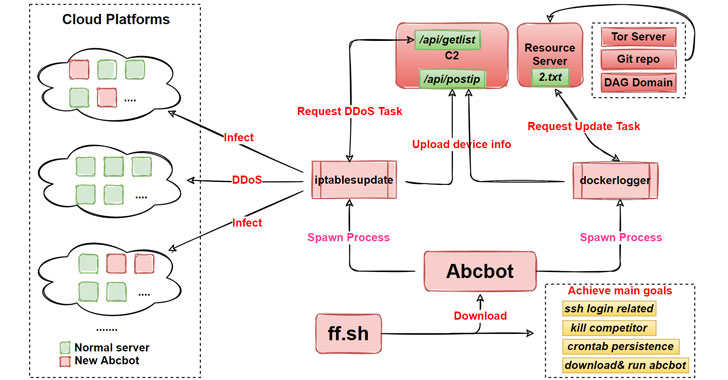
Researchers from Qihoo 360’s Netlab security team have released details of a new evolving botnet called “Abcbot” that has been observed in the wild with worm-like propagation features to infect Linux systems and launch distributed denial-of-service (DDoS) attacks against targets.
While the earliest version of the botnet dates back to July 2021, new variants observed as recently as October 30 have been equipped with additional updates to strike Linux web servers with weak passwords and are susceptible to N-day vulnerabilities, including a custom implementation of DDoS functionality, indicating that the malware is under continuous development.
Netlab’s findings also build on a report from Trend Micro early last month, which publicized attacks targeting Huawei Cloud with cryptocurrency-mining and cryptojacking malware. The intrusions were also notable for the fact that the malicious shell scripts specifically disabled a process designed to monitor and scan the servers for security issues as well as reset users’ passwords to the Elastic cloud service.
Now according to the Chinese internet security company, these shell scripts are being used to spread Abcbot. A total of six versions of the botnet have been observed to date.
Once installed on a compromised host, the malware triggers the execution of a series of steps that results in the infected device being repurposed as a web server, in addition to reporting the system information to a command-and-control (C2) server, spreading the malware to new devices by scanning for open ports, and self-updating itself as and when new features are made available by its operators.
“Interesting thing is that the sample [updated] on October 21 uses the open-source ATK Rootkit to implement the DDoS function,” a mechanism which the researchers said “requires Abcbot to download the source code, compile, and load the rootkit module before performing [a] DDoS attack.”
“This process requires too many steps, and any step that is faulty will result in the failure of the DDoS function,” the researchers noted, leading the adversary to replace the off-the-shelf code with a custom attack module in a subsequent version released on October 30 that completely abandons the ATK rootkit.
The findings come a little over a week after the Netlab security team disclosed details of a “Pink” botnet that’s believed to have infected over 1.6 million devices primarily located in China with the goal of launching DDoS attacks and inserting advertisements into HTTP websites visited by unsuspecting users. In a related development, AT&T Alien Labs took the wraps off a new Golang malware dubbed “BotenaGo” that has been discovered using over thirty exploits to attack millions of routers and IoT devices potentially.
“The update process in these six months is not so much a continuous upgrade of features as a trade-off between different technologies,” the researchers concluded. “Abcbot is slowly moving from infancy to maturity. We do not consider this stage to be the final form, there are obviously many areas of improvement or features to be developed at this stage.”