Remote Access Trojans (RATs) have taken the third leading position in ANY. RUN’s Q1 2023 report on the most prevalent malware types, making it highly probable that your organization may face this threat.
Though LimeRAT might not be the most well-known RAT family, its versatility is what sets it apart. Capable of carrying out a broad spectrum of malicious activities, it excels not only in data exfiltration, but also in creating DDoS botnets and facilitating crypto mining. Its compact footprint allows it to elude endpoint detection systems, making it a stealthy adversary. Interestingly, LimeRAT shares similarities with njRAT, which ANY.RUN ranks as the third most popular malware family in terms of uploads during Q1 2023.
ANY.RUN researchers have recently conducted an in-depth analysis of a LimeRAT sample and successfully extracted its configuration. In this article, we’ll provide a brief overview of that analysis.
Collected artifacts
| SHA1 | 14836dd608efb4a0c552a4f370e5aafb340e2a5d |
| SHA256 | 6d08ed6acac230f41d9d6fe2a26245eeaf08c84bc7a66fddc764d82d6786d334 |
| MD5 | d36f15bef276fd447e91af6ee9e38b28 |
| SSDEEP | 3072:DDiv2GSyn88sH888wQ2wmVgMk/211h36vEcIyNTY4WZd/w1UwIwEoTqPMinXHx+i:XOayy |
IPv4:
| IOC | Description |
| 20[.]199.13.167:8080 | LimeRAT’s Command and Control server |
Domains:
| IOC | Description |
| https://pastebin[.]com/raw/sxNJt2ek | PasteBin used by LimeRAT to hide its original Command and Control server |
MITRE ATT&CK®
| Tactic | Technique | Description |
| TA0005: Defense Evasion | T1027: Obfuscated Files or Information | Malware is using obfuscator to strip its method names, class names, etc. |
| TA0005: Defense Evasion | T1027: Obfuscated Files or Information | Malware uses Base64 algorithm to encode and decode data |
| TA0005: Defense Evasion | T1027: Obfuscated Files or Information | Malware uses AES algorithm to encrypt and decrypt data |
ANY.RUN is running a limited-time offer, celebrating the 7th Cyberbirthdsay
ANY.RUN is an interactive cloud malware sandbox that can extract malware configs automatically for numerous families, saving researchers hours of effort.
The service is celebrating its 7th anniversary and inviting all researchers to try out advanced analysis features typically reserved for pro plans, completely free until May 5th. This includes configuring the execution environment with Windows 8, 10, or 11.
If you discover that ANY.RUN enhances your malware analysis workflow, they are also offering a limited promotion, available until May 5th: receive 6 or 12 months of free usage when you sign up for a yearly or two-year subscription, respectively.
Breaking down LimeRAT’s decryption algorithm
We’ll share a condensed version of the article here. For a complete walkthrough and the extended analysis, head over to ANY. RUN’s blog if you’re interested in learning more about the workflow they employed.
Since the sample under review was written in .NET, researchers utilized DnSpy to examine the code. Immediately, it was obvious that obfuscation techniques were being employed:
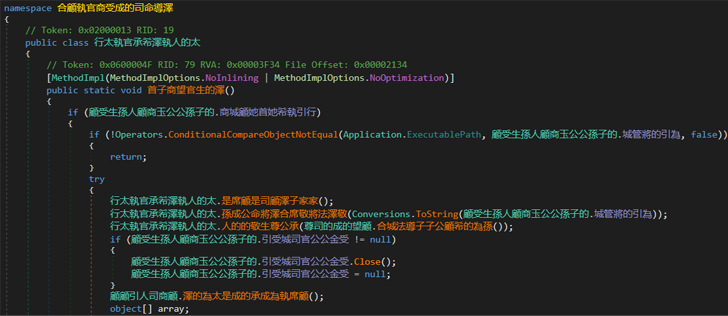 |
| Sample overview in DnSpy; note that use of obfuscation techniques |
Closer examination of the code revealed a class resembling the malware configuration. Within this class, was a field containing a string that was both base64 encoded and encrypted.
