Amazon earlier this April addressed a critical vulnerability in its Kindle e-book reader platform that could have been potentially exploited to take full control over a user’s device, resulting in the theft of sensitive information by just deploying a malicious e-book.
“By sending Kindle users a single malicious e-book, a threat actor could have stolen any information stored on the device, from Amazon account credentials to billing information,” Yaniv Balmas, head of cyber research at Check Point, said in an emailed statement. “The security vulnerabilities allow an attacker to target a very specific audience.”
In other words, if a threat actor wanted to single out a specific group of people or demographic, it’s possible for the adversary to choose a popular e-book in a language or dialect that’s widely spoken among the group to tailor and orchestrate a highly targeted cyber attack.
Upon responsibly disclosing the issue to Amazon in February 2021, the retail and entertainment giant published a fix as part of its 5.13.5 version of Kindle firmware in April 2021.
Attacks exploiting the flaw commence by sending a malicious e-book to an intended victim, who, upon opening the book, triggers the infection sequence sans any interaction, allowing the bad actor to delete the user’s library, gain full access to the Amazon account, or convert the Kindle into a bot for striking other devices in the target’s local network.
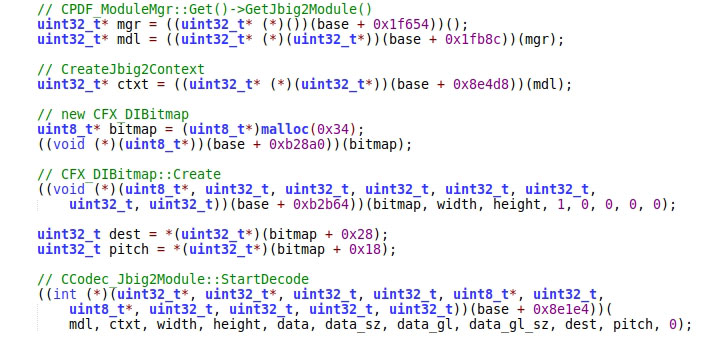 |
| Heap overflow vulnerability in the JBIG2Globals decoding algorithm |
The problem resides in the firmware’s e-book parsing framework, specifically in the implementation associated with how PDF documents are opened, permitting an attacker to execute a malicious payload on the device.
This is made possible, thanks to a heap overflow vulnerability in the PDF rendering function (CVE-2021-30354), which can be leveraged to gain arbitrary write primitive, and a local privilege escalation flaw in the Kindle application manager service (CVE-2021-30355) that enables the threat actor to chain the two flaws to run malware-laced code as a root user.
Earlier this January, Amazon fixed similar weaknesses — collectively named “KindleDrip” — that could have allowed an attacker to take control of victims’ devices by delivering a malicious e-book to the targets and make unauthorized purchases.
“Kindle, like other IoT devices, are often thought of as innocuous and disregarded as security risks,” Balmas said. “These IoT devices are vulnerable to the same attacks as computers. Everyone should be aware of the cyber risks in using anything connected to the computer, especially something as ubiquitous as Amazon’s Kindle.”


