Threat actors are exploiting ProxyLogon and ProxyShell exploits in unpatched Microsoft Exchange Servers as part of an ongoing spam campaign that leverages stolen email chains to bypass security software and deploy malware on vulnerable systems.
The findings come from Trend Micro following an investigation into a number of intrusions in the Middle East that culminated in the distribution of a never-before-seen loader dubbed SQUIRRELWAFFLE. First publicly documented by Cisco Talos, the attacks are believed to have commenced in mid-September 2021 via laced Microsoft Office documents.
“It is known for sending its malicious emails as replies to pre-existing email chains, a tactic that lowers a victim’s guard against malicious activities,” researchers Mohamed Fahmy, Sherif Magdy, Abdelrhman Sharshar said in a report published last week. “To be able to pull this off, we believe it involved the use of a chain of both ProxyLogon and ProxyShell exploits.”
ProxyLogon and ProxyShell refer to a collection of flaws in Microsoft Exchange Servers that could enable a threat actor to elevate privileges and remotely execute arbitrary code, effectively granting the ability to take control of the vulnerable machines. While the ProxyLogon flaws were addressed in March, the ProxyShell bugs were patched in a series of updates released in May and July.
 |
| DLL infection flow |
Trend Micro said it observed the use of public exploits for CVE-2021-26855 (ProxyLogon), CVE-2021-34473, and CVE-2021-34523 (ProxyShell) on three of the Exchange servers that were compromised in different intrusions, using the access to hijack legitimate email threads and send malicious spam messages as replies, thereby increasing the likelihood that unsuspecting recipients will open the emails.
“Delivering the malicious spam using this technique to reach all the internal domain users will decrease the possibility of detecting or stopping the attack, as the mail getaways will not be able to filter or quarantine any of these internal emails,” the researchers said, adding the attackers behind the operation did not carry out lateral movement or install additional malware so as to stay under the radar and avoid triggering any alerts.
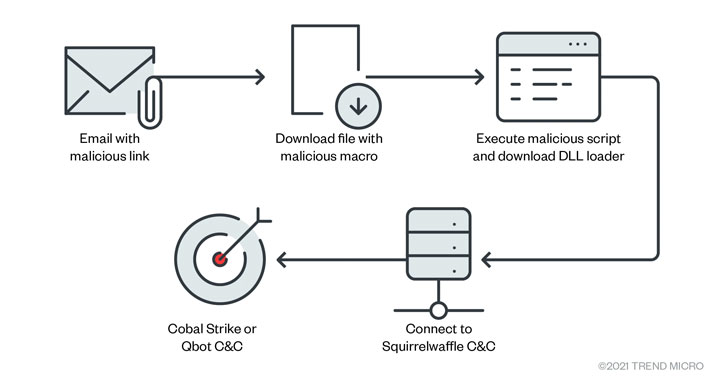
The attack chain involves rogue email messages containing a link that, when clicked, drops a Microsoft Excel or Word file. Opening the document, in turn, prompts the recipient to enable macros, ultimately leading to the download and execution of the SQUIRRELWAFFLE malware loader, which acts as a medium to fetch final-stage payloads such as Cobalt Strike and Qbot.
“SQUIRRELWAFFLE campaigns should make users wary of the different tactics used to mask malicious emails and files,” the researchers concluded. “Emails that come from trusted contacts may not be enough of an indicator that whatever link or file included in the email is safe.”