An updated version of a sophisticated backdoor framework called MATA has been used in attacks aimed at over a dozen Eastern European companies in the oil and gas sector and defense industry as part of a cyber espionage operation that took place between August 2022 and May 2023.
“The actors behind the attack used spear-phishing mails to target several victims, some were infected with Windows executable malware by downloading files through an internet browser,” Kaspersky said in a new exhaustive report published this week.
“Each phishing document contains an external link to fetch a remote page containing a CVE-2021-26411 exploit.”
CVE-2021-26411 (CVSS score: 8.8) refers to a memory corruption vulnerability in Internet Explorer that could be triggered to execute arbitrary code by tricking a victim into visiting a specially crafted site. It was previously exploited by the Lazarus Group in early 2021 to target security researchers.
The cross-platform MATA framework was first documented by the Russian cybersecurity company in July 2020, linking it to the prolific North Korean state-sponsored crew in attacks targeting various sectors in Poland, Germany, Turkey, Korea, Japan, and India since April 2018.
The use of a revamped version of MATA to strike defense contractors was previously disclosed by Kaspersky in July 2023, although attribution to the Lazarus Group remains tenuous at best due to the presence of techniques used by Five Eyes APT actors such as Purple Lambert, Magenta Lambert, and Green Lambert.
That said, a majority of the malicious Microsoft Word documents created by the attackers feature a Korean font called Malgun Gothic, suggesting that the developer is either familiar with Korean or works in a Korean environment.
Russian cybersecurity company Positive Technologies, which shared details of the same framework late last month, is tracking the operators under the moniker Dark River.
“The group’s main tool, the MataDoor backdoor, has a modular architecture, with a complex, thoroughly designed system of network transports and flexible options for communication between the backdoor operator and an infected machine,” security researchers Denis Kuvshinov and Maxim Andreev said.
“The code analysis suggests that the developers invested considerable resources into the tool.”
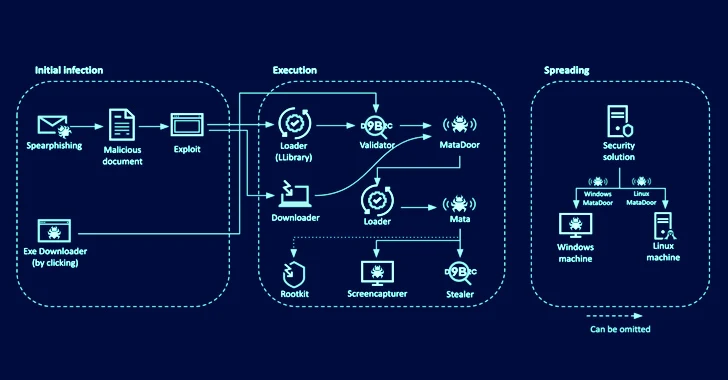
The latest attack chains begin with the actor sending spear-phishing documents to targets, in some cases by impersonating legitimate employees, indicating prior reconnaissance and extensive preparation. These documents include a link to an HTML page that embeds an exploit for CVE-2021-26411.
A successful compromise leads to the execution of a loader that, in turn, retrieves a Validator module from a remote server to send system information and download and upload files to and from the command-and-control (C2) server.
The Validator is also designed to fetch MataDoor, which, according to Kasperksy, is MATA generation 4 that’s equipped to run a wide range of commands capable of gathering sensitive information from compromised systems.
The attacks are further characterized by the use of stealer malware to capture content from clipboard, record keystrokes, take screenshots, and siphon passwords and cookies from the Windows Credential Manager and Internet Explorer.
Another noteworthy tool is a USB propagation module that allows for sending commands to the infected system via removable media, likely enabling the threat actors to infiltrate air-gapped networks. Also employed is an exploit called CallbackHell to elevate privileges and bypass endpoint security products so as to achieve their goals without attracting attention.
Kaspersky said it also discovered a new MATA variant, dubbed MATA generation 5 or MATAv5, that’s “completely rewritten from scratch” and “exhibits an advanced and complex architecture making use of loadable and embedded modules and plugins.”
“The malware leverages inter-process communication (IPC) channels internally and employs a diverse range of commands, enabling it to establish proxy chains across various protocols – also within the victim’s environment,” the company added.
In total, the MATA framework and its cocktail of plugins incorporate support for over 100 commands pertaining to information gathering, event monitoring, process management, file management, network reconnaissance, and proxy functionality.
“The actor demonstrated high capabilities of navigating through and leveraging security solutions deployed in the victim’s environment,” Kaspersky said.
“Attackers used many techniques to hide their activity: rootkits and vulnerable drivers, disguising files as legitimate applications, using ports open for communication between applications, multi-level encryption of files and network activity of malware, [and] setting long wait times between connections to control servers.”