Attackers are using many types of attacks to compromise business-critical data. These can include zero-day attacks, supply chain attacks, and others. However, one of the most common ways that hackers get into your environment is by compromising passwords.
The password spraying attack is a special kind of password attack that can prove effective in compromising your environment. Let’s look closer at the password spraying attack and how organizations can prevent it.
Beware of compromised credentials
Are compromised credentials dangerous to your environment? Yes! Compromised credentials allow an attacker to “walk in the front door” of your environment with legitimate credentials. They assume all the rights and permissions to systems, data, and resources the compromised account can access.
The compromise of a privileged account is even worse. Privileged accounts are accounts that have high levels of access, such as an administrator user account. These types of accounts represent the “holy grail” to an attacker as they generally have the “keys to the kingdom” in terms of access. For example, with an administrator account, an attacker can not only access systems but can also create other backdoors and high-level accounts that may be difficult to detect.
According to the IBM Cost of a Data Breach Report 2021, “the most common initial attack vector in 2021 was compromised credentials, responsible for 20% of breaches.” It continues: “Breaches caused by stolen/compromised credentials took the longest number of days to identify (250) and contain (91) on average, for an average total of 341 days.”
The longer it takes to identify an attack, they are more costly and damaging to a business, leading to an increased risk of a tarnished reputation and lost business.
What is a password spraying attack?
The password spraying attack is a slightly different take on the brute force attack. In a typical brute force attack, an attacker tries an exponential number of passwords against a single account to crack that single account. With the password spraying attack, the attacker “sprays” multiple accounts with the same password.
Many businesses use Microsoft Active Directory Domain Services (ADDS) and account lockout policies. With the account lockout policy, administrators can set the number of failed login attempts before the account locks out for a specified duration. For example, lockout policies configure a low number of failed login attempts, such as five failed login attempts. The advantage of password spraying is that the attacker spreads the attack out over multiple accounts, which helps avoid account lockouts.
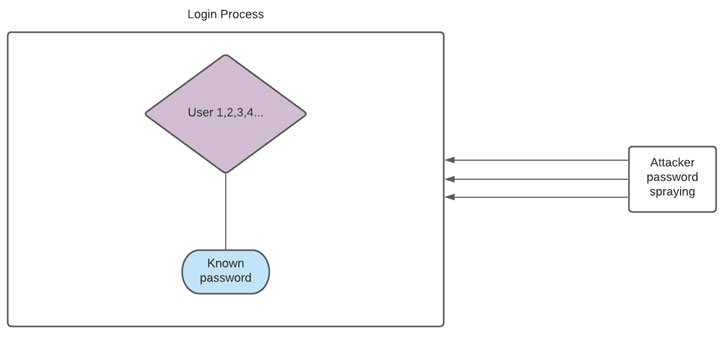 |
| Password spraying attacks target multiple user accounts with a single commonly used password |
Attackers may target an environment with common passwords that are found as password defaults or found in known or breached password lists. If an attacker sprays these passwords across many user accounts, they are likely to find a user account configured with a known, breached, or default password.
Prevent password spraying attacks
Any credential compromise is undoubtedly a cybersecurity event that companies want to avoid at all costs. Password spraying is another tool in the attack arsenal of cybercriminals used to breach valuable or sensitive data. What steps can organizations take to prevent password spraying attacks in particular?
As with many cybersecurity threats, there is no one “silver bullet” that prevents all types of attacks. Instead, password security involves a multi-layered approach that includes many mitigations. So, what do these mitigations include?
- Enforce account lockout policies limiting bad password attempts
- Effective password policies enforcing good password hygiene
- Use breached password protection
- Implement multi-factor authentication
1 — Enforce account lockout policies limiting bad password attempts
As mentioned earlier, account lockout policies prevent an attacker from trying an infinite number of passwords against an account until they crack the password.
Organizations can configure a threshold of bad password attempts that lock the account for a specific time with an account lockout policy.
While a password spraying attack attempts to bypass this mitigation and can prove successful, password lockout policies are a good line of defense against brute force attacks in general. Current cybersecurity best-practice standards recommend implementing password lockout policies.
2 — Effective password policies enforcing good password hygiene
Password policies control the characteristics of passwords used in an environment. Weak passwords or passwords that are easily guessed are extremely dangerous for businesses for obvious reasons, but particularly the incredibly high cost of recovery.
Password policies allow companies to define the length, complexity, and content of passwords in their environments. Microsoft’s Active Directory Domain Services allow creating basic password policies used by most enterprise organizations today.
However, it is limited in providing modern password policy features recommended, such as breached password protection and advanced password policy features. As a result, businesses must implement third-party solutions to effectively prevent the use of breached passwords and other weak passwords in the environment.
