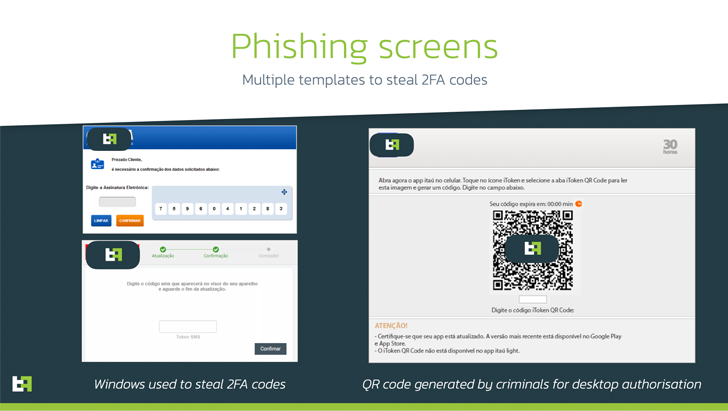
The threat actors behind the Windows banking malware known as Casbaneiro has been attributed as behind a novel Android trojan called BrasDex that has been observed targeting Brazilian users as part of an ongoing multi-platform campaign.
BrasDex features a “complex keylogging system designed to abuse Accessibility Services to extract credentials specifically from a set of Brazilian targeted apps, as well as a highly capable Automated Transfer System (ATS) engine,” ThreatFabric said in a report published last week.
The Dutch security firm said that the command-and-control (C2) infrastructure used in conjunction with BrasDex is also being used to control Casbaneiro, which is known to strike banks and cryptocurrency services in Brazil and Mexico.
The hybrid Android and Windows malware campaign is estimated to have resulted in thousands of infections to date.
BrasDex, which masquerades as a banking app for Banco Santander, is also emblematic of a new trend that involves abusing Android’s Accessibility APIs to log keystrokes entered by the victims, moving away from the traditional method of overlay attacks to steal credentials and other personal data.
It’s also engineered to capture account balance information, subsequently using it to take over infected devices and initiate fraudulent transactions in a programmatic manner.
Another notable aspect of BrasDex is its singular focus on the PIX payments platform, which allows banking customers in Brazil to make money transfers simply using their email addresses or phone numbers.
The ATS system in BrasDex is explicitly designed to abuse PIX technology to make fraudulent transfers.
This is not the first time the instant payment ecosystem has been targeted by bad actors. In September 2021, Check Point detailed two Android malware families named PixStealer and MalRhino that tricked users into transferring their entire account balances to an actor-controlled one.
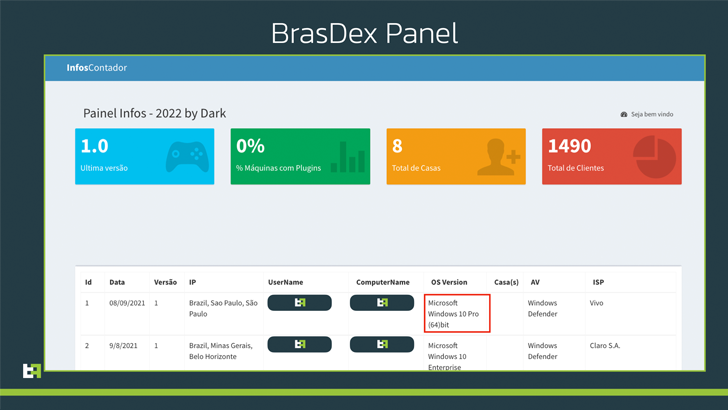
ThreatFabric’s investigation into BrasDex also allowed it to gain access to the C2 panel used by the criminal operators to keep track of the infected devices and retrieve data logs exfiltrated from the Android phones.
The C2 panel, as it happens, is also being utilized to keep tabs on a different malware campaign which compromises Windows machines to deploy Casbaneiro, a Delphi-based financial trojan.
This attack chain employs package delivery-themed phishing lures purporting to be from Correios, a state-owned postal service, to dupe recipients into executing the malware following a multi-staged process.
Casbaneiro’s features run the typical backdoor gamut that allows it to seize control of banking accounts, take screenshots, perform keylogging, hijack clipboard data, and even function as a clipper malware to hijack crypto transactions.
“Being independent and full-fledged malware families, BrasDex and Casbaneiro form a very dangerous pair, allowing the actor behind them to target both Android and Windows users on a large scale,” ThreatFabric said.
“The BrasDex case shows the necessity of fraud detection and prevention mechanisms in place on customers devices: Fraudulent payments made automatically with the help of ATS engines appear legitimate to bank backends and fraud scoring engines, as they are made through the same device that is usually used by customers.”