In a huge sting operation, the U.S. Federal Bureau of Investigation (FBI) and Australian Federal Police (AFP) ran an “encrypted chat” service called ANoM for almost 3 years to intercept 27 million messages between criminal gang members globally.
Dubbed Operation Ironside (AFP), Operation Greenlight (Europol), and Operation Trojan Shield (FBI), the long-term covert probe into transnational and serious organized crime culminated in the arrests of 224 offenders on 526 charges in Australia, with 55 luxury vehicles, eight tons of cocaine, 22 tons of cannabis and cannabis resin, 250 firearms, and more than $48 million in various currencies and cryptocurrencies seized in raids around the world.
A total of more than 800 arrests have been reported across 18 countries, including New Zealand, Germany, and Sweden. Europol called it the “biggest ever law enforcement operation against encrypted communication.”
The communications allegedly involved plots to kill, mass drug trafficking, and gun distribution, according to the AFP. Access to these encrypted messages was gained lawfully through using the Telecommunications and Other Legislation Amendment (Assistance and Access) Act 2018, the agency added.
“For almost three years, the AFP and the FBI have monitored criminals’ encrypted communications over a Dedicated Encrypted Communications Platform,” AFP said. “The AFP built a capability that allowed law enforcement to access, decrypt and read communications on the platform. The AFP and FBI were able to capture all the data sent between devices using the platform.”
The encryption barriers were surmounted by inserting a master key into ANoM’s encryption system that was stealthily attached to every message, thus enabling the law enforcement to execute a man-in-the-middle (MitM) scheme to decrypt and retrieve the messages as they were transmitted. For devices located outside of the U.S., an encrypted “BCC” copy of the messages was forwarded to a server outside of the U.S., from where it was forwarded to a second FBI-owned server for subsequent decryption.
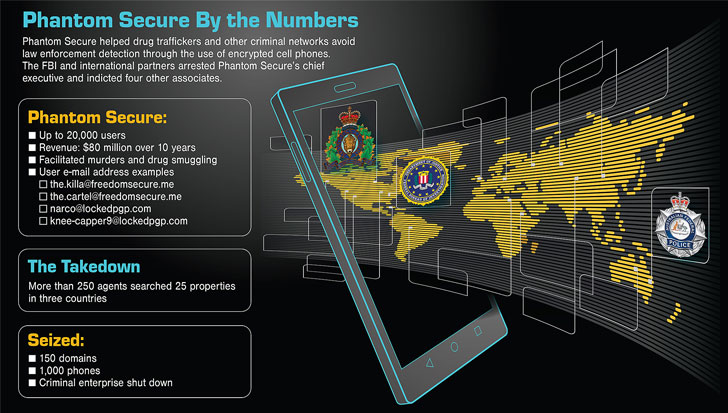
ANoM (aka Anøm) is said to have been intentionally created to fill the vacuum left by Phantom Secure, another encrypted phone service dismantled by the FBI in 2018, thereby allowing the agencies to monitor the conversations without the criminals’ knowledge. In a move echoing the latter, criminals needed to be part of a closed network to get hold of a phone on which ANoM came preinstalled, while the devices themselves were stripped of all other functionality.
Among some of the features of the app included —
- Send encrypted text and voice messages
- Make secure voice calls
- Share photos, videos, animated GIFs, locations, drawings and more.
- Send files of any type
In addition, phone owners can also verify their contacts via a QR code, create distribution lists, and chat completely anonymously without even requiring a phone number, according to a listing from the now taken down anom.io website.
Operation Ironside follows similar law enforcement actions that involved infiltrating encrypted chat platform EncroChat to monitor millions of encrypted messages sent by organized crime networks through the platform. Earlier this year, a coordinated exercise under the name “Operation Argus” staged major interventions against Sky ECC, leading to nearly 275 raids and the arrest of 91 suspects, besides seizing 17 tonnes of cocaine and €1.2 million.
The FBI used a confidential human source, who had previously sold phones from both Phantom Secure and Sky Global to criminal organizations and had “invested a substantial amount of money into the development of a new hardened encrypted device” (i.e., ANoM), to distribute the devices to criminal networks.
“The devices organically circulated and grew in popularity among criminals, who were confident of the legitimacy of the app because high-profile organised crime figures vouched for its integrity,” the AFP said. By May 2021, the phones, which were procured from the black market, had increased to 11,800 in number, of which about 9,000 are in active use, spanning over 300 criminal syndicates operating in more than 100 countries.
The top five countries where Anom devices are currently used are Germany, the Netherlands, Spain, Australia, and Serbia, unsealed court documents show, with its user base having grown significantly in the aftermath of Sky ECC’s disruption.
“After the takedown of Sky ECC in March 2021, many organised crime networks sought a quick encrypted replacement for a communication platform that would allow them to evade law enforcement detection,” Europol said. “This was a deliberate and strategic aspect of OTF Greenlight / Operation Trojan Shield resulting in the migration of some of the criminal Sky ECC customer base to the FBI-managed platform ANoM.”
The international coalition that participated in the joint operation consisted of Australia, Austria, Canada, Denmark, Estonia, Finland, Germany, Hungary, Lithuania, New Zealand, the Netherlands, Norway, Sweden, the U.K. (including Scotland), and the U.S.
“A goal of the Trojan Shield investigation is to shake the confidence in this entire industry because the FBI is willing and able to enter this space and monitor messages,” per the court documents.