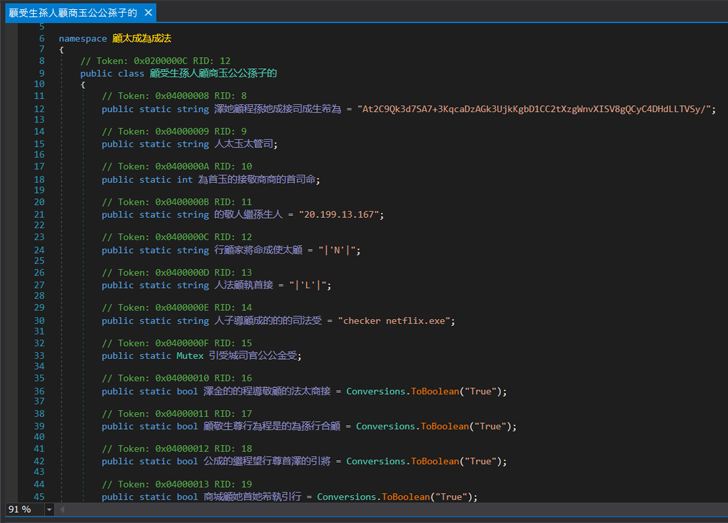 |
| Possibly, malware configuration class |
Continuing the code inspection, ANY.RUN researchers pinpointed a function responsible for decrypting the string. By employing the “Read by” filter in DnSpy, they tracked down methods where the string was being read, which led to a total of two methods. The first method proved unfruitful, but the second one looked interesting:
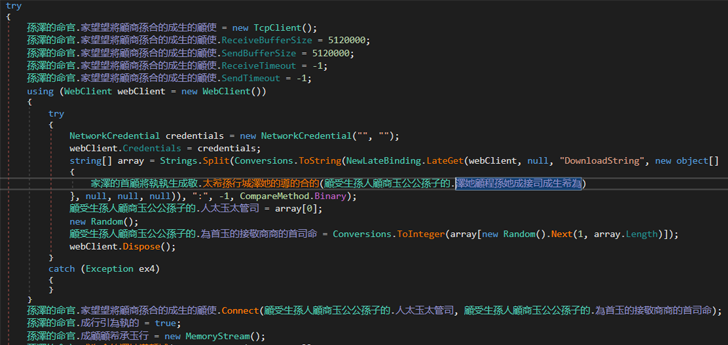 |
| The second x-ref is more interesting. It seems that it uses our string in WebClient.DownloadString method |
This method turned out to be responsible for decryption. By closely examining it, it was possible to reconstruct the process by which LimeRAT decrypts its configuration:
- Instances of the RijndaelManaged and MD5CryptoServiceProvider classes are instantiated. As per MSDN, RijndaelManaged is an outdated implementation of the AES encryption algorithm (MITRE T1027), while MD5CryptoServiceProvider computes MD5 hashes.
- A 32-byte array, initialized with zeros, is generated to store the AES key.
- The key is created by first calculating the MD5 hash of a distinct string within the configuration class (in our analysis, the string is “20[.]199.13.167”).
- The initial 15 bytes, followed by the first 16 bytes of the calculated hash, are copied into the previously established array. The final element of the array remains zero.
- The derived key is assigned to the key property of the RijndaelManaged instance, while the Mode property is configured as CipherMode.ECB.
- Ultimately, the primary string undergoes decoding via the Base64 algorithm and decryption using the AES256-ECB algorithm.
Decrypting the string revealed a link to a PasteBin note: https://pastebin[.]com/raw/sxNJt2ek. Within this note, was LimeRAT’s Command and Control (C2) server:
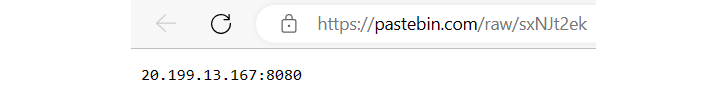 |
| LimeRATs C2 discovered with decrypted data |
To wrap up
We hope you found this brief overview of our LimeRAT configuration decryption process insightful. For a more comprehensive examination, head over to the full article on ANY.RUN’s blog, to get additional context on the steps and check the decryption process using CyberChef.
Also, remember that ANY. RUN’s currently offering limited-time deals, featuring discounts on subscriptions and an expanded feature set for free plans, including the ability to configure execution environments with Windows 8, 10, and 11 operating systems. This offer expires on May 5th.
This is an ideal opportunity to test out ANY.RUN and determine if it streamlines your workflow, or to secure a subscription at an unbeatable price and reap the benefits of significant time savings through static and behavioral analysis.
To learn more about this offer, visit ANY.RUN plans.