ShadowPad, an infamous Windows backdoor that allows attackers to download further malicious modules or steal data, has been put to use by five different Chinese threat clusters since 2017.
“The adoption of ShadowPad significantly reduces the costs of development and maintenance for threat actors,” SentinelOne researchers Yi-Jhen Hsieh and Joey Chen said in a detailed overview of the malware, adding “some threat groups stopped developing their own backdoors after they gained access to ShadowPad.”
The American cybersecurity firm dubbed ShadowPad a “masterpiece of privately sold malware in Chinese espionage.”
A successor to PlugX and a modular malware platform since 2015, ShadowPad catapulted to widespread attention in the wake of supply chain incidents targeting NetSarang, CCleaner, and ASUS, leading the operators to shift tactics and update their defensive measures with advanced anti-detection and persistence techniques.
More recently, attacks involving ShadowPad have singled out organizations in Hong Kong as well as critical infrastructure in India, Pakistan, and other Central Asian countries. Although primarily attributed to APT41, the implant is known to be shared among several Chinese espionage actors such as Tick, RedEcho, RedFoxtrot, and clusters dubbed Operation Redbonus, Redkanku, and Fishmonger.
“[The threat actor behind Fishmonger is] now using it and another backdoor called Spyder as their primary backdoors for long-term monitoring, while they distribute other first-stage backdoors for initial infections including FunnySwitch, BIOPASS RAT, and Cobalt Strike,” the researchers said. “The victims include universities, governments, media sector companies, technology companies and health organizations conducting COVID-19 research in Hong Kong, Taiwan, India and the U.S.”
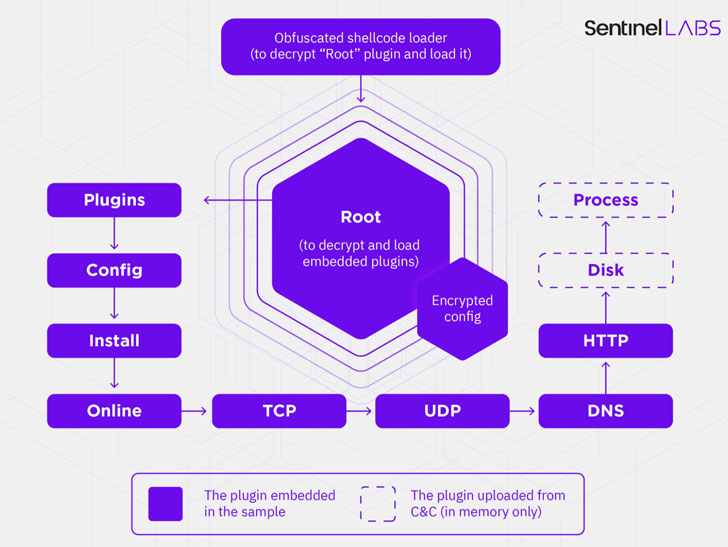
The malware functions by decrypting and loading a Root plugin in memory, which takes care of loading other embedded modules during runtime, in addition to dynamically deploying additional plugins from a remote command-and-control (C2) server, enabling adversaries to incorporate extra functionality not built into the malware by default. At least 22 unique plugins have been identified to date.
The infected machines, for their part, are commandeered by a Delphi-based controller that’s used for backdoor communications, updating the C2 infrastructure, and managing the plugins.
Interestingly, the feature set made available to ShadowPad users is not only tightly controlled by its seller, each plugin is sold separately instead of offering a full bundle containing all of the modules, with most samples — out of about 100 — embedded with less than nine plugins.
“The emergence of ShadowPad, a privately sold, well-developed and functional backdoor, offers threat actors a good opportunity to move away from self-developed backdoors,” the researchers said. “While it is well-designed and highly likely to be produced by an experienced malware developer, both its functionalities and its anti-forensics capabilities are under active development.”