Cybersecurity researchers have discovered the first-ever illicit cryptocurrency mining campaign used to mint Dero since the start of February 2023.
“The novel Dero cryptojacking operation concentrates on locating Kubernetes clusters with anonymous access enabled on a Kubernetes API and listening on non-standard ports accessible from the internet,” CrowdStrike said in a new report shared with The Hacker News.
The development marks a notable shift from Monero, which is a prevalent cryptocurrency used in such campaigns. It’s suspected it may have to do with the fact that Dero “offers larger rewards and provides the same or better anonymizing features.”
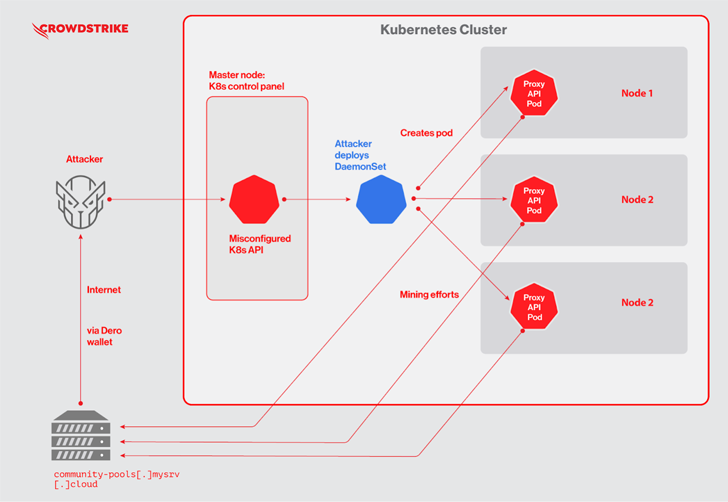
The attacks, attributed to an unknown financially motivated actor, commence with scanning for Kubernetes clusters with authentication set as –anonymous-auth=true, which allows anonymous requests to the server, to drop initial payloads from three different U.S.-based IP addresses.
This includes deploying a Kubernetes DaemonSet named “proxy-api,” which, in turn, is used to drop a malicious pod on each node of the Kubernetes cluster to kick-start the mining activity.
To that end, the DaemonSet’s YAML file is orchestrated to run a Docker image that contains a “pause” binary, which is actually the Dero coin miner.
“In a legitimate Kubernetes deployment, ‘pause’ containers are used by Kubernetes to bootstrap a pod,” the company noted. “Attackers may have used this name to blend in to avoid obvious detection.”
Discover the Hidden Dangers of Third-Party SaaS Apps
Are you aware of the risks associated with third-party app access to your company’s SaaS apps? Join our webinar to learn about the types of permissions being granted and how to minimize risk.
The cybersecurity company said it identified a parallel Monero-mining campaign also targeting exposed Kubernetes clusters by attempting to delete the existing “proxy-api” DaemonSets associated with the Dero campaign.
This is an indication of the ongoing tussle between cryptojacking groups that are vying for cloud resources to take and retain control of the machines and consume all of its resources.
“Both campaigns are trying to find undiscovered Kubernetes attack surfaces and are battling it out,” CrowdStrike threat researchers Benjamin Grap and Manoj Ahuje said.