An advanced persistent threat (APT) actor has been tracked in a new campaign deploying Android malware via the Syrian e-Government Web Portal, indicating an upgraded arsenal designed to compromise victims.
“To the best of our knowledge, this is the first time that the group has been publicly observed using malicious Android applications as part of its attacks,” Trend Micro researchers Zhengyu Dong, Fyodor Yarochkin, and Steven Du said in a technical write-up published Wednesday.
StrongPity, also codenamed Promethium by Microsoft, is believed to have been active since 2002 and has typically focused on targets across Turkey and Syria. In June 2020, the espionage threat actor was connected to a wave of activities that banked on watering hole attacks and tampered installers, which abuse the popularity of legitimate applications, to infect targets with malware.
“Promethium has been resilient over the years,” Cisco Talos disclosed last year. “Its campaigns have been exposed several times, but that was not enough to make the actors behind it to make them stop. The fact that the group does not refrain from launching new campaigns even after being exposed shows their resolve to accomplish their mission.”
The latest operation is no different in that it underscores the threat actor’s propensity towards repackaging benign applications into trojanized variants to facilitate the attacks.
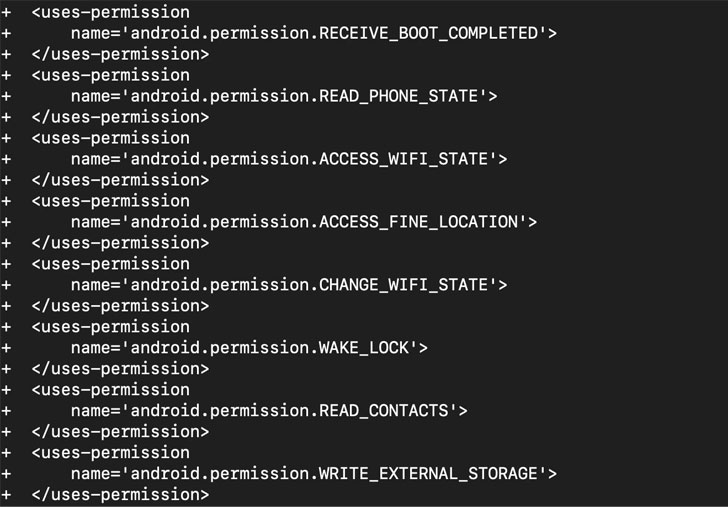
The malware, masquerading as the Syrian e-Gov Android application, is said to have been created in May 2021, with the app’s manifest file (“AndroidManifest.xml“) modified to explicitly request additional permissions on the phone, including the ability to read contacts, write to external storage, keep the device awake, access information about cellular and Wi-Fi networks, precise location, and even allow the app to have itself started as soon as the system has finished booting.
Additionally, the malicious app is designed to perform long-running tasks in the background and trigger a request to a remote command-and-control (C2) server, which responds back with an encrypted payload containing a settings file that allows the “malware to change its behavior according to the configuration” and update its C2 server address.
Last but not least, the “highly modular” implant has the capacity to hoover data stored on the infected device, such as contacts, Word and Excel documents, PDFs, images, security keys, and files saved using Dagesh Pro Word Processor (.DGS), among others, all of which are exfiltrated back to the C2 server.
Despite no known public reports of StrongPity using malicious Android applications in their attacks, Trend Micro’s attribution to the adversary stems from the use of a C2 server that has previously been used in intrusions linked to the hacking group, notably a malware campaign documented by AT&T’s Alien Labs in July 2019 that leveraged tainted versions of the WinBox router management software, WinRAR, and other trusted utilities to breach targets.
“We believe that the threat actor is exploring multiple ways of delivering the applications to potential victims, such as using fake apps and using compromised websites as watering holes to trick users into installing malicious applications,” the researchers said.
“Typically, these websites would require its users to download the applications directly onto their devices. In order to do so, these users would be required to enable installation of the applications from ‘unknown sources’ on their devices. This bypasses the ‘trust-chain’ of the Android ecosystem and makes it easier for an attacker to deliver additional malicious components,” they added.