The peer-to-peer (P2) worm known as P2PInfect has witnessed a surge in activity since late August 2023, witnessing a 600x jump between September 12 and 19, 2023.
“This increase in P2PInfect traffic has coincided with a growing number of variants seen in the wild, suggesting that the malware’s developers are operating at an extremely high development cadence,” Cado Security researcher Matt Muir said in a report published Wednesday.
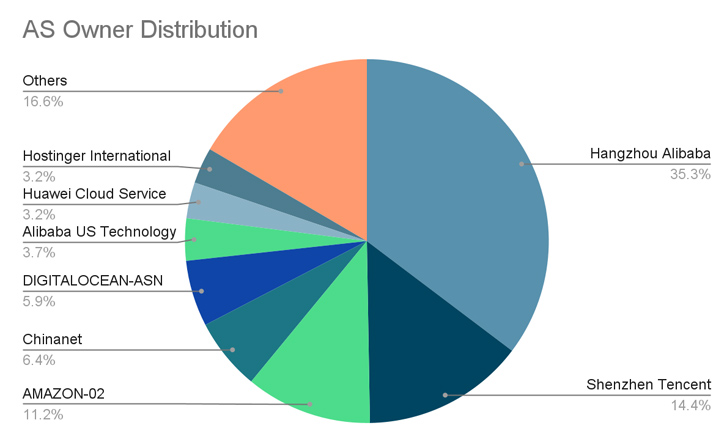
A majority of the compromises have been reported in China, the U.S., Germany, the U.K., Singapore, Hong Kong, and Japan.
P2PInfect first came to light in July 2023 for its ability to breach poorly secured Redis instances. The threat actors behind the campaign have since resorted to different approaches for initial access, including the abuse of the database’s replication feature to deliver the malware.

Cado Security said it has observed an increase in initial access events attributable to P2PInfect in which the Redis SLAVEOF command is issued by an actor-controlled node to a target to enable replication.
This is followed by delivering a malicious Redis module to the target, which, in turn, runs a command to retrieve and launch the main payload, after which another shell command is run to remove the Redis module from the disk as well as disable the replication.
One of the new features of the newer variants is the addition of a persistence mechanism that leverages a cron job to launch the malware every 30 minutes.Additionally, there now exists a secondary method that retrieves a copy of the malware binary from a peer and executes should it be deleted or the main process is terminated.
P2PInfect further overwrites existing SSH authorized_keys files with an attacker-controlled SSH key, effectively preventing existing users from logging in over SSH.
“The main payload also iterates through all users on the system and attempts to change their user passwords to a string prefixed by Pa_ and followed by 7 alphanumeric characters (e.g. Pa_13HKlak),” Muir said. This step, however, requires that the malware has root access.
Level-Up SaaS Security: A Comprehensive Guide to ITDR and SSPM
Stay ahead with actionable insights on how ITDR identifies and mitigates threats. Learn about the indispensable role of SSPM in ensuring your identity remains unbreachable.
Despite the growing sophistication of the malware, P2PInfect’s exact goals are unclear. Cado Security said it observed the malware attempting to fetch a crypto miner payload, but there is no evidence of cryptomining to date.
“It’s clear that P2PInfect’s developers are committed to maintaining and iterating on the functionality of their malicious payloads, while simultaneously scaling the botnet across continents and cloud providers at a rapid rate,” Muir said.
“It is expected that those behind the botnet are either waiting to implement additional functionality in the miner payload, or are intending to sell access to the botnet to other individuals or groups.”