Researchers have unearthed a new remote access trojan (RAT) for Linux that employs a never-before-seen stealth technique that involves masking its malicious actions by scheduling them for execution on February 31st, a non-existent calendar day.
Dubbed CronRAT, the sneaky malware “enables server-side Magecart data theft which bypasses browser-based security solutions,” Sansec Threat Research said. The Dutch cybersecurity firm said it found samples of the RAT on several online stores, including an unnamed country’s largest outlet.
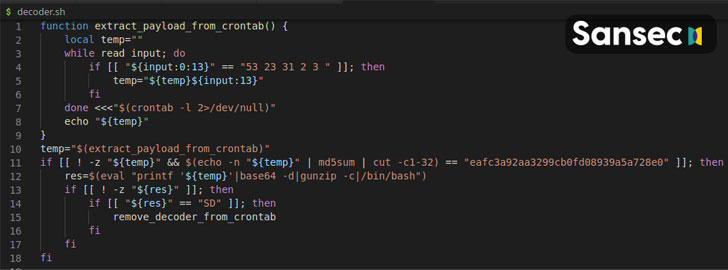
CronRAT’s standout feature is its ability to leverage the cron job-scheduler utility for Unix to hide malicious payloads using task names programmed to execute on February 31st. Not only does this allow the malware to evade detection from security software, but it also enables it to launch an array of attack commands that could put Linux eCommerce servers at risk.
“The CronRAT adds a number of tasks to crontab with a curious date specification: 52 23 31 2 3,” the researchers explained. “These lines are syntactically valid, but would generate a run time error when executed. However, this will never happen as they are scheduled to run on February 31st.”
The RAT — a “sophisticated Bash program” — also uses many levels of obfuscation to make analysis difficult, such as placing code behind encoding and compression barriers, and implementing a custom binary protocol with random checksums to slip past firewalls and packet inspectors, before establishing communications with a remote control server to await further instructions.
Armed with this backdoor access, the attackers associated with CronRAT can run any code on the compromised system, the researchers noted.
“Digital skimming is moving from the browser to the server and this is yet another example,” Sansec’s Director of Threat Research, Willem de Groot, said. “Most online stores have only implemented browser-based defenses, and criminals capitalize on the unprotected back-end. Security professionals should really consider the full attack surface.”