An active malware campaign targeting Latin America is dispensing a new variant of a banking trojan called BBTok, particularly users in Brazil and Mexico.
“The BBTok banker has a dedicated functionality that replicates the interfaces of more than 40 Mexican and Brazilian banks, and tricks the victims into entering its 2FA code to their bank accounts or into entering their payment card number,” Check Point said in research published this week.
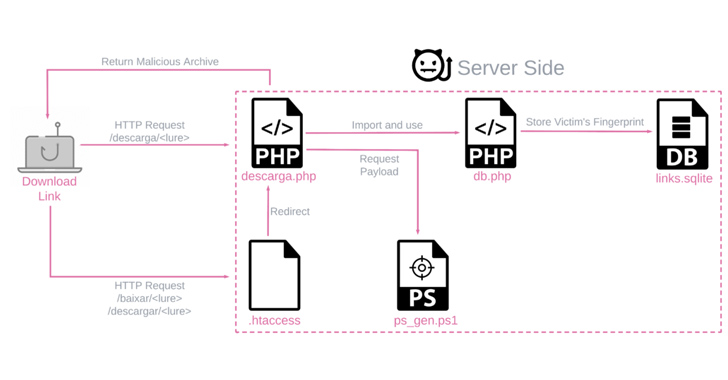
The payloads are generated by a custom server-side PowerShell script and are unique for each victim based on the operating system and country, while being delivered via phishing emails that leverage a variety of file types.
BBTok is a Windows-based banking malware that first surfaced in 2020. It’s equipped with features that run the typical trojan gamut, allowing it to enumerate and kill processes, issue remote commands, manipulate keyboard, and serve fake login pages for banks operating in the two countries.
The attack chains themselves are fairly straightforward, employing bogus links or ZIP file attachments to stealthily deploy the banker retrieved from a remote server (216.250.251[.]196) while displaying a decoy document to the victim.

But they are also diversified for both Windows 7 and Windows 10 systems, mainly taking steps to evade newly implemented detection mechanisms such as Antimalware Scan Interface (AMSI) that allows for scanning the machine for any threats.
Two other key methods to fly under the radar are the use of living-off-the-land binaries (LOLBins) and geofencing checks to ensure that the targets are only from Brazil or Mexico before serving the malware via the PowerShell script.
Once launched, BBTok establishes connections with a remote server to receive commands to simulate the security verification pages for various banks.
In impersonating the interfaces of Latin American banks, the goal is to harvest credential and authentication information entered by the users to conduct account takeovers of the online bank accounts.
“What’s notable is the operator’s cautious approach: all banking activities are only executed upon direct command from its C2 server, and are not automatically carried out on every infected system,” the company said.
Check Point’s analysis of the malware has revealed a significant improvement to its obfuscation and targeting since 2020, expanding beyond Mexican banks. The presence of Spanish and Portuguese language in the source code as well as in phishing emails offers a hint as to the attackers’ origin.
More than 150 users are estimated to have been infected by BBTok, based on an SQLite database found in the server hosting the payload generation component that records access to the malicious application.
The targeting and the language points to the threat actors likely operating out of Brazil, which continues to be the epicenter of potent financially-focused malware.
AI vs. AI: Harnessing AI Defenses Against AI-Powered Risks
Ready to tackle new AI-driven cybersecurity challenges? Join our insightful webinar with Zscaler to address the growing threat of generative AI in cybersecurity.
“Although BBTok has been able to remain under the radar due to its elusive techniques and targeting victims only in Mexico and Brazil, it’s evident that it is still actively deployed,” Check Point said.
“Due to its many capabilities, and its unique and creative delivery method involving LNK files, SMB and MSBuild, it still poses a danger to organizations and individuals in the region.”
The development comes as the Israeli cybersecurity company detailed a new large-scale phishing campaign that recently targeted over 40 prominent companies across multiple industries in Colombia with an ultimate aim to deploy the Remcos RAT via a multi-stage infection sequence.
“Remcos, a sophisticated ‘Swiss Army Knife’ RAT, grants attackers full control over the infected computer and can be used in a variety of attacks. Common consequences of a Remcos infection include data theft, follow-up infections, and account takeover,” Check Point said.