A new social engineering-based malvertising campaign targeting Japan has been found to deliver a malicious application that deploys a banking trojan on compromised Windows machines to steal credentials associated with cryptocurrency accounts.
The application masquerades as an animated porn game, a reward points application, or a video streaming application, Trend Micro researchers Jaromir Horejsi and Joseph C Chen said in an analysis published last week, attributing the operation to a threat actor it tracks as Water Kappa, which was previously found targeting Japanese online banking users with the Cinobi trojan by leveraging exploits in Internet Explorer browser.
The switch in tactics is an indicator that the adversary is singling out users of web browsers other than Internet Explorer, the researchers added.
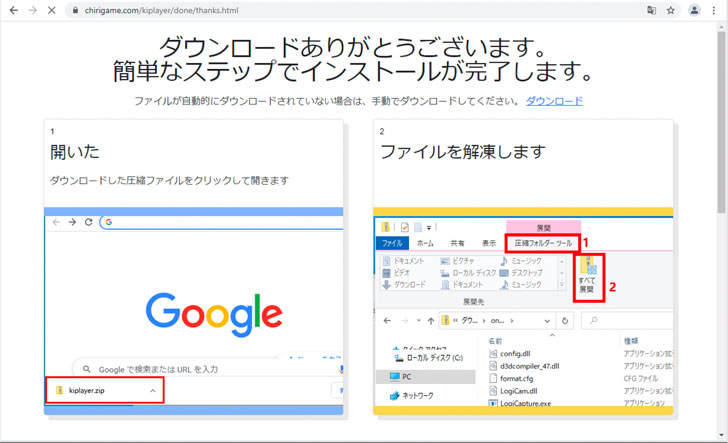
Water Kappa’s latest infection routine commences with malvertisements for either Japanese animated porn games, reward points apps, or video streaming services, with the landing pages urging the victim to download the application — a ZIP archive containing files from an older version of the “Logitech Capture” application dated 2018, but also featuring modified files that are orchestrated to decrypt and run shellcode that, in turn, triggers the execution of the Cinobi banking trojan.
In addition to geofencing access to the malvertisement portals from non-Japanese IP addresses, the trojan is designed to pilfer usernames and passwords for 11 Japanese financial institutions, three of which are involved in cryptocurrency trading. In the event, a user visits one of the targeted websites, Cinobi’s form-grabbing module is activated to capture the filled-in information in the login screens.
“The new malvertising campaign shows that Water Kappa is still active and continuously evolving their tools and techniques for greater financial gain — this one also aims to steal cryptocurrency,” the researchers said. “In order to minimise the chances of being infected, users need to be wary of suspicious advertisements on shady websites, and as much as possible, download applications only from trusted sources.”