Cybersecurity researchers are warning of “massive phishing campaigns” that distribute five different malware targeting banking users in India.
“The bank customers targeted include account subscribers of seven banks, including some of the most well-known banks located in the country and potentially affecting millions of customers,” Trend Micro said in a report published this week.
Some of the targeted banks include Axis Bank, ICICI Bank, and the State Bank of India (SBI), among others.
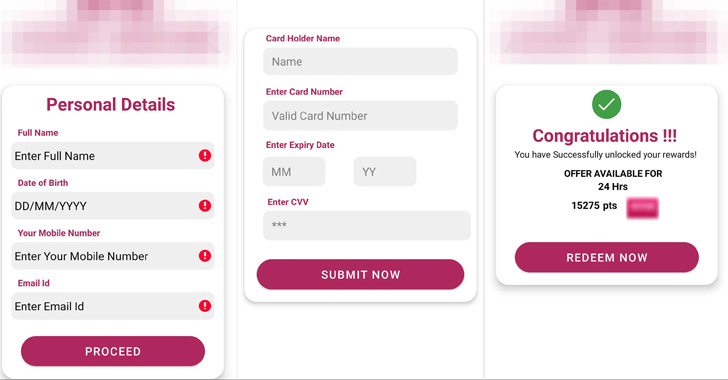
The infection chains all have a common entry point in that they rely on SMS messages containing a phishing link that urge potential victims to enter their personal details and credit card information to supposedly get a tax refund or gain credit card reward points.
The smishing attacks, which deliver Elibomi, FakeReward, AxBanker, IcRAT, and IcSpy, are just the latest in a series of similar rewards-themed malware campaigns that have been documented by Microsoft, Cyble, and K7 Labs over the past year.
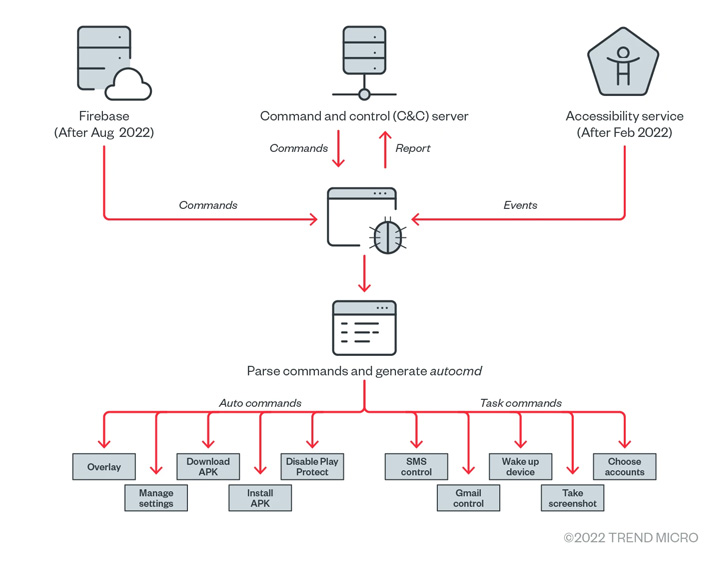
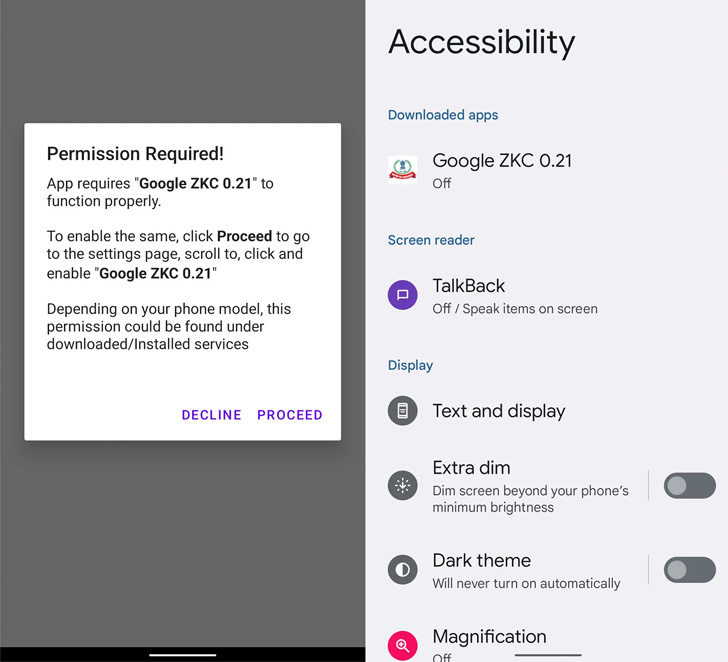
Elibomi, first documented by McAfee in September 2021, is engineered to steal personal data, take screenshots, and even capture the lock screen code or pattern by abusing Android’s accessibility API permissions, enabling it to seize control of the compromised devices.
The mobile malware has undergone numerous revisions, with a new variant of Elibomi called Drinik observed impersonating the Income Tax Department of India to target users of 18 different banks.
“Elibomi implements an overlay by adding a view to the current window as an evasion technique from users, instead of having an overlay on other apps such as bank applications to steal users’ credentials,” the researchers said.
In a similar vein, the FakeReward and AxBanker banking trojans, once installed, prompt the victim to grant it permissions to access SMSes and notifications, which are then leveraged to exfiltrate incoming SMS messages. AxBanker further displays fake pages to siphon credit card information.
The apps themselves are delivered through phishing websites with domain names similar to that of their legitimate counterparts, in addition to reusing the brand logos to increase the likelihood of a successful attack and trick the user into downloading the malicious app to get “instant reward points.”
The similarity in stolen data and phishing themes notwithstanding, Trend Micro said there is no concrete evidence tying all these malware families to a single threat actor.
“While no other customers outside India have been targeted by these malware families, phishing campaigns in the country have significantly increased and are increasingly becoming adept at detection evasion,” Trend Micro noted.
“One possible reason for this uptick is the growing number of new threat actors entering the India underground market, bringing with them profitable business models, and interacting with other malicious players to learn, exchange ideas from, and establish connections.”