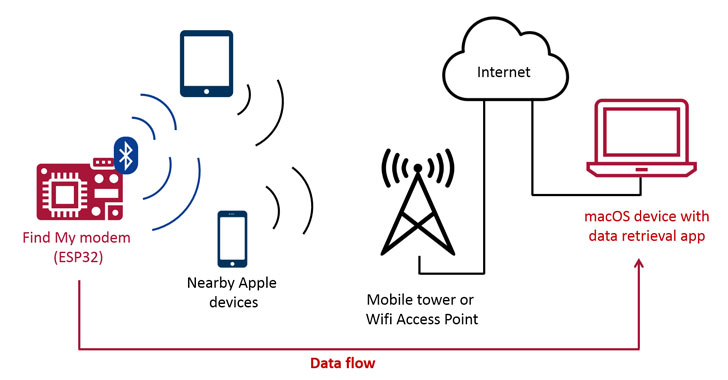
Latest research has demonstrated a new exploit that enables arbitrary data to be uploaded from devices that are not connected to the Internet by simply sending “Find My Bluetooth” broadcasts to nearby Apple devices.
“It’s possible to upload arbitrary data from non-internet-connected devices by sending Find My [Bluetooth Low Energy] broadcasts to nearby Apple devices that then upload the data for you,” Positive Security researcher Fabian Bräunlein said in a technical write-up disclosed last week.
“Being inherent to the privacy and security-focused design of the Find My Offline Finding system, it seems unlikely that this misuse can be prevented completely.”
The study builds on a previous study by TU Darmstadt published in March 2021, which disclosed two distinct design and implementation flaws in Apple’s crowdsourced Bluetooth location tracking system that could lead to a location correlation attack and unauthorized access to a user’s location history of the past seven days.
The investigation was augmented by the release of a framework called OpenHaystack that’s designed to let any user create an “AirTag,” enabling individuals to track personal Bluetooth devices via Apple’s massive Find My network.
But the reverse engineering of Apple’s Find My offline finding system also left the door open to the possibility that the protocol could be emulated to upload arbitrary data to the Internet by broadcasting the information via Bluetooth beacons that would get picked up by Apple devices in close physical proximity, and then subsequently relay the encrypted data to Apple’s servers, from where a macOS application can retrieve, decode, and display the uploaded data.
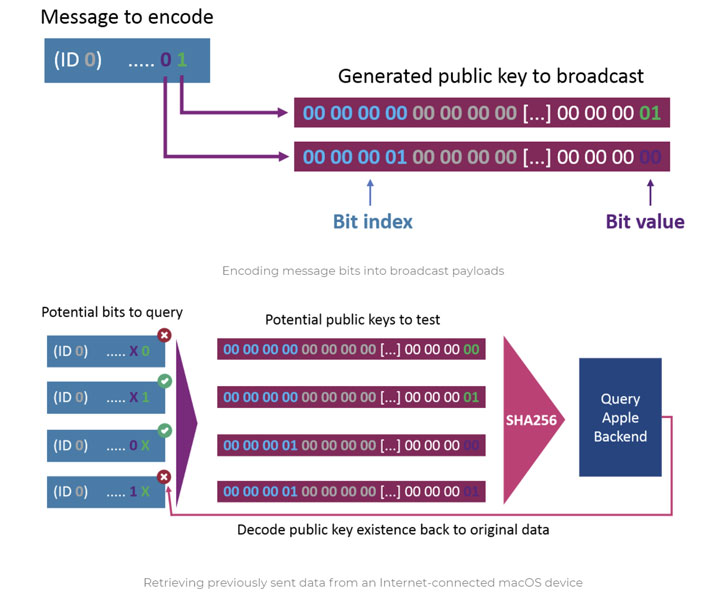
One of the core aspects of Find My is its rotating key scheme consisting of a pair of public-private keys that are deterministically changed every 15 minutes, with the public key sent within the Bluetooth Low Energy advertisement packet.
Thus when nearby Apple devices such as MacBooks, iPhones, and iPads receive the broadcast, they fetch their own location, then encrypt the location using the aforementioned public key before sending the encrypted location report to iCloud along with a hash of the public key. In the final step, the owner of the lost device can use a second Apple device signed in with the same Apple ID to access the approximate location.
The encryption protections mean that not only does Apple not know which public keys belong to a specific lost device or AirTag, it also doesn’t have any knowledge of which location reports are intended for a specific user — hence the above Apple ID requirement. “The security solely lies in the encryption of the location reports: The location can only be decrypted with the correct private key, which is infeasible to brute force and only stored on the paired Owner Device,” Bräunlein said.
The idea, therefore, is to exploit this gap by encoding a message into the broadcast payloads and then obtaining them on the other end using a data fetcher component based on OpenHaystack that decrypts and extracts the information transmitted from the sender device, say, a microcontroller.
“When sending, the data is encoded in the public keys that are broadcasted by the microcontroller. Nearby Apple devices will pick up those broadcasts and forward the data to an Apple backend as part of their location reporting. Those reports can later be retrieved by any Mac device to decode the sent data,” Bräunlein explained.
While malicious real-world implications of such an exploit may seem moot, it’s also difficult for Apple to defend against an attack of this kind due to the end-to-end encrypted nature of the Find My network. To counter such unintended uses, the researcher suggests hardening the system in two possible ways, including authenticating the BLE advertisement and applying rate limits on-location report retrievals by caching the hashes and ensuring that the only “16 new key ids are queried per 15 minutes and Apple ID.” It’s worth noting that there is a limit of 16 AirTags per Apple ID.
“In the world of high-security networks, where combining lasers and scanners seems to be a noteworthy technique to bridge the air gap, the visitor’s Apple devices might also become feasible intermediaries to exfiltrate data from certain air gapped systems or Faraday caged rooms,” Bräunlein said.