A security flaw has been unearthed in Microsoft’s Azure App Service that resulted in the exposure of source code of customer applications written in Java, Node, PHP, Python, and Ruby for at least four years since September 2017.
The vulnerability, codenamed “NotLegit,” was reported to the tech giant by Wiz researchers on October 7, 2021, following which mitigations have been undertaken to fix the information disclosure bug in November. Microsoft said a “limited subset of customers,” adding “Customers who deployed code to App Service Linux via Local Git after files were already created in the application were the only impacted customers.”
The Azure App Service (aka Azure Web Apps) is a cloud computing-based platform for building and hosting web applications. It allows users to deploy source code and artifacts to the service using a local Git repository, or via repositories hosted on GitHub and Bitbucket.
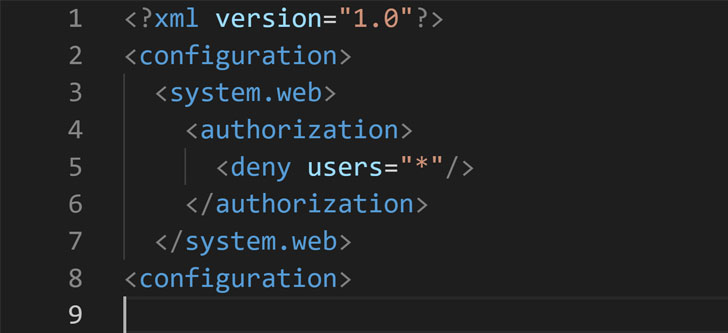
The insecure default behavior occurs when the Local Git method is used to deploy to Azure App Service, resulting in a scenario where the Git repository is created within a publicly accessible directory (home/site/wwwroot).
While Microsoft does add a “web.config” file to the .git folder — which contains the state and history of the repository — to restrict public access, the configuration files are only used with C# or ASP.NET applications that rely on Microsoft’s own IIS web servers, leaving out apps coded in other programming languages like PHP, Ruby, Python, or Node that are deployed with different web servers like Apache, Nginx, and Flask.
“Basically, all a malicious actor had to do was to fetch the ‘/.git’ directory from the target application, and retrieve its source code,” Wiz researcher Shir Tamari said. “Malicious actors are continuously scanning the internet for exposed Git folders from which they can collect secrets and intellectual property. Besides the possibility that the source contains secrets like passwords and access tokens, leaked source code is often used for further sophisticated attacks.”
“Finding vulnerabilities in software is much easier when the source code is available,” Tamari added.