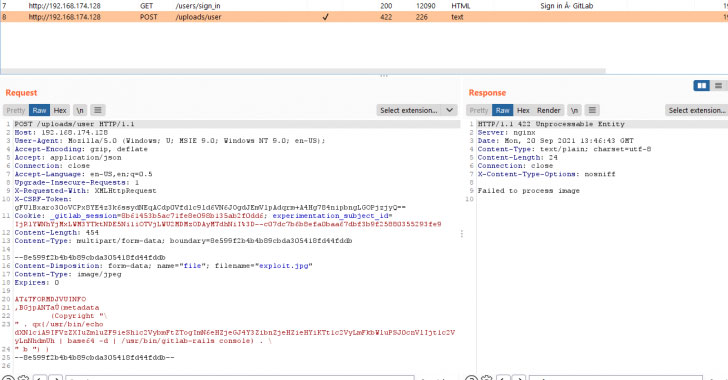
A now-patched critical remote code execution (RCE) vulnerability in GitLab’s web interface has been detected as actively exploited in the wild, cybersecurity researchers warn, rendering a large number of internet-facing GitLab instances susceptible to attacks.
Tracked as CVE-2021-22205, the issue relates to an improper validation of user-provided images that results in arbitrary code execution. The vulnerability, which affects all versions starting from 11.9, has since been addressed by GitLab on April 14, 2021 in versions 13.8.8, 13.9.6, and 13.10.3.
In one of the real-world attacks detailed by HN Security last month, two user accounts with admin privileges were registered on a publicly-accessible GitLab server belonging to an unnamed customer by exploiting the aforementioned flaw to upload a malicious payload that leads to remote execution of arbitrary commands, including obtaining elevated permissions.
Although the flaw was initially deemed to be a case of authenticated RCE and assigned a CVSS score of 9.9, the severity rating was revised to 10.0 on September 21, 2021 owing to the fact that it can be triggered by unauthenticated threat actors as well.
“Despite the tiny move in CVSS score, a change from authenticated to unauthenticated has big implications for defenders,” cybersecurity firm Rapid7 said in an alert published Monday.
Despite the public availability of the patches for more than six months, of the 60,000 internet-facing GitLab installations, only 21% of the instances are said to be fully patched against the issue, with another 50% still vulnerable to RCE attacks.
In the light of the unauthenticated nature of this vulnerability, exploitation activity is expected to increase, making it critical that GitLab users update to the latest version as soon as possible. “In addition, ideally, GitLab should not be an internet facing service,” the researchers said. “If you need to access your GitLab from the internet, consider placing it behind a VPN.”
Additional technical analysis related to the vulnerability can be accessed here.