3 — Use breached password protection
Breached password protection is an essential cybersecurity protection mechanism for password credentials. Attackers can use previously breached password lists to attempt breaching the current accounts maintained by organizations. How does this work?
Attackers know that different end-users commonly use the same passwords. Due to human nature, we all tend to think alike. Therefore, users tend to think of and use the same types of passwords. It means that lists of breached passwords most likely contain passwords that other users currently use for their user accounts.
Implementing breached password protection means that organizations are scanning their Active Directory environments for passwords that have been found on breached password lists. However, as mentioned earlier, breached password protection is not a feature natively found in Active Directory. So, organizations must use third-party tools to implement this protection effectively.
4 — Implement multi-factor authentication
Along with strong passwords with breached password protection, organizations do well to implement multi-factor authentication. Multi-factor authentication combines something you know (your password) with something you have (a hardware authentication device).
Multi-factor authentication such as two-factor makes it exponentially harder for attackers to compromise credentials. Even if they guess or possess the password via a breach, they still do not have everything needed to authenticate (the second factor, such as a hardware device).
Modern password protection
For businesses looking to implement modern password protection in their Active Directory environment, third-party tools are needed to protect against breached passwords and bolster default Active Directory password policies. By increasing the cybersecurity posture by having more robust password protection, organizations can help to prevent password spraying attacks.
Specops Password Policy is a solution that allows organizations to improve their password security significantly. It provides built-in Breached Password Protection and the ability to implement multiple password dictionaries that include disallowed passwords customized for your business.
Recently Specops has introduced an update to the Breached Password Protection module that includes live attack data. It means that Breached Password Protection protects you from passwords observed as breached in actual attacks. With this new feature, customers can be protected from passwords in breached password dictionaries and live attacks.
Below notes the ability to create custom dictionaries and make use of downloadable dictionaries.
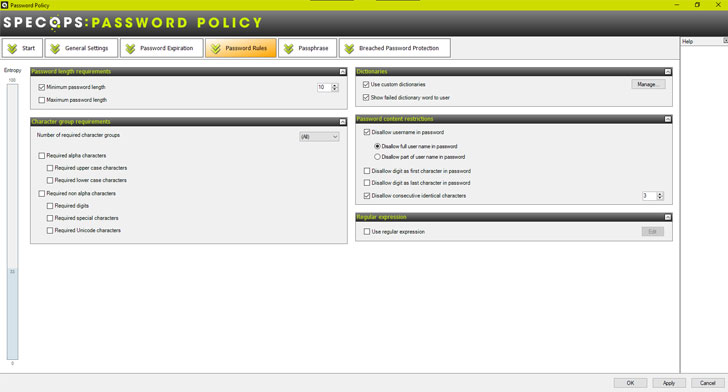 |
| Custom password dictionaries available in Specops Password Policy |
Specops provides robust Breached Password Protection with the real-time Breached Password API.
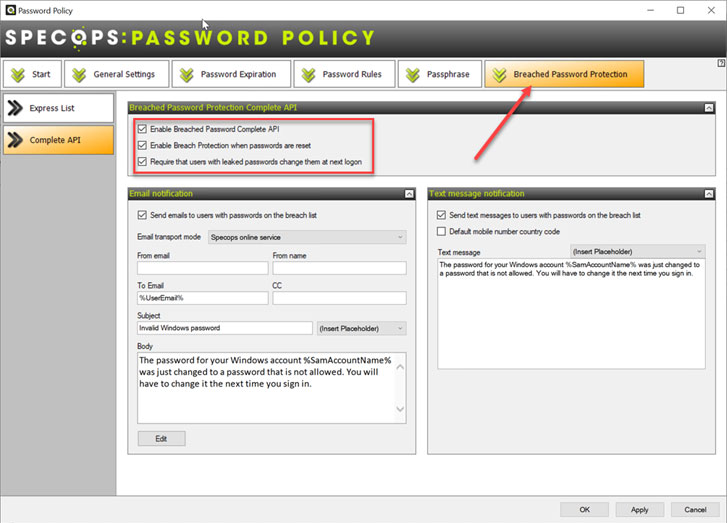 |
| Breached password protection in Specops Password Policy |
Wrapping Up
Credential theft is a dangerous risk for organizations resulting in more costly and lengthy breach events. Attackers often use password spraying attacks to compromise accounts with known passwords and avoid the password lockout policy.
Specops Password Policy helps businesses to implement the best practice recommendations needed for a modern cybersecurity posture. It includes breached password protection, password dictionaries, and robust password policy capabilities above and beyond native features in Active Directory.
In addition, its breached password protection service includes a new addition of live attack data that protects businesses from real password spray attacks happening right now.
Learn more about Specops Password Policy and download a free trial here.
