Mozilla has begun rolling out a new security feature for its Firefox browser in nightly and beta channels that aims to protect users against a new class of side-channel attacks from malicious sites.
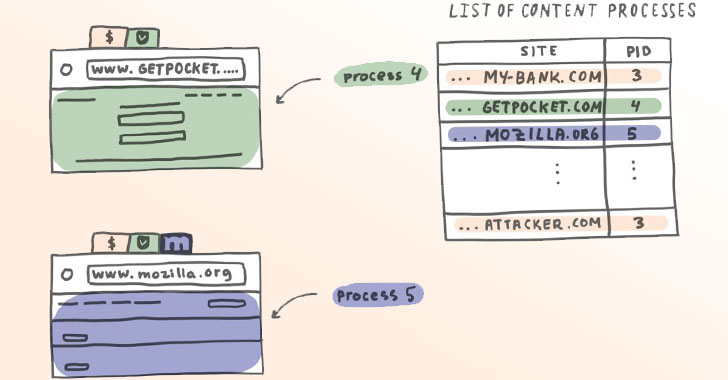
Called “Site Isolation,” the implementation loads each website separately in its own operating system process and, as a result, prevents untrusted code from a rogue website from accessing confidential information stored in other sites.
“This fundamental redesign of Firefox’s Security architecture extends current security mechanisms by creating operating system process-level boundaries for all sites loaded in Firefox for Desktop,” Mozilla said in a statement. “Isolating each site into a separate operating system process makes it even harder for malicious sites to read another site’s secret or private data.”
The motivation for Site Isolation can be traced all the way back to January 2018 when Spectre and Meltdown vulnerabilities were publicly disclosed, forcing browser vendors and chipmakers to incorporate defenses to neutralize attacks that could break the boundaries between different applications and allow an adversary to read passwords, encryption keys, and other valuable information directly from a computer’s kernel memory.
Troublingly, such timing side-channel attacks could be launched remotely via websites running malicious JavaScript code, necessitating browser makers, including Mozilla, to offer mitigations by reducing the precision of time-measuring functions. However, the current patches for Spectre have been a mere “band-aid” and don’t offer protection against all theoretical variants of the attacks.
“Despite existing security mitigations, the only way to provide memory protections necessary to defend against Spectre-like attacks is to rely on the security guarantees that come with isolating content from different sites using the operating system’s process separation,” Mozilla’s Anny Gakhokidze said.
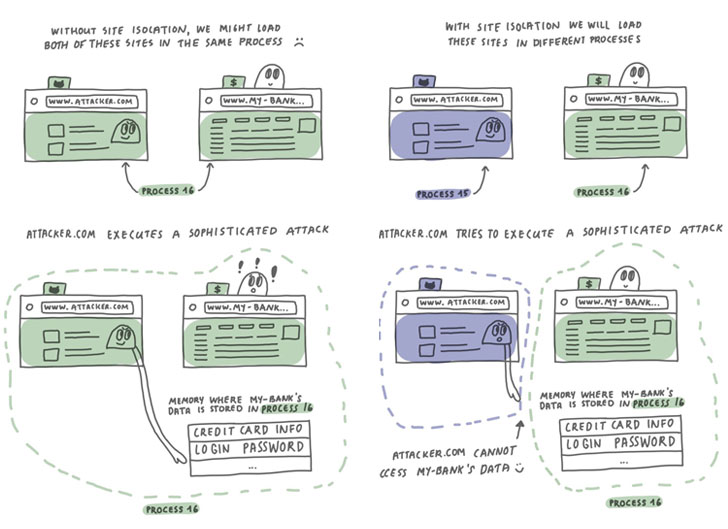
Thus began Mozilla’s initiative for Site Isolation in April 2018 under the moniker Project Fission. While Firefox’s current architecture allows the privileged “parent” process to spawn eight web content processes, it could also open the door to a scenario where two completely different websites end up in the same process and, therefore, share process memory, thereby putting legitimate websites at risk of speculative execution attacks.
This also means a web page that comes embedded with multiple subframes from different sites (e.g., ad slots in web pages) will all share the same process memory, in turn enabling a top-level site to obtain secrets from an embedded subframe it shouldn’t have access to in the first place, and vice-versa.
This is where Site Isolation comes in. It loads every website into its own process, including those that are embedded into the page, and isolates their memory from each other, thus effectively making it difficult for a malicious domain from accessing information entered in a different domain.
Besides hardening the security of Firefox by offering operating system-level process separation for each site, Site Isolation is also expected to bring other performance benefits, including efficient use of underlying hardware and improved stability, as a subframe or a tab crash will no longer affect other websites or processes.
Users running Firefox Nightly builds can enable the feature by navigating to “about:preferences#experimental” and ticking the “Fission (Site Isolation)” checkbox. Those on Firefox Beta can do so by heading to “about:config” and setting “fission.autostart” to “true.”