL search order hijacking to load malicious payloads and thwart detection. “The trident model features a legitimate application vulnerable to DLL hijacking, a custom DLL that loads the payload, and a raw Shikata Ga Nai-encoded binary payload,” Faou noted.
For its part, SysUpdate functions as a modular tool, with each component devoted to a particular operational purpose. It involves abusing a benign application as a loader for a malicious DLL, which in turn loads the first-stage payload that ultimately decodes and deploys the memory implant on the compromised system. Since its discovery in 2018, the toolkit has undergone numerous revisions devoted to adding new functionalities, indicating that the operators are actively working to revamp their malware arsenal.
“LuckyMouse was increasingly active throughout 2020, seemingly going through a retooling process in which various features were being incrementally integrated into the SysUpdate toolkit,” Faou said. “This may be an indicator that the threat actors behind LuckyMouse are gradually shifting from using HyperBro to SysUpdate.”