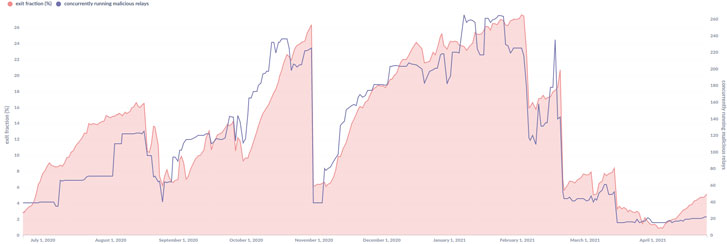
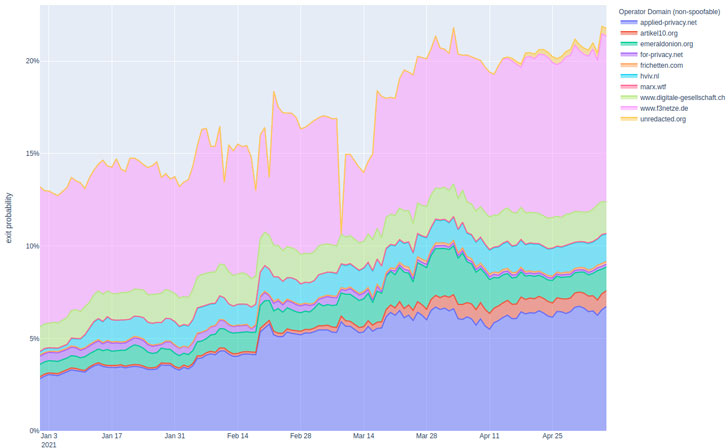
An unknown threat actor managed to control more than 27% of the entire Tor network exit capacity in early February 2021, a new study on the dark web infrastructure revealed.
“The entity attacking Tor users is actively exploiting tor users since over a year and expanded the scale of their attacks to a new record level,” an independent security researcher who goes by the name nusenu said in a write-up published on Sunday. “The average exit fraction this entity controlled was above 14% throughout the past 12 months.”
It’s the latest in a series of efforts undertaken to bring to light malicious Tor activity since December 2019. The attacks, which are said to have begun in January 2020, were first documented and exposed by the same researcher in August 2020.
Tor is open-source software for enabling anonymous communication on the Internet. It obfuscates the source and destination of a web request by directing network traffic through a series of relays in order to mask a user’s IP address and location and usage from surveillance or traffic analysis. While middle relays typically take care of receiving traffic on the Tor network and pass it along, an exit relay is the final node that Tor traffic passes through before it reaches its destination.
Exit nodes on the Tor network have been subverted in the past to inject malware such as OnionDuke, but this is the first time a single unidentified actor has managed to control such a large fraction of Tor exit nodes.
The hacking entity maintained 380 malicious Tor exit relays at its peak in August 2020, before the Tor directory authorities intervened to cull the nodes from the network, following which the activity once again crested early this year, with the attacker attempting to add over 1,000 exit relays in the first week of May. All the malicious Tor exit relays detected during the second wave of the attacks have since been removed.
The main purpose of the attack, according to nusenu, is to carry out “person-in-the-middle” attacks on Tor users by manipulating traffic as it flows through its network of exit relays. Specifically, the attacker appears to perform what’s called SSL stripping to downgrade traffic heading to Bitcoin mixer services from HTTPS to HTTP in an attempt to replace bitcoin addresses and redirect transactions to their wallets instead of the user-provided bitcoin address.
“If a user visited the HTTP version (i.e. the unencrypted, unauthenticated version) of one of these sites, they would prevent the site from redirecting the user to the HTTPS version (i.e. the encrypted, authenticated version) of the site,” the maintainers of Tor Project explained last August. “If the user didn’t notice that they hadn’t ended up on the HTTPS version of the site (no lock icon in the browser) and proceeded to send or receive sensitive information, this information could be intercepted by the attacker.”
To mitigate such attacks, the Tor Project outlined a number of recommendations, including urging website administrators to enable HTTPS by default and deploy .onion sites to avoid exit nodes, adding it’s working on a “comprehensive fix” to disable plain HTTP in Tor Browser.
“The risk of being the target of malicious activity routed through Tor is unique to each organization,” the U.S. Cybersecurity Security and Infrastructure Security Agency (CISA) said in an advisory in July 2020. “An organization should determine its individual risk by assessing the likelihood that a threat actor will target its systems or data and the probability of the threat actor’s success given current mitigations and controls.”
“Organizations should evaluate their mitigation decisions against threats to their organization from advanced persistent threats (APTs), moderately sophisticated attackers, and low-skilled individual hackers, all of whom have leveraged Tor to carry out reconnaissance and attacks in the past,” the agency added.