A Chinese cyber espionage group has been linked to a string of intrusion activities targeting Israeli government institutions, IT providers, and telecommunications companies at least since 2019.
FireEye’s Mandiant threat intelligence arm attributed the campaign to an operator it tracks as “UNC215”, a Chinese espionage operation that’s believed to have singled out organizations around the world dating back as far as 2014, linking the group with “low confidence” to an advanced persistent threat (APT) widely known as APT27, Emissary Panda, or Iron Tiger.
“UNC215 has compromised organizations in the government, technology, telecommunications, defense, finance, entertainment, and health care sectors,” FireEye’s Israel and U.S. threat intel teams said in a report published today.
“The group targets data and organizations which are of great interest to Beijing’s financial, diplomatic, and strategic objectives,” the findings reflecting a relentless appetite for defense-related secrets among hacking groups.
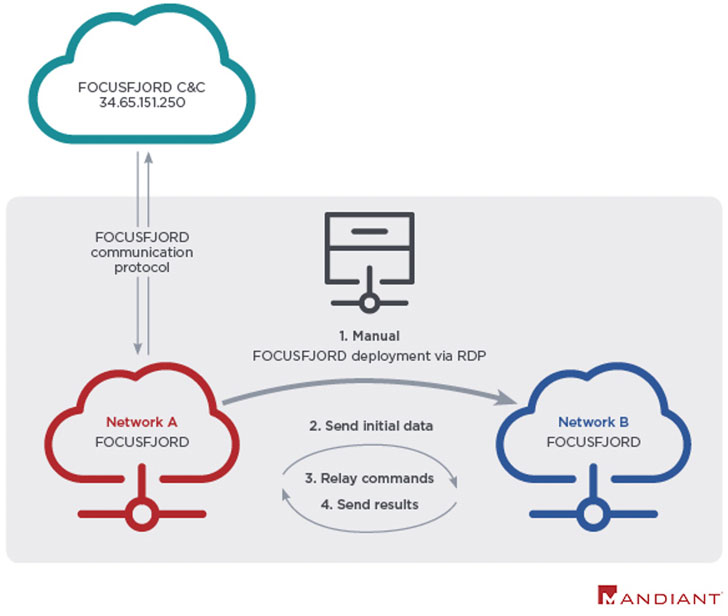
Early attacks perpetrated by the collective is said to have exploited a Microsoft SharePoint vulnerability (CVE-2019-0604) as a stepping stone toward infiltrating government and academic networks to deploy web shells and FOCUSFJORD payloads at targets in the Middle East and Central Asia. First described by the NCC Group in 2018, FOCUSFJORD, also called HyperSSL and Sysupdate, is a backdoor that’s part of an arsenal of tools put to use by the Emissary Panda actor.
Upon gaining an initial foothold, the adversary follows an established pattern of conducting credential harvesting and internal reconnaissance to identify key systems within the target network, before carrying out lateral movement activities to install a custom implant called HyperBro that comes with capabilities such as screen capture and keylogging.
Each phase of the attack is marked by notable efforts undertaken to hinder detection by removing any traces of residual forensic artifacts from compromised machines, while simultaneously improving the FOCUSFJORD backdoor in response to security vendor reports, concealing command-and-control (C2) infrastructure by using other victim networks to proxy their C2 instructions, and even incorporating false flags such as deploying a web shell called SEASHARPEE that’s associated with Iranian APT groups in an attempt to mislead attribution.
What’s more, in a 2019 operation against an Israeli government network, UNC215 obtained access to the primary target via remote desktop protocol (RDP) connections from a trusted third-party using stolen credentials, abusing it to deploy and remotely execute the FOCUSFJORD malware, the cybersecurity firm noted.
“The activity […] demonstrates China’s consistent strategic interest in the Middle East,” the researchers concluded. “This cyber espionage activity is happening against the backdrop of China’s multi-billion-dollar investments related to the Belt and Road Initiative (BRI) and its interest in Israeli’s robust technology sector.”
“China has conducted numerous intrusion campaigns along the BRI route to monitor potential obstructions—political, economic, and security—and we anticipate that UNC215 will continue targeting governments and organizations involved in these critical infrastructure projects in Israel and the broader Middle East in the near- and mid-term,” the teams added.