Cybersecurity researchers have discovered a new ongoing campaign aimed at the npm ecosystem that leverages a unique execution chain to deliver an unknown payload to targeted systems.
“The packages in question seem to be published in pairs, each pair working in unison to fetch additional resources which are subsequently decoded and/or executed,” software supply chain security firm Phylum said in a report released last week.
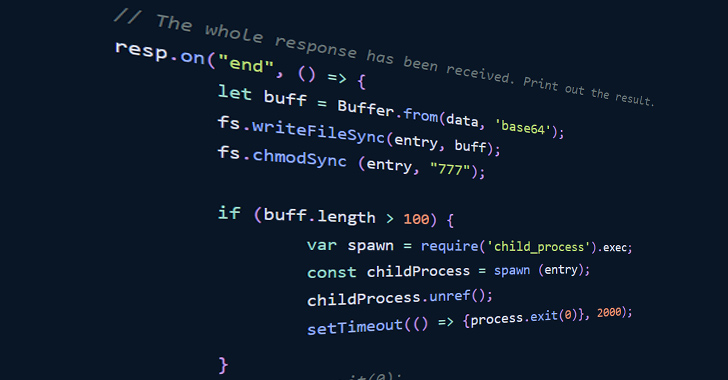
To that end, the order in which the pair of packages are installed is paramount to pulling off a successful attack, as the first of the two modules are designed to store locally a token retrieved from a remote server. The campaign was first discovered on June 11, 2023.
The second package subsequently passes this token as a parameter alongside the operating system type to an HTTP GET request to acquire a second script from the remote server. A successful execution returns a Base64-encoded string that is immediately executed but only if that string is longer than 100 characters.
Phylum revealed that the endpoint has so far returned the string “bm8gaGlzdG9yeSBhdmFpbGFibGU=,” which decodes to “no history available,” either implying that the attack is still a work in progress or it’s engineered to return a payload only at specific times.
Another hypothesis for this behavior could be that it’s dependent on the IP address (and by extension, the location) from which the request originating from the first package is sent when generating the token.
The identity of the threat actor behind the operation is currently not known, although it has all the hallmarks of a “reasonably” sophisticated supply chain threat given the lengths the adversary has gone to execute the attack, while also taking steps to dynamically deliver the next-stage payload to evade detection.
“It’s crucial that each package in a pair is executed sequentially, in the correct order, and on the same machine to ensure successful operation,” Phylum noted. “This carefully orchestrated attack serves as a stark reminder of the ever-evolving complexity of modern threat actors in the open-source ecosystem.”
The disclosure comes as Sonatype uncovered a set of six malicious packages on the Python Package Index (PyPI) repository – broke-rcl, brokescolors, brokescolors2, brokescolors3, brokesrcl, and trexcolors – that were uploaded by a single account named broke.
“These packages target the Windows operating system and are identical with regards to their versioning,” security researcher and journalist Ax Sharma said. “Upon installation, these packages simply download and run a trojan hosted on Discord’s servers.”
Also discovered by Sonatype is a package referred to as libiobe that’s capable of targeting both Windows and Linux operating systems. On machines running Windows, the package delivers an information stealer, whereas on Linux, it’s configured to profile the system and exfiltrate that information back to a Telegram endpoint.
“It is hard to ascertain who would ultimately run packages with such names or who they are specifically targeting,” Sharma noted. “While these packages may not be employing any novel payload or tactics, or have obvious targets, they are a testament to the ongoing malicious attacks that are targeting open source software registries like PyPI and npm